If you're a SaaS company trying to close enterprise deals, you've probably heard this question more than once: "Do you have SOC 2?" And if you don't, the conversation usually stops right there.
SOC 2 certification has become the baseline security standard for B2B software companies. It's not optional anymore if you want to work with enterprise clients, handle sensitive data, or compete in regulated industries. But here's the problem: traditional SOC 2 compliance takes 3-6 months of manual work, costs $50,000-$100,000 in consulting fees, and requires dedicated internal resources most startups don't have.
We built Comp AI specifically to solve this problem. Our AI-powered compliance platform can get you audit-ready in 24 hours (not months), with 90%+ automation replacing manual evidence collection. Instead of hiring expensive consultants, you get white-glove support from our team and a platform that actually understands your infrastructure.
This guide covers everything you need to know about SOC 2 compliance requirements in 2025, from the five Trust Services Criteria to the specific evidence auditors demand, plus a realistic timeline for companies using modern automation.
What is SOC 2 Compliance and Why Does it Matter?
SOC 2 (System and Organization Controls 2) is an auditing framework developed by the American Institute of CPAs (AICPA) that evaluates how well a service organization manages customer data based on five Trust Services Criteria: Security, Availability, Processing Integrity, Confidentiality, and Privacy.
Unlike SOC 1 (which focuses on financial reporting controls), SOC 2 is specifically designed for technology and cloud computing companies that store or process customer data. It's become the de facto security certification for SaaS companies because it proves to potential customers that you have proper controls in place to protect their information.
SOC 2 Type 1 vs Type 2: Which Audit Do You Need?
There are two types of SOC 2 audits, and understanding the difference is critical:
| Feature | SOC 2 Type I | SOC 2 Type II |
|---|---|---|
| Definition | Point-in-time assessment | Operational audit over time |
| Timeline | Ready in weeks (24 hours with Comp AI) | 3-6 month observation period required |
| Observation Period | None (snapshot on specific date) | Minimum 3 months, typically 6 months |
| What's Tested | Controls are properly designed and implemented | Controls operate effectively throughout period |
| Cost | Lower ($15k-$25k typically) | Higher ($25k-$40k+ typically) |
| Best For | Fast certification needs, initial validation | Enterprise customers, long-term trust |
SOC 2 Type I is a point-in-time assessment. An auditor examines whether your security controls are properly designed and implemented on a specific date. Think of it as a snapshot. It's faster to achieve (you can be ready in weeks with automation) and it costs less, but it doesn't prove your controls work over time.
SOC 2 Type II is an operational audit that spans a minimum of three months (though six months is more common). The auditor tests whether your controls operate effectively throughout that entire observation period. It's more rigorous, takes longer, and costs more, but it's also what most enterprise customers actually require.
Here's what this means in practice: If you implement security controls today, you can technically get a Type I audit tomorrow. But for Type II, you need to wait at least three months while those controls operate, and the auditor will test them throughout that period to ensure they're working consistently. Understanding SOC 2 Type 1 vs Type 2 requirements helps you choose the right path for your business.
With Comp AI, we can get you Type I ready in 24 hours and Type II ready in 14 days (plus the mandatory observation period). Our platform continuously collects evidence in the background, so when your observation period ends, you already have everything the auditor needs.
What Are the Five Trust Services Criteria for SOC 2?
Every SOC 2 audit evaluates your organization against the Trust Services Criteria (TSC), which are managed by the AICPA. There are five criteria total, but only one is mandatory:
1. Security (Mandatory for All SOC 2 Audits)
Security is the only required criterion for SOC 2 compliance. It focuses on protecting your system against unauthorized access, both physical and logical. This isn't just about preventing hackers; it's about demonstrating that you have comprehensive controls across your entire technology stack.
The Security criterion breaks down into several Common Criteria (labeled CC1 through CC9 in the AICPA framework):
| Criterion | Focus Area | Key Requirements | Comp AI Automation Level |
|---|---|---|---|
| CC1 | Control Environment | Organizational charts, job descriptions with security responsibilities, background checks, management commitment evidence | 85% automated |
| CC2 | Communication & Information | Document communication channels, security incident reporting, employee training records, vendor security requirements | 90% automated |
| CC3 | Risk Assessment | , internal/external threat analysis, risk treatment plans | 95% automated |
| CC4 | Monitoring Activities | , log reviews, anomaly investigation, corrective actions | 100% automated |
| CC5 | Control Activities | , , SDLC controls, physical security | 90% automated |
| CC6 | Access Controls | Authentication mechanisms, authorization matrices, user provisioning/deprovisioning, privileged access management | 100% automated |
| CC7 | System Operations | Capacity planning, , vulnerability management, | 95% automated |
| CC8 | Change Management | SDLC documentation, testing procedures, change approval workflows, rollback procedures | 90% automated |
| CC9 | Risk Mitigation | , incident handling, , vulnerability tracking | 90% automated |
⚠️ CRITICAL COMPLIANCE REQUIREMENT: Most companies fail their first SOC 2 attempt because they don't have proper evidence for these Common Criteria. They have some controls in place, but they can't prove those controls work. Comp AI solves this by automatically collecting evidence for all nine Common Criteria continuously, so you're never scrambling to find proof when the auditor asks.
2. Availability (Optional)
Availability focuses on whether your system is operational and accessible as committed or agreed. If you have uptime SLAs in your customer contracts, auditors will expect you to include this criterion.
You'll need to demonstrate:
- Monitoring of system performance and availability
- Incident response procedures for outages
- Disaster recovery and business continuity plans
- Evidence that you actually meet your uptime commitments
This means collecting uptime metrics, documenting incident response activities, testing your backup and recovery procedures, and showing that you have redundancy where you've promised it.
3. Processing Integrity (Optional)
Processing Integrity addresses whether your system processes data completely, accurately, timely, and authorized. This is particularly relevant for companies that process financial transactions, healthcare data, or any application where data accuracy is critical.
Auditors will look for input validation controls, error detection and correction procedures, reconciliation processes, and monitoring of processing errors. You need to prove that data doesn't get lost, corrupted, or processed incorrectly as it moves through your systems.
4. Confidentiality (Optional)
Confidentiality is about protecting information designated as confidential (beyond just general data security). This applies if you handle trade secrets, proprietary business information, or any data that's specifically classified as confidential in your customer agreements.
Controls include data classification policies, encryption for confidential data at rest and in transit, access restrictions based on data sensitivity, and procedures for securely disposing of confidential information. This goes beyond the Security criterion by focusing specifically on information that has heightened sensitivity.
5. Privacy (Optional)
Privacy addresses how you collect, use, retain, disclose, and dispose of personal information. If you process personal data (especially for European customers subject to GDPR or California residents subject to CCPA), you should include this criterion.
You'll need privacy notices that clearly explain your data practices, consent mechanisms for data collection, processes for handling data subject rights requests (access, deletion, portability), vendor agreements that address privacy requirements, and evidence of data retention and disposal procedures.
What System Description Requirements Do Auditors Expect?
One of the most overlooked aspects of SOC 2 compliance is the System Description requirement. According to DC-200 criteria from the AICPA, your System Description must document:
The type of services provided
This isn't just "we're a SaaS platform." You need to describe the specific services covered by your SOC 2 scope, what they do, and how they process customer data.
Principal service commitments and system requirements (PSC/SR)
These are the specific commitments you've made to customers regarding security, availability, processing integrity, confidentiality, or privacy. If your contracts promise 99.9% uptime, that's a principal service commitment. If you've told customers their data is encrypted at rest, that's a system requirement.
The components of the system
This includes your infrastructure (cloud providers, data centers), software (both internally developed and third-party applications), people (organizational structure and responsibilities), procedures (documented processes for operations and security), and data (types of information processed and data flows).
Complementary User Entity Controls (CUECs)
These are controls that customers need to implement on their end for the system to be secure. For example, if you provide a platform but customers are responsible for configuring their own access controls, that's a CUEC. You need to document these clearly because you're essentially saying "our controls work, but only if the customer does their part."
Complementary Subservice Organization Controls (CSOCs)
If you rely on third-party vendors (like AWS, Google Cloud, or specialized security services), you need to describe what controls they're responsible for versus what you're responsible for. There are two approaches here:
Carve-out method: You explicitly exclude the subservice organization's controls from your SOC 2 scope. You document that AWS (for example) is responsible for physical security of data centers, and you reference AWS's own SOC 2 report. This is simpler but means your customers need to review multiple SOC 2 reports.
Inclusive method: You take responsibility for monitoring and evaluating your subservice organization's controls. You include their controls in your scope and provide evidence that you're actively managing that third-party risk. This is more comprehensive but requires more ongoing work.
Most companies use the carve-out method for infrastructure providers (AWS, Azure, GCP) and the inclusive method for specialized service providers that are more tightly integrated into their operations.
Comp AI automatically generates your System Description based on your actual infrastructure and cloud integrations. We map your architecture, identify your principal service commitments from your customer contracts, and generate the documentation auditors expect, all without you having to write a single word.
What Evidence Do Auditors Actually Require for SOC 2?
Here's the reality of SOC 2 audits: auditors aren't just checking that you have policies. They're verifying that you have evidence those policies are followed consistently. For every control, you need to provide artifacts that prove the control operated effectively throughout the observation period (for Type II audits).
Types of Evidence Auditors Request

Access Control Evidence
You'll need to provide:
- User access reviews (quarterly is standard)
- Screenshots or exports showing who has access to what systems
- Evidence of user provisioning and deprovisioning (tickets, approval workflows, logs)
- Multi-factor authentication enforcement proof
- Privileged access management logs
Change Management Evidence
Auditors want to see:
- Change request tickets with approval workflows
- Evidence of testing before production deployment
- Deployment logs showing who made changes and when
- Documentation of rollback procedures
- Evidence that emergency changes are properly documented after the fact
Monitoring and Logging Evidence
You need:
- Centralized logging infrastructure (SIEM or log aggregation)
- Evidence that logs are reviewed regularly (not just collected)
- Security alerting configurations
- Incident response documentation for any security events
- Proof that logs are retained for the required period (typically one year)
Vendor Management Evidence
This includes:
- Your vendor inventory with risk classifications
- Vendor assessment questionnaires or third-party SOC 2 reports
- Vendor contracts that include security and data protection requirements
- Evidence of ongoing vendor monitoring
- Procedures for offboarding vendors and ensuring data deletion
Training and Awareness Evidence
You need:
- Security awareness training records showing who completed training and when
- Acknowledgment receipts for security policies
- Phishing simulation results (if you run them)
- Evidence that training happens for new hires and annually for existing employees
Physical Security Evidence
For any locations where you process customer data, you'll need:
- Visitor logs
- Access badge reports
- Surveillance system documentation
- Environmental controls documentation (if you operate your own data centers)
Backup and Recovery Evidence
Auditors expect:
- Backup schedules and evidence of execution
- Restoration testing documentation (you need to prove backups actually work)
- Disaster recovery plan documentation
- Evidence that backups are stored securely and separately from production systems
The traditional approach is to gather all this evidence manually every quarter, which takes hundreds of hours. Comp AI continuously collects evidence automatically from your actual infrastructure through API integrations with AWS, Google Cloud, Azure, GitHub, your HRIS system, and 50+ other platforms. When the auditor asks for evidence, you already have it.
How Long Does SOC 2 Compliance Actually Take in 2025?
Let's talk about real numbers. The SOC 2 industry has a reputation for being expensive and time-consuming, and for good reason.
Traditional SOC 2 Timeline
| Phase | Traditional Approach | With Comp AI |
|---|---|---|
| Readiness Assessment | Months 1-2: Evaluate gaps, create remediation plan | Day 1: Comp AI AI analyzes environment, identifies gaps automatically |
| Remediation | Months 3-4: Implement controls, document policies | Days 2-7: Comp AI platform implements missing controls with AI guidance |
| Pre-Audit | Month 5: Preliminary review, fix remaining issues | Days 8-14: AI validates evidence, identifies gaps |
| Formal Audit | Month 6: Auditor review, report issuance | Days 15+: Audit-ready, observation period begins |
| Total Timeline | 6-9 months from start to certification | 24 hours (Type I) or 14 days + observation (Type II) |
| Cost | $50,000-$100,000 (consulting + audit + tools) | $3,000-$8,000 (platform + audit included) |
With manual processes and traditional consulting firms:
Months 1-2 (Readiness Assessment): A consulting firm evaluates your current state, identifies gaps, and creates a remediation plan. You're paying for their time but haven't made any actual progress yet.
Months 3-4 (Remediation): You implement the recommended controls, document policies and procedures, and set up evidence collection processes. This is the period where internal teams are pulled away from product work to focus on compliance.
Month 5 (Pre-Audit): The auditor performs a preliminary review to identify any remaining issues before the formal audit starts. If they find gaps, you need to fix them before proceeding.
Month 6 (Formal Audit): The auditor examines your controls, reviews evidence, interviews team members, and issues your SOC 2 report.
Total Traditional Timeline: 6-9 months from start to certification, with $50,000-$100,000 in costs (consulting fees plus auditor fees). And that's assuming everything goes well. Many companies fail their first audit and have to restart the clock.
The Automation Advantage
Modern compliance automation platforms can compress this timeline dramatically. With Comp AI:
Day 1 (Onboarding): You connect your cloud infrastructure, HR system, and key SaaS applications through our API integrations. Our AI agent analyzes your environment and automatically maps your controls.
Days 2-7 (Control Implementation): Our platform identifies gaps and generates the specific policies and procedures you need (not generic templates). You implement missing controls with guidance from our team.
Days 8-14 (Evidence Collection): Comp AI begins continuously collecting evidence in the background. Unlike manual processes where you gather evidence quarterly, our platform captures proof that controls are operating every single day.
Days 15+ (Observation Period): For Type II audits, you still need the mandatory 3-6 month observation period (there's no way to accelerate this; it's required by the standard). But Comp AI is collecting evidence automatically throughout this entire period, so you're not scrambling when the auditor shows up.
Total Timeline with Comp AI: 24 hours to audit-ready status for Type I, or 14 days plus the observation period for Type II. Cost ranges from $3,000-$8,000 (versus $50,000-$100,000 with traditional consulting). Use our SOC2 timeline calculator to estimate your specific timeline, or check our SOC2 cost estimator for pricing based on your company size.
The key difference: we automate 90%+ of the work that consulting firms charge you for. Instead of junior consultants manually collecting evidence and filling out spreadsheets, our AI agent does it continuously and automatically.
Why Do Most Companies Fail Their First SOC 2 Audit?
Most companies don't pass their SOC 2 audit on the first attempt. Here are the six most common reasons why, based on hundreds of failed audits we've analyzed:
Failure Mode 1: Incomplete Evidence
🔴 CRITICAL FAILURE PATTERN: You have controls in place, but you can't prove they operated throughout the observation period.
This happens when companies start collecting evidence too late, don't have automated logging, or simply forget to document certain activities.
For example, you have a policy that says user access is reviewed quarterly. But when the auditor asks for evidence, you can only find one access review from six months ago. The policy exists, but the evidence doesn't support that it operates as described.
Failure Mode 2: Scope Creep
You define your SOC 2 scope too broadly and include systems or services that aren't fully ready for audit. Or you define it too narrowly and exclude systems that actually process customer data, which causes the auditor to flag incomplete coverage.
The right scope includes all systems that store, process, or transmit customer data, but nothing more. Comp AI automatically maps your data flows and recommends the appropriate scope based on your actual architecture. If you're unsure where to start, our SOC2 readiness assessment helps identify your current gaps.
Failure Mode 3: System Description Misalignment
Your System Description (the document that defines what you're committing to) doesn't match what you actually do. You say you have 24/7 monitoring, but your monitoring tools are only checked during business hours. You claim data is encrypted at rest, but some legacy databases aren't encrypted.
Auditors will test whether your actual practices match your documented commitments. Any mismatch is a finding.
Failure Mode 4: Vendor Management Gaps
You rely on third-party vendors for critical services, but you haven't properly evaluated their security posture, you don't have contracts with appropriate data protection clauses, or you can't produce their SOC 2 reports.
This is especially problematic for companies using many SaaS tools. If your development team uses dozens of services (GitHub, Slack, monitoring tools, analytics platforms), you need evidence that you've assessed each one and they meet your security requirements.
Failure Mode 5: Control Design Flaws
Your controls are designed in a way that doesn't actually address the risk. For example, you have a change management process, but it allows developers to push directly to production without approval (which defeats the purpose of change management).
Or you have password policies, but they're not actually enforced at the technical level, so users can set weak passwords despite what your policy document says.
Failure Mode 6: Inconsistent Documentation
Different documents contradict each other. Your security policy says one thing, your System Description says something else, and your actual implementation does a third thing. Auditors flag these inconsistencies because they suggest you're not actually following your documented processes.
Comp AI eliminates most of these failure modes by maintaining a single source of truth. Our platform generates your documentation based on your actual infrastructure, collects evidence continuously, and validates that your controls are operating consistently before you ever talk to an auditor.
How Do AI and LLM Systems Affect SOC 2 Compliance?
If you're building with AI or large language models, SOC 2 audits in 2025 require additional considerations that didn't exist two years ago. Auditors are increasingly asking about AI-specific risks, and you need to have good answers.
Model Training Data Controls
If you train or fine-tune models on customer data, auditors will want to know how you prevent data leakage. Do you have processes to ensure customer data doesn't end up in your training corpus? Can you demonstrate that model outputs don't inadvertently expose other customers' information? Are you tracking data lineage from raw input through model training to production inference?
Third-Party AI Service Risks
If you're using OpenAI, Anthropic, Google's AI services, or other third-party AI providers, you need to evaluate them as subservice organizations. What data are you sending to them? How are they protecting it? Do they have SOC 2 certifications? Can you demonstrate that customer data isn't being used to train their models?
Most AI providers now offer enterprise agreements with stricter data handling commitments, but you need to document that you've reviewed and accepted their terms, and that you're monitoring compliance with those terms.
Prompt Injection and Output Validation
Auditors increasingly understand that AI systems introduce new attack vectors. If users can interact with your AI system through prompts, how are you preventing prompt injection attacks? If your AI generates content or code, how are you validating that output before it affects customer data or systems?
This might mean implementing output validation controls, monitoring AI system logs for anomalous behavior, and demonstrating that you've considered AI-specific threats in your risk assessment.
Explainability and Audit Trails
For AI systems that make automated decisions affecting customers, auditors may ask how you maintain audit trails and explainability. Can you explain why your AI system made a particular decision? Do you log enough information to investigate when something goes wrong?
Comp AI itself is built with these considerations in mind. Our AI agent that automates compliance tasks operates with full audit logging, explainable decision-making, and validation of all automated outputs. We practice what we preach.
What's Your 30-60-90 Day Path to SOC 2 Compliance?
Here's a realistic execution plan for achieving SOC 2 compliance, assuming you're using automation rather than doing everything manually.
Days 1-30: Foundation and Quick Wins
Week 1: Connect Your Infrastructure
- Connect Comp AI to cloud providers (AWS, Azure, GCP)
- Integrate source control (GitHub, GitLab, Bitbucket)
- Connect HR system for employee lifecycle evidence
- Link key SaaS applications (Slack, Okta, monitoring tools)
- Document your scope (which services, which Trust Services Criteria)
Week 2: Address Critical Gaps
- Review control gaps identified by Comp AI
- Enable multi-factor authentication everywhere
- Implement centralized logging and monitoring
- Set up automated backup verification
- Document incident response procedures
Week 3: Implement Policies and Procedures
- Review auto-generated policies from Comp AI
- Get stakeholder approval on security policies
- Customize policies for your specific context
- Officially adopt and distribute to team
- Set up policy acknowledgment tracking
Week 4: Begin Evidence Collection
- Verify evidence is flowing automatically
- Check log collection is working
- Confirm user access reports are generating
- Validate backup testing is documented
- Review first month's evidence completeness
By day 30, you should have all critical controls implemented and evidence collection running automatically.
Days 31-60: Vendor Management and Documentation
Weeks 5-6: Tackle Vendor Management
- Inventory all vendors using Comp AI automation
- Prioritize vendors that process customer data
- Request SOC 2 reports from critical vendors (AWS, Azure, GCP have these)
- Complete risk assessments for key vendors
- Update vendor contracts with security requirements
Weeks 7-8: Finalize System Description
- Review auto-generated System Description from Comp AI
- Verify it accurately reflects your architecture
- Confirm principal service commitments match contracts
- Document complementary controls (CUECs and CSOCs)
- Conduct first documented user access review
By day 60, your vendor management should be complete, your System Description should be finalized, and you should have at least one documented access review.
Days 61-90: Testing and Readiness
Weeks 9-10: Security Testing
- Run penetration test or vulnerability assessment
- Document results in Comp AI
- Track remediation of any findings
- Ensure critical vulnerabilities are addressed
- Prepare evidence of testing for auditor
Weeks 11-12: Business Continuity Testing
- Test backup restoration to verify backups work
- Document the restoration process
- Run tabletop exercise for incident response
- Update disaster recovery procedures based on test
- Complete security awareness training for all employees
Week 13: Pre-Audit Readiness Review
- Use Comp AI gap analysis to identify remaining issues
- Fix any gaps before audit engagement
- Organize all evidence in platform
- Prepare team for auditor interviews
- Schedule audit with pre-vetted auditor
By day 90, you should be genuinely ready for the auditor. If you're pursuing Type I (point-in-time), you can schedule your audit immediately. If you're pursuing Type II, you need to wait out the observation period while Comp AI continues collecting evidence automatically.
How Does Comp AI Accelerate Your SOC 2 Journey?
Traditional compliance consulting is built on a fundamentally broken model: junior consultants spend hundreds of billable hours manually collecting evidence, filling out spreadsheets, and writing documentation. You pay $150-$300 per hour for work that should be automated.
We built Comp AI differently. Our AI agent connects directly to your infrastructure and continuously automates the tedious work through our automated compliance software:
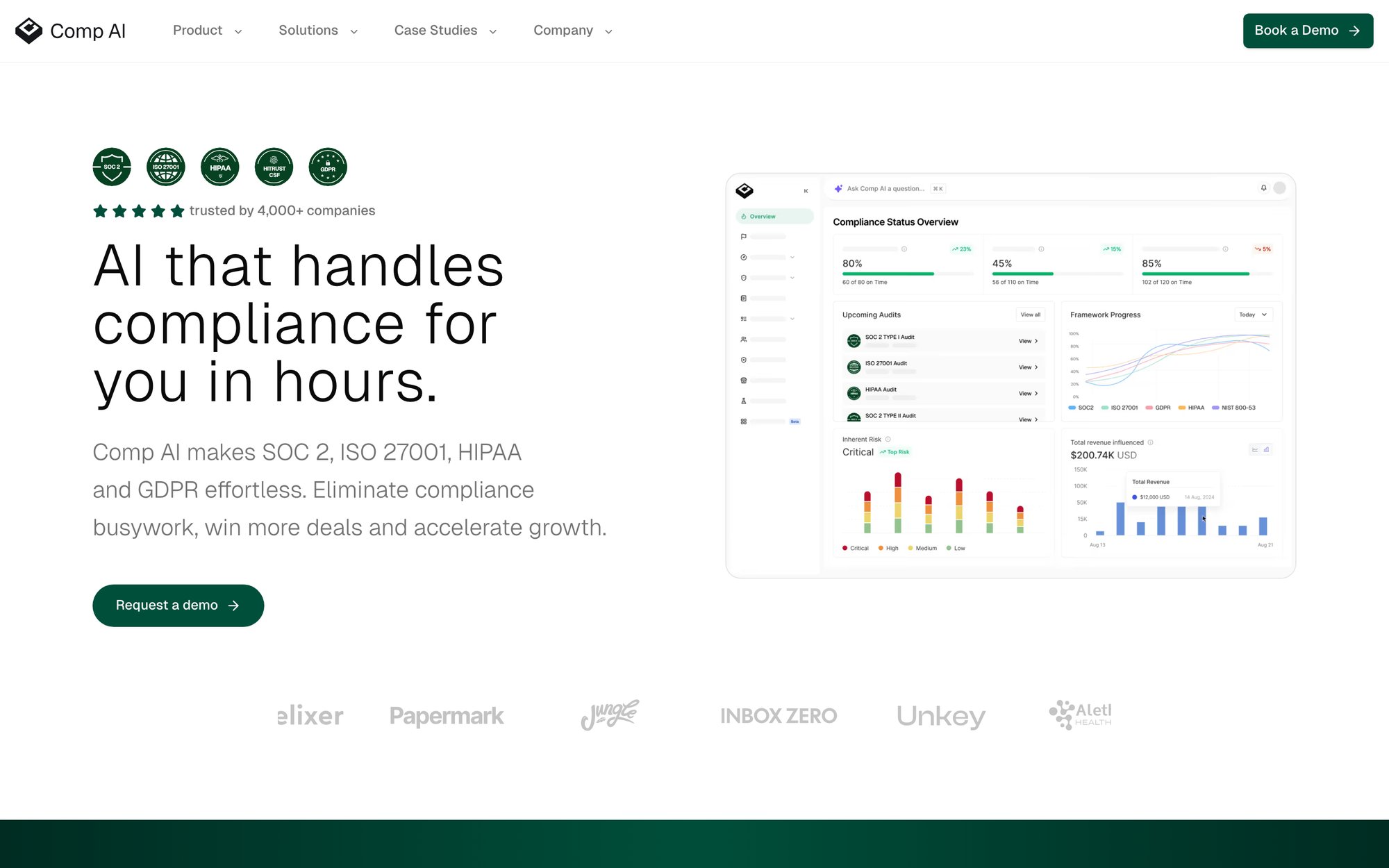
The Comp AI dashboard gives you real-time visibility into your compliance posture across multiple frameworks. Instead of spreadsheets and manual tracking, you see exactly where you stand with automated status updates, upcoming audit timelines, and framework-specific progress tracking (all in one centralized view).
Automated Evidence Collection
We integrate with 50+ platforms (AWS, Azure, GCP, GitHub, your HRIS system, SSO provider, and more) to collect evidence automatically. When the auditor asks for user access reports, change management logs, or backup verification records, you already have them.
Intelligent Control Mapping
Our AI analyzes your infrastructure and automatically maps which controls you have in place and where the gaps are. Instead of spending weeks doing manual assessments, you get a prioritized remediation roadmap on day one.
Dynamic Documentation
Your System Description, policies, and procedures are generated automatically based on your actual infrastructure (not generic templates). When your infrastructure changes, Comp AI updates your documentation automatically so you're never out of sync.
Continuous Monitoring
SOC 2 isn't a one-time event; it's an ongoing commitment. Comp AI monitors your controls continuously and alerts you when something drifts out of compliance so you can fix it before the annual audit.
White-Glove Support
Despite being an automation platform, you're not on your own. Our team of compliance experts provides guidance throughout your journey, reviews your System Description, and helps you prepare for auditor questions.
The result: you can achieve SOC 2 certification in 24 hours for Type I or 14 days plus observation period for Type II, at a fraction of traditional consulting costs ($3,000-$8,000 vs. $50,000-$100,000).
We're so confident in our approach that we offer a money-back guarantee: if you don't pass your SOC 2 audit after using Comp AI, we'll refund your entire subscription and pay for a re-audit.
Frequently Asked Questions
How long does it actually take to get SOC 2 certified?
The timeline depends on your starting point and which type of audit you're pursuing. For SOC 2 Type I (point-in-time audit), you can be ready in as little as 24 hours with Comp AI if you have reasonably mature security practices already in place. More realistically, most companies need 2-4 weeks to implement any missing controls and collect sufficient evidence.
For SOC 2 Type II (operational audit), you need a minimum observation period of three months (though six months is more common) where your controls operate and evidence is collected continuously. The good news: if you're using Comp AI, we're collecting evidence automatically throughout this entire period, so you're not actively working on compliance for those three to six months. You can get audit-ready in 14 days, then wait out the observation period while Comp AI handles evidence collection in the background.
Can I achieve SOC 2 compliance without hiring expensive consultants?
Yes, absolutely. The traditional consulting model exists because manual evidence collection and documentation are incredibly time-consuming. But with modern automation platforms like Comp AI, you can automate 90%+ of that work. Our AI agent handles evidence collection continuously, generates documentation based on your actual infrastructure, and provides guidance on implementing missing controls.
You still need to invest internal resources (someone needs to own the project and make decisions about scope and controls), but you don't need to pay $50,000-$100,000 for consultants to manually gather evidence and fill out spreadsheets. Comp AI costs $3,000-$8,000 and includes white-glove support from our compliance team.
Which Trust Services Criteria should I include in my SOC 2 audit?
Security is mandatory for all SOC 2 audits. Beyond that, it depends on what commitments you've made to customers in your contracts or SLAs:
Include Availability if you have uptime commitments in your SLAs (like 99.9% availability). Most SaaS companies should include this criterion.
Include Processing Integrity if your system processes data where accuracy and completeness are critical (financial transactions, healthcare records, payroll processing). This is less common for general SaaS products but essential if you're in those specific industries.
Include Confidentiality if you handle information that's specifically designated as confidential beyond general customer data. This applies if you process trade secrets, proprietary business information, or data with specific confidentiality obligations in your contracts.
Include Privacy if you process personal information, especially if you serve customers in the European Union (GDPR) or California (CCPA). Many SaaS companies include Privacy as a criterion to demonstrate strong data protection practices.
When in doubt, start with Security and Availability (the most common combination), then add others based on your specific business and customer requirements. Comp AI can help you make this decision based on your actual contracts and service commitments.
Do I need a SOC 2 Type I or Type II audit?
Most enterprise customers require SOC 2 Type II because it proves your controls operate effectively over time, not just that they existed on a specific date. Type II is the gold standard and it's what you should pursue if you're serious about enterprise sales.
SOC 2 Type I is useful in a few specific situations: you need something to show customers quickly while you wait out the observation period for Type II, you're early-stage and Type I is enough to unblock initial enterprise conversations, or you want to validate your readiness before committing to the longer Type II observation period.
If you're deciding between the two, go with Type II. The incremental cost isn't dramatically higher, and you won't need to re-audit as soon when customers start asking for Type II reports (which they inevitably will).
How much does SOC 2 compliance cost?
| Cost Component | Traditional Consulting | With Comp AI |
|---|---|---|
| Readiness Consulting | $20,000-$40,000 | Included (platform cost) |
| Audit Fee (Type II) | $25,000-$40,000 | $15,000-$25,000 (pre-vetted auditors) |
| Tools & Assessments | $5,000-$20,000 | Included (platform cost) |
| Platform/Software | N/A | $3,000-$8,000 annually |
| Total First Year | $50,000-$100,000 | $18,000-$33,000 |
| Annual Renewal | $30,000-$50,000 | $18,000-$25,000 |
Traditional consulting-led SOC 2 programs cost $50,000-$100,000 for the first year, broken down into readiness consulting ($20,000-$40,000), the actual audit ($25,000-$40,000 for Type II), and various tools and assessments ($5,000-$20,000). Annual renewals cost $30,000-$50,000 because you need to re-audit every year.
With automation platforms like Comp AI, the cost structure is completely different: $3,000-$8,000 annually for the platform (which includes continuous evidence collection, automated documentation, and white-glove support), plus the auditor fee ($15,000-$25,000 for Type II audits, though some auditors charge less when working with automation platforms because the evidence is already organized).
Total first-year cost with Comp AI: approximately $18,000-$33,000, which is 60-70% less than traditional consulting. And because Comp AI handles evidence collection continuously, your annual renewal costs stay low.
What's the difference between SOC 2 and ISO 27001?
SOC 2 and ISO 27001 are both security frameworks, but they have different origins, audiences, and approaches:
SOC 2 is an American auditing standard created by the AICPA, primarily focused on how service organizations handle customer data. It's report-based (you get a SOC 2 report to share with customers, not a certificate), it's flexible (you choose which Trust Services Criteria to include beyond Security), and it's especially common in the US SaaS industry.
ISO 27001 is an international standard created by the International Organization for Standardization, focused on information security management systems (ISMS). It's certificate-based (you get certified to the standard), it has a prescribed set of controls you must address, and it's more common in Europe and for companies selling to highly regulated industries.
Many companies pursue both certifications because they serve different markets. If you're primarily selling to US-based SaaS customers, start with SOC 2. If you're selling to European enterprises or highly regulated industries, ISO 27001 may be more valuable. Comp AI supports both frameworks, so you can pursue them simultaneously without duplicating effort. Learn more about the differences between ISO 27001 vs SOC 2 to determine which certification path is right for your business.
How do I maintain SOC 2 compliance after the initial audit?
SOC 2 compliance is an ongoing commitment, not a one-time project. You need to re-audit annually to keep your SOC 2 report current. Between audits, you need to maintain your controls, collect evidence continuously, handle any changes to your infrastructure or team, and address any new risks.
This is where most companies struggle with traditional consulting. You pass your audit, the consultants leave, and a year later you're scrambling to reconstruct evidence for the next audit because you haven't maintained documentation throughout the year.
Comp AI solves this by continuously monitoring your controls and collecting evidence automatically every single day. When it's time for your annual re-audit, you already have all the evidence the auditor needs. We also alert you if anything drifts out of compliance (a critical employee leaves and their access isn't deprovisioned promptly, a security patch isn't applied on schedule, etc.) so you can fix issues before they become audit findings.
Can I get SOC 2 certified if I'm a small startup?
Yes. SOC 2 isn't just for large enterprises. In fact, many startups pursue SOC 2 certification specifically because they're trying to sell to enterprise customers who require it.
The challenge for startups is resource constraints. You probably don't have a dedicated compliance team, and you can't afford to spend $100,000 on traditional consulting. This is exactly why we built Comp AI: to make enterprise-grade compliance accessible to startups without requiring a massive budget or dedicated compliance headcount.
With Comp AI, a startup can achieve SOC 2 compliance with one person spending a few hours per week on the project (mostly reviewing automatically generated documentation and making decisions about scope and controls), rather than needing a full-time compliance manager working for months. Check out our SOC 2 checklist for SaaS startups to see exactly what's required.
What happens if I fail my SOC 2 audit?
If you fail your SOC 2 audit (meaning the auditor issues a qualified or adverse opinion), you need to remediate the findings and re-audit. This means addressing whatever control deficiencies the auditor identified, collecting new evidence, and paying for another audit. The timeline and cost reset, which is why it's critical to get it right the first time.
Common reasons for audit failures include incomplete evidence (you can't prove your controls operated throughout the observation period), control design flaws (your controls don't actually address the risks they're meant to address), and scope issues (your System Description doesn't match your actual operations).
Comp AI dramatically reduces the risk of audit failure by validating your evidence before the auditor sees it and identifying gaps early when they're still easy to fix. We're so confident in our platform that we offer a money-back guarantee: if you don't pass your audit after using Comp AI, we'll refund your entire subscription and pay for your re-audit.
Do I need to be SOC 2 compliant to sell to enterprise customers?
For most B2B SaaS companies: yes, practically speaking. While SOC 2 certification isn't legally required (it's voluntary), it has become the de facto security baseline that enterprise procurement teams expect. Without SOC 2, you'll struggle to get through enterprise security reviews, you'll lose deals to competitors who have SOC 2, and you'll waste months in back-and-forth security questionnaires that go nowhere.
Some large enterprises might accept alternative security frameworks (ISO 27001, NIST Cybersecurity Framework, custom security assessments), but SOC 2 is by far the most widely accepted standard in the US market. If you're serious about enterprise sales, SOC 2 should be a priority.
The good news: with modern automation, getting SOC 2 certified is no longer the massive burden it used to be. Comp AI can get you audit-ready in 24 hours for Type I or 14 days plus observation period for Type II, at a fraction of traditional consulting costs. The ROI is clear when you consider how many enterprise deals you can close with SOC 2 certification in hand. Learn how to get SOC 2 certification with our step-by-step guide.
Can Comp AI help if I'm already working with a consultant?
Yes. Many companies come to Comp AI after spending months with traditional consultants and realizing how much manual work is still required. Our platform complements consulting relationships by automating the tedious evidence collection that consultants typically charge hundreds of hours for.
If you're already working with consultants, Comp AI can take over the evidence collection and continuous monitoring work, allowing your consultants to focus on higher-value strategic guidance. You'll reduce your consulting fees dramatically while maintaining the benefit of expert advice.
Alternatively, many companies switch entirely from consultants to Comp AI because our white-glove support team provides the same expert guidance without the consulting firm markup. We've helped hundreds of companies achieve SOC 2 certification without traditional consultants.
How often do I need to renew my SOC 2 certification?
SOC 2 reports are valid for one year from the end of the observation period. Most companies re-audit annually to keep their reports current, because customers will want to see a recent SOC 2 report (typically no older than 12 months).
The re-audit process is similar to the initial audit but often faster because you already have processes in place and you're just demonstrating that those processes continued to operate effectively. With Comp AI, re-audits are even smoother because we've been collecting evidence continuously throughout the year, so you're not scrambling to reconstruct documentation when it's time for the annual audit.
Budget time and resources for your annual re-audit. It's not as intensive as the initial certification, but it's a recurring commitment that's necessary to maintain your SOC 2 status.
Share this article
Help others discover this content