Getting started with ISO 27001 certification is really about laying a solid foundation for your Information Security Management System (ISMS). It all ends with a formal, third-party audit, but how you begin sets the tone for the entire project. Think of it as a strategic mission to build trust, not just a technical checklist.
Starting Your ISO 27001 Certification Journey
Kicking off the ISO 27001 process can feel massive, but the first few moves you make are the most important. Success doesn't come from trying to boil the ocean; it comes from smart planning and a clear sense of direction right from the get-go.
Your very first job is to define the scope of your ISMS. This isn't just a technical task—it's a critical business decision that determines what parts of your organization you're going to protect.
Defining Your ISMS Scope
Defining your scope is all about drawing a clear boundary around the information and assets that need protection. You’re essentially answering a few core questions:
- Which business units are we including? Is it just the engineering team, or are we looping in HR, finance, and customer support?
- What physical locations are covered? Does this apply to just our main office, or does it include our remote hubs and data centers?
- Which specific assets are in play? This means listing everything from servers and employee laptops to cloud services and key software.
Getting the scope right prevents "scope creep" later on and keeps your team focused. For instance, a fintech startup might decide to scope its ISMS to only cover the core payment processing platform and its direct support teams. They might leave corporate IT out of the initial certification just to keep things manageable and get certified faster.
Conducting a Practical Gap Analysis
With your scope locked in, it's time for a gap analysis. This is where you measure your current security reality against what the ISO 27001 standard requires. It's like dropping a pin on a map that shows you exactly how far you have to go.
The analysis will uncover things like missing policies, undocumented procedures, or glaring technical vulnerabilities. It’s the moment you stop guessing and start building a real plan.
A good gap analysis turns ambiguity into an actionable roadmap. You're no longer speculating about security weaknesses; you're systematically addressing them with a data-driven plan.
This step is absolutely crucial for creating a realistic project timeline and getting the leadership team on board. It gives everyone a clear-eyed view of the time, effort, and resources you'll need.
The demand for this kind of verified security is exploding. There are over 70,000 ISO 27001 certificates issued across nearly 150 countries, and that number is only growing. A thorough gap analysis is your first real step toward joining that group. To better understand the investment, check out this comprehensive cost breakdown from Rhymetec. And if you need to build a stronger case internally, outlining the benefits of ISO 27001 certification can make all the difference.
To help you get organized, here’s a quick checklist that covers the essential first steps for launching your certification process.
ISO 27001 Kick-Off Checklist
| Phase | Key Objective | Critical Action Item | Common Pitfall |
|---|---|---|---|
| Project Initiation | Secure management buy-in and resources. | Develop a business case linking ISO 27001 to company goals. | Treating it as a purely IT project without executive sponsorship. |
| Scope Definition | Clearly define the boundaries of the ISMS. | Document included locations, business units, assets, and technologies. | Making the scope too broad (boiling the ocean) or too narrow (missing key risks). |
| Gap Analysis | Identify the delta between current controls and ISO 27001 requirements. | Conduct a detailed assessment against Annex A controls and clauses 4-10. | Rushing the analysis and underestimating the work required to close gaps. |
| Team Assembly | Form a cross-functional team to lead the project. | Appoint a project manager and assign roles to members from IT, HR, and legal. | Lacking representation from key departments, leading to implementation roadblocks. |
Following these initial steps methodically ensures you're not just starting a project, but building a sustainable security program that adds real value to your business.
Mastering Risk Assessment and Treatment
Let's get to the real core of ISO 27001: the risk assessment. This is where the rubber meets the road. You move from abstract security concepts to pinpointing the actual dangers lurking around your company's information. Think of it less as a compliance checkbox and more as building a real-world defense strategy against credible threats.
A solid assessment always starts with knowing what you're trying to protect. You need a detailed inventory of your most critical information assets. We're talking about things like customer databases, proprietary source code, financial projections, and intellectual property. Once you have that list, you can start connecting the dots between those assets and specific threats and vulnerabilities.
Identifying and Prioritizing Your Risks
Picture a SaaS company that handles a ton of personally identifiable information (PII). A major threat could be a sophisticated phishing attack, while a key vulnerability might be gaps in employee security training. The risk, then, is the very real possibility of an employee clicking a malicious link, triggering a data breach that exposes thousands of customer records. It's a nightmare scenario.
From there, you have to figure out the business impact of each risk. This means calculating both the likelihood of something happening and the potential damage if it does. This simple exercise is incredibly powerful. It forces you to focus your limited resources on the big, scary stuff—the high-impact, high-likelihood scenarios—instead of getting bogged down by minor issues.
Your risk register isn't just a spreadsheet for your auditor. It's your strategic playbook. It’s a living document that turns vague security worries into concrete business priorities that your leadership team can actually understand and act on.
A strong risk management system is the absolute backbone of ISO 27001 certification. A practical guide to Risk Management Systems can give you a great starting point for building your own Information Security Management System (ISMS). When you get this part right, your entire security program rests on a solid, evidence-based foundation.
Choosing Your Risk Treatment Strategy
Once you've lined up and prioritized your risks, you have to decide what to do about them. This process is called risk treatment, and you've got four main plays you can run.
- Treat: This is your go-to move most of the time. You implement specific security controls from Annex A to knock the risk down to an acceptable level. For our SaaS company example, this would mean rolling out advanced email filtering and launching mandatory, recurring phishing training for the whole team.
- Tolerate: Sometimes, you just accept the risk. This usually happens when the cost of fixing it is way higher than the potential damage. It’s a calculated business decision, but it has to be formally documented and signed off on by management.
- Terminate: In more extreme cases, the smartest move is to eliminate the risk completely by stopping the activity that creates it. This might mean decommissioning an old, vulnerable legacy system that's just too risky to keep online.
- Transfer: You can also offload the risk to someone else. The classic example here is buying a comprehensive cyber insurance policy to cover the financial fallout from a potential data breach.
By systematically working through these options, you create a clear, defensible line between the risks you've identified and the security controls you've put in place. This ensures your ISMS isn't just compliant on paper but is genuinely effective at protecting what matters most. To get a better handle on formalizing this, see how you can build out your own risk management policy.
Building Your Practical ISMS Documentation

Let's be honest, documentation can feel like the most tedious part of getting ISO 27001 certified. But this is where your security strategy gets real. We're not talking about creating dusty binders that sit on a shelf. This is about building a practical, operational playbook for your whole company.
The aim is to create "living documents"—guides that are actually useful, easy to understand, and woven into how people work every day. Think of them less as audit artifacts and more as the instruction manual for your Information Security Management System (ISMS).
Crafting Your Core Documents
Two documents are the absolute bedrock of your ISMS: the Statement of Applicability (SoA) and the Risk Treatment Plan.
The SoA is basically your master list of all 114 Annex A controls. Here, you document which ones apply to your business and, just as importantly, justify why any do not. No skipping allowed.
Your Risk Treatment Plan is the direct result of your risk assessment. It's the action plan. It details exactly how you'll handle each risk you found—whether you decide to treat it, tolerate it, terminate it, or transfer it. This document gives auditors a crystal-clear map from the threats you face to the defenses you’ve put in place.
For instance, an e-commerce company might flag "unauthorized access to customer payment data" as a major risk. Their Risk Treatment Plan would then point to specific controls they're using to fight it, like encryption (A.18.1.4) and strict access control policies (A.9.1.1).
Your documentation can't just state what you do; it has to explain why you do it. A solid policy provides the logic behind your security controls, which makes them easier for your team to follow and for auditors to approve.
Making Policies That People Actually Use
The best security policies are never written in a vacuum. They’re built with input from the people who have to live with them every day.
Get departments like HR, Engineering, and Legal involved. This ensures your documentation is actually relevant and doesn't create pointless roadblocks. An information security policy that’s too technical or rigid will just be ignored. If you want to dive deeper, check out our guide on creating an effective information security policy.
Imagine a media company working on a data classification policy. Instead of some overly-engineered, five-tier system, they collaborated with content creators to build a simple three-level model that made sense for them:
- Public: Marketing materials and press releases.
- Internal: Employee handbooks and project plans.
- Confidential: Unreleased content, source data, and financial records.
This approach made the policy intuitive and easy to follow. Security became part of the content creation process, not some clunky add-on. That’s how you show a real commitment to security—the kind that goes way beyond just passing an audit.
Running Your Internal Audit and Management Review
Think of the internal audit as the final dress rehearsal before the main event. This is your chance to put your Information Security Management System (ISMS) through its paces, find the cracks, and patch them up before an external auditor puts them under a microscope.
This isn't just about ticking boxes on a checklist. A solid internal audit brings a fresh, unbiased perspective to your security controls. The trick is to have it run by people who aren't involved in the day-to-day grind of managing the ISMS—whether that’s an internal team from another department or a third-party expert. Their objective viewpoint is gold for catching issues the implementation team might have missed.
Conducting an Effective Internal Audit
It all starts with a clear audit plan. Lay out the scope, what you're trying to achieve, and the criteria you'll be measuring against. From there, your auditors will start digging for evidence by reviewing documents, interviewing your team, and seeing processes in action. Their job is to make sure what you've written down is actually happening in the real world.
Let's say your access control policy dictates that ex-employee accounts are shut down within 24 hours. An internal auditor will grab a list of terminations from the last few months and check it against your system access logs. Any lag time gets flagged as a finding. It's that simple.
This infographic breaks down the flow from that initial planning all the way to the strategic review.
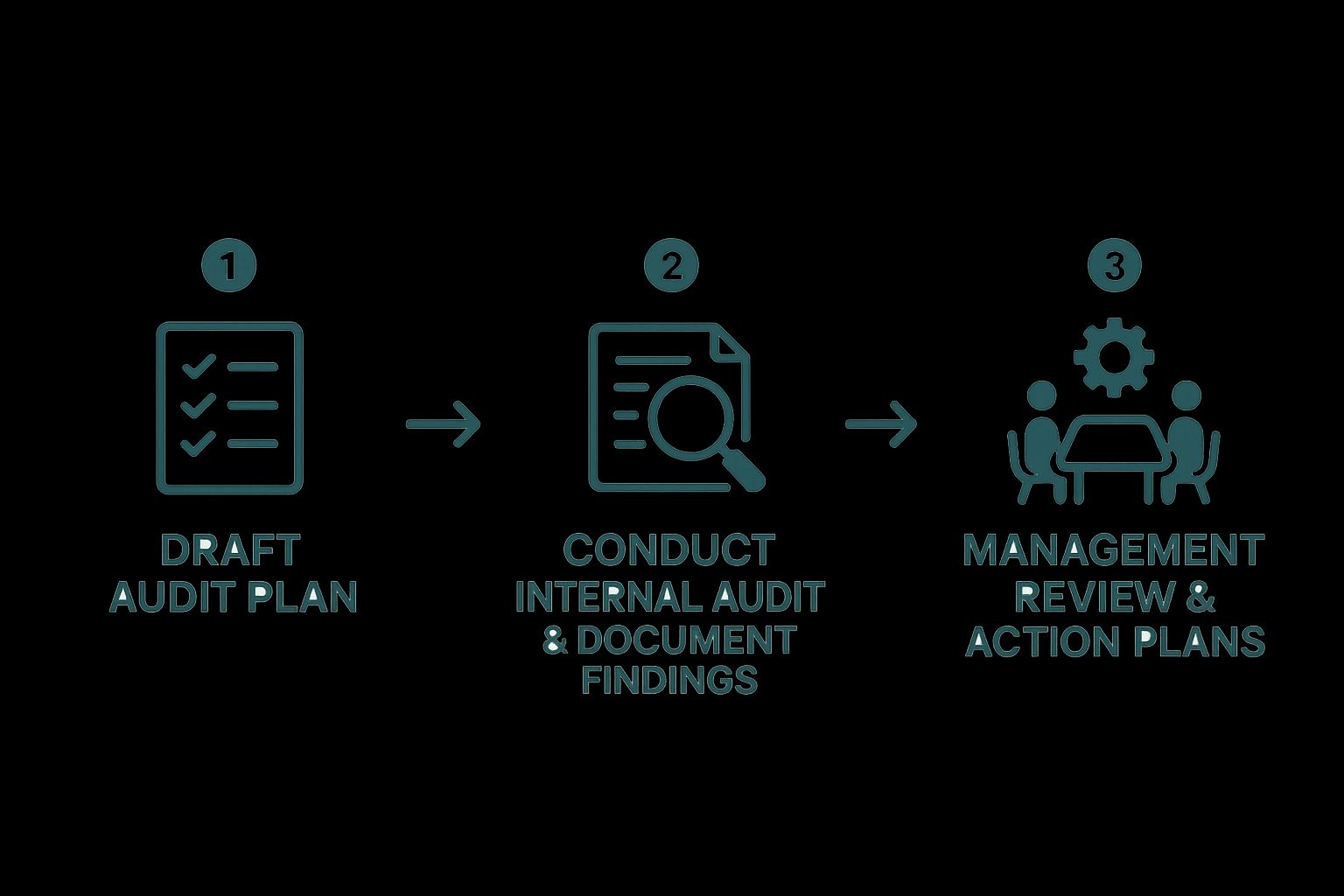
This kind of structured sequence makes sure the management review is backed by hard data from the internal audit, which leads to much smarter action plans.
Documenting everything clearly is non-negotiable. Every finding needs to detail the non-conformity, show the proof, and point to the specific ISO 27001 clause it breaks. This process naturally flows into creating corrective action plans that fix the root cause, not just the surface-level problem. To keep it all straight, it's worth checking out the best audit management software to stay organized.
Leading the Management Review
Once the audit wraps up, it's time for the management review. This is where leadership formally sits down to assess how the ISMS is performing. It’s more than a status update; it's a strategic gut-check to ensure your security efforts still line up with business goals and are actually working.
The Management Review is where audit findings stop being a list of problems and start a strategic conversation about getting better. It’s how you get the continued buy-in and resources to keep your ISMS in fighting shape.
In this meeting, you’ll present the key metrics, the internal audit results, any corrective actions you've taken, and your latest risk assessment. Here's a powerful stat you can use: while countries like Japan, India, and the UK make up about 67% of global ISO certifications, a whopping 75% of companies report compliance issues stemming from poor employee training. Dropping a number like that is a great way to justify more budget for security awareness training.
This meeting is your moment to prove the ISMS isn't just a cost center. It's a critical part of the business that enables growth and protects the bottom line. A successful review locks in leadership support and clears the path for the real deal: the external certification audits.
Navigating the External Certification Audits
<iframe width="100%" style="aspect-ratio: 16 / 9;" src="https://www.youtube.com/embed/K5MyslyaREk" frameborder="0" allow="autoplay; encrypted-media" allowfullscreen></iframe>
This is the final hurdle. After all the internal prep work, it’s time to bring in the pros—an accredited certification body. Their entire job is to give your Information Security Management System (ISMS) a completely objective, third-party once-over.
The whole process is split into two distinct phases. Think of it as a document review followed by a real-world inspection.
The Stage 1 Audit: A Readiness Review
The Stage 1 audit is essentially a high-level look at your ISMS documentation. The auditor’s goal here is simple: confirm that the system you’ve designed on paper meets all the requirements of the ISO 27001 standard. They aren't kicking the tires on your controls just yet; they're just making sure the blueprint is complete and correct.
You’ll need to have your core documentation ready for them to comb through, including:
- The Scope of your ISMS
- Your Information Security Policy
- The Risk Assessment and Treatment Plan
- Your Statement of Applicability (SoA)
- Results from your internal audit and management review
The auditor will flag any major gaps or what they call "non-conformities" in your documentation. This is actually a good thing—it gives you a clear punch list of items to fix before you head into the much more intense second stage.
The Stage 2 Audit: The Deep Dive
Once you’ve tackled any findings from Stage 1, the auditor comes back for the main event: the Stage 2 audit. This is a much deeper examination where they test whether your ISMS is actually working the way you said it would.
Auditors will interview your team, watch processes in action, and ask for hard evidence that your security controls are effective. For instance, if your policy says new hires get security training within their first week, the auditor will want to see the training logs and completion records for your most recent employees.
The Stage 2 audit is where your documented policies meet reality. It's your opportunity to prove that your ISMS isn't just a set of documents, but a living, breathing part of your company culture that actively protects information.
The demand for this kind of certified security is blowing up. The market for ISO 27001 certification software was valued at around USD 1.16 billion and is projected to skyrocket to USD 3.5 billion by 2035, all thanks to growing cybersecurity concerns. You can learn more about the market's growth projections if you're curious. This growth really highlights just how much value companies are placing on getting certified.
Maintaining and Improving Your ISMS After Certification
Getting your ISO 27001 certificate is a huge milestone, but don't pop the champagne just yet. This isn't the finish line; it's the starting gun for a continuous process of security improvement. The real payoff comes from keeping your Information Security Management System (ISMS) sharp and effective long-term.
Your certificate is valid for three years, but it's definitely not a "set it and forget it" deal. To keep that hard-earned certification active, you'll need to pass an annual surveillance audit. Think of these as lighter-touch check-ins compared to the big Stage 2 audit, designed to make sure your ISMS is humming along and you're still committed to getting better.
The Annual Surveillance Audit Cycle
During a surveillance audit, the auditor isn't going to tear everything apart again. Instead, they'll zero in on key areas of your ISMS. They’ll want to see updated documentation, evidence of your ongoing security activities (like internal audits and management reviews), and proof that you’ve fixed any issues they found last time.
This cycle is what prevents your ISMS from collecting dust on a shelf. It forces you to weave security practices into your day-to-day operations, making it business as usual instead of a frantic, one-off project. To pass, you'll need to show you're on top of things like:
- Ongoing Risk Assessments: Your risk register isn't static. You need to be regularly updating it to reflect new threats, different technologies, or changes in how you do business.
- Continuous Monitoring: Keep a close watch on your security controls. Are they still working as intended? Can you prove it?
- Regular Training: Security awareness can't be a one-time event. You should be training new hires as they join and giving everyone an annual refresher to keep security top of mind.
An ISMS is a living system. If it isn't evolving with your business and the threat landscape, it's effectively losing value. The surveillance and recertification cycle ensures your security posture keeps pace with change.
Preparing for Recertification
After three years, it's time for the main event again: a full recertification audit. This one is much more like your initial Stage 2 audit, taking a comprehensive look at your entire ISMS to confirm it still meets the ISO 27001 standard. It's your chance to really show off how much your security posture has matured.
The best way to stay ahead is to get organized. Create a compliance calendar and schedule your recurring activities—internal audits, management reviews, policy updates—well in advance. This turns what could be a chaotic scramble into a manageable, predictable routine, ensuring your ISO 27001 certification delivers real security value for years to come.
Common Questions About the ISO 27001 Certification Process
When you start digging into ISO 27001, a few questions pop up almost immediately. Let's tackle some of the most common ones that teams run into.
How Long Does The Certification Take
This is usually the first thing leadership wants to know. For a small or mid-sized company that already has some security measures in place, you’re typically looking at a 6 to 12 month journey from kickoff to getting that certificate in hand. If you're a larger, more complex organization, it might stretch to 12 or even 18 months.
The biggest factors are your company's size, how broad your ISMS scope is, and where your security maturity is today. Of course, having strong backing from the top and a dedicated team can really put the pedal to the metal.
Is Compliance The Same As Certification
This one trips a lot of people up, but it's a crucial difference. Compliance is an internal thing—it means you're following the rules and have implemented the requirements laid out in the ISO 27001 standard. You’re doing the work.
Certification, on the other hand, is the official stamp of approval from an outside party. It’s the formal, third-party verification by an accredited auditor who comes in, kicks the tires on your ISMS, and confirms you've done everything correctly.
Compliance is what you do. Certification is what you prove. That certificate is the tangible evidence you can show customers and partners that your security claims aren't just talk—they've been independently validated.
Can We Get Certified Without A Consultant
The short answer is yes, it's possible. But—and it's a big but—you absolutely need deep in-house expertise. We're talking about a dedicated project manager who eats, sleeps, and breathes the ISO 27001 standard.
While you might save some money upfront by skipping the consultant, a good one can be worth their weight in gold. They'll help you speed up the process, steer you clear of common mistakes, and share priceless insights from their experience in the audit trenches.
--- Ready to accelerate your ISO 27001 certification and achieve audit readiness in just 14 days? Comp AI blends powerful automation with expert guidance to make compliance effortless. See how our AI-first platform can help you win deals faster and scale securely at https://trycomp.ai.
Share this article
Help others discover this content