8 Key Benefits of ISO 27001 Certification in 2025
Discover the top benefits of ISO 27001 certification. Learn how it enhances security, boosts growth, ensures compliance, and builds customer trust.
- Home
- Compliance HubHub
- 8 Key Benefits of ISO 27001 Certification in 2025
In a data-driven economy, information security is no longer just a technical requirement-it's a core business asset. As organizations navigate increasing cyber threats and strict regulations, ISO 27001 certification has shifted from an optional benchmark to a strategic imperative for growth, resilience, and market leadership. This global standard for Information Security Management Systems (ISMS) offers a proven framework to protect your most sensitive data assets, but its value extends far beyond preventing breaches.
The benefits of ISO 27001 certification are tangible and transformative. Achieving it signals a deep-seated commitment to security that resonates with customers, partners, and regulators, unlocking new revenue opportunities and building lasting trust. Traditionally, the path to certification was a manual, resource-intensive process filled with spreadsheets, evidence gathering, and policy drafting. Modern compliance automation platforms are changing this dynamic, using AI to condense months of work into a streamlined, efficient workflow. This article breaks down the 8 most significant advantages of ISO 27001 and demonstrates how your organization can achieve them faster than ever before. You will learn how to leverage certification not just as a defensive shield, but as a proactive tool for sustainable business success.
1. Enhanced Information Security and Risk Management
At its core, one of the most significant benefits of ISO 27001 certification is its mandate to establish a systematic, proactive approach to managing sensitive company and customer information. This is achieved through the implementation of an Information Security Management System (ISMS), a framework of policies and procedures that includes all legal, physical, and technical controls involved in an organization's information risk management processes. It shifts your security posture from reactive firefighting to a continuous, strategic cycle of evaluation and improvement.

Instead of addressing security threats as they appear, the ISMS forces you to methodically identify assets, assess potential risks, and implement targeted treatments. This structured process protects critical data from breaches, unauthorized access, and loss, creating a truly resilient security foundation that builds trust with customers and partners.
How It Works in Practice
Implementing an ISMS under ISO 27001 follows a "Plan-Do-Check-Act" (PDCA) model, ensuring continuous improvement rather than a one-time fix. This cycle involves:
- Plan: Identifying risks, assessing their potential impact, and defining security controls.
- Do: Implementing the selected controls and security policies.
- Check: Monitoring the effectiveness of controls and measuring performance.
- Act: Making improvements and adjustments based on performance reviews and audits.
This repeatable framework is why major organizations rely on ISO 27001. For example, Microsoft uses the standard to secure its Azure cloud services, demonstrating its security commitment to enterprise clients. Similarly, the UK's NHS Digital adopted ISO 27001 to safeguard highly sensitive patient health records against evolving cyber threats.
Actionable Implementation Tips
To realize this benefit, start with a comprehensive risk assessment to identify your most critical information assets and their associated vulnerabilities. Engage all departments early in the process to ensure organization-wide buy-in, as information security is everyone's responsibility.
Key Insight: A successful ISMS is not just an IT project; it's a fundamental business process. It requires continuous management, monitoring, and improvement to remain effective against new and emerging threats.
For startups and scale-ups, leveraging automation platforms can streamline this process significantly. These tools can help conduct gap analyses, manage control implementation, and provide the necessary documentation for a successful audit. By using the right tools and strategies, you can build a robust security framework. To dive deeper into managing these processes effectively, you can explore some of the top risk management software available today.
2. Competitive Advantage and Business Growth
In a crowded marketplace, ISO 27001 certification acts as a powerful differentiator, signaling to potential clients and partners that your organization takes information security seriously. This internationally recognized standard is often a prerequisite for doing business with large enterprises, government agencies, and highly regulated industries. Achieving certification can unlock new revenue streams and open doors that were previously closed, transforming security from a cost center into a business enabler.

This verified stamp of excellence moves security discussions from a technical checklist to a strategic advantage. It demonstrates a commitment to protecting sensitive data, which builds immediate trust and can significantly shorten sales cycles. For companies in competitive fields, this benefit of ISO 27001 certification is a critical tool for standing out and proving their reliability.
How It Works in Practice
Certification provides tangible proof of your security posture, which is essential when responding to RFPs and security questionnaires. Instead of answering hundreds of questions, you can present your ISO 27001 certificate as evidence of a robust, audited ISMS.
- Winning Contracts: Certification often fulfills a mandatory requirement for tenders and enterprise-level contracts.
- Building Trust: It assures clients that you have systematic processes to protect their confidential information.
- Streamlining Sales: Reduces the friction and time spent on security due diligence with prospective customers.
- Market Expansion: Allows entry into new markets and industries where security is a primary concern.
Major enterprise players use this to their advantage. For instance, Salesforce leverages its ISO 27001 certification to win the trust of global enterprise clients who handle massive volumes of customer data. Similarly, smaller Managed Service Providers (MSPs) have reported client acquisition increases of 30-40% after getting certified, as it validates their security claims.
Actionable Implementation Tips
To leverage your certification for growth, start by prominently displaying the ISO 27001 logo on your website, marketing materials, and email signatures. Make sure your sales and marketing teams understand its value and can communicate it effectively to prospects.
Key Insight: ISO 27001 is more than a compliance badge; it's a powerful marketing and sales asset. It proactively answers your prospects' biggest security questions before they even ask them.
When responding to RFPs, lead with your certification details to immediately satisfy key security requirements. Create case studies that highlight how your ISMS protects client data, turning your security investment into a compelling narrative. Automating evidence collection with platforms like Comp AI ensures you are always prepared for these opportunities and can maintain your certification with ease during surveillance audits.
3. Regulatory Compliance and Legal Protection
Navigating the complex web of global and industry-specific regulations is a major challenge for modern businesses. One of the key benefits of ISO 27001 certification is its ability to streamline compliance efforts by providing a single, internationally recognized framework that maps to numerous legal and regulatory requirements. This unified approach simplifies audits, reduces redundant work, and demonstrates due diligence to regulators.
By implementing an ISMS based on ISO 27001, you create a robust system of controls and documentation that can serve as evidence of compliance with laws like GDPR, HIPAA, and others. This not only minimizes the risk of costly fines and penalties but also provides a strong legal defense in the unfortunate event of a data breach, proving that you took reasonable and appropriate steps to protect sensitive information.
How It Works in Practice
ISO 27001's framework is designed to be comprehensive and adaptable, allowing organizations to integrate multiple compliance needs into one cohesive system. This works by:
- Mapping Controls: Identifying the overlap between ISO 27001 controls and the specific requirements of regulations like GDPR's Article 32 (Security of Processing) or HIPAA's Security Rule.
- Demonstrating Due Diligence: Using the records from your ISMS, such as risk assessments and internal audits, to prove to regulators that your security measures are thoughtful and well-managed.
- Centralizing Evidence: Consolidating compliance documentation into a single repository, making it easier to respond to audits and information requests.
For example, a healthcare provider can use its ISO 27001 certification to demonstrate it meets the technical and administrative safeguard requirements of HIPAA. Similarly, financial services firms often align their ISO 27001 ISMS with PCI DSS controls to protect cardholder data, streamlining two separate but related compliance efforts.
Actionable Implementation Tips
To leverage ISO 27001 for regulatory compliance, start by mapping its controls to the specific legal requirements your organization must meet. Integrate these requirements into the scope of your ISMS from the very beginning to ensure they are addressed throughout the implementation process. Moreover, ISO 27001 certification provides a structured approach to help your organization navigate critical regulatory frameworks such as GDPR by formalizing data protection processes.
Key Insight: ISO 27001 doesn't automatically guarantee compliance with every law, but it provides an auditable framework that proves your commitment to security and makes demonstrating compliance significantly easier.
Keep detailed records of all risk assessments, incident responses, and management reviews, as this documentation is invaluable during a regulatory audit. By using automation platforms, you can efficiently manage this evidence and maintain an always-audit-ready posture, turning compliance from a periodic scramble into a continuous, manageable business function.
4. Customer Trust and Stakeholder Confidence
In an era defined by data breaches and privacy concerns, one of the most crucial benefits of ISO 27001 certification is its power to build and maintain trust. This certification acts as a globally recognized seal of approval, providing tangible, third-party validated proof that your organization prioritizes the security of customer and partner data. It moves security discussions from a list of promises to a demonstrated commitment.

This external validation is a powerful differentiator, especially for startups and scale-ups competing against established players. It assures clients, investors, and stakeholders that you have implemented a robust framework to manage information risks, which can be the deciding factor in closing deals, securing funding, and retaining loyal customers.
How It Works in Practice
Achieving ISO 27001 certification signals that your organization's security practices have been rigorously audited against an international standard. This assurance helps overcome initial objections and shortens sales cycles, as it pre-emptively answers critical security questions.
- Builds Credibility: It demonstrates a proactive commitment to data protection.
- Reduces Friction: It simplifies vendor security questionnaires and due diligence processes.
- Enhances Reputation: It protects your brand by minimizing the risk of security incidents.
- Attracts Investment: It shows potential investors that you manage operational risk effectively.
For instance, after facing public security scrutiny, Zoom achieved ISO 27001 certification to rebuild user trust and prove its dedication to securing communications. Similarly, FinTech startups like Revolut leverage the standard to build confidence with customers who are entrusting them with sensitive financial information.
Actionable Implementation Tips
To maximize this benefit, don't just get certified; communicate it. Create customer-facing materials that explain what your ISO 27001 certification means for their data's safety. Feature the certification badge prominently on your website, in email signatures, and within sales proposals to keep your security commitment front and center.
Key Insight: ISO 27001 is more than a compliance certificate; it's a powerful marketing and trust-building asset. Use it proactively in sales and marketing to turn your security posture into a competitive advantage.
For organizations handling vast amounts of sensitive data, like e-commerce platforms or SaaS providers, this trust is non-negotiable. Automating the evidence collection and control monitoring required for ISO 27001 with a platform like Comp AI not only streamlines the audit but also provides a continuous, real-time view of your security posture, which can be shared with key stakeholders to reinforce their confidence.
5. Reduced Security Incidents and Financial Losses
One of the most tangible benefits of ISO 27001 certification is its direct impact on your bottom line by drastically cutting down on security incidents and their associated costs. The standard's systematic approach to risk management, protective controls, and incident response planning moves an organization from a reactive stance to a proactive, defensive posture. This shift minimizes the likelihood of data breaches, reduces system downtime, and helps avoid steep regulatory fines.
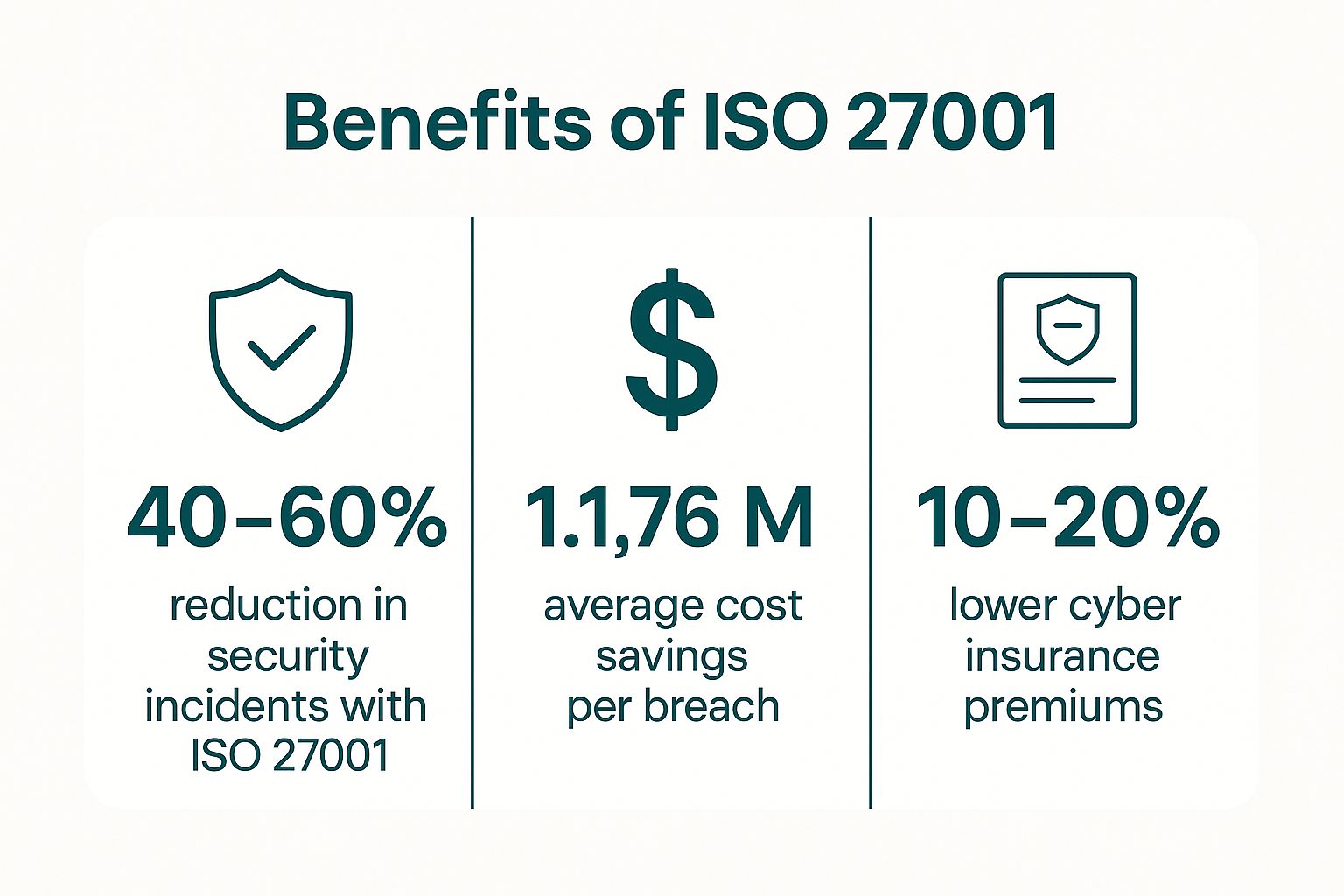
By proactively identifying threats and implementing robust controls, you are not just ticking a compliance box; you are building a resilient operational framework. This infographic visualizes the clear financial and operational advantages of this proactive approach. These figures underscore the powerful return on investment that a well-implemented ISMS can deliver, directly linking security posture to financial health.
How It Works in Practice
ISO 27001 requires organizations to establish formal incident response procedures, ensuring a swift and coordinated reaction when an event does occur. This readiness minimizes damage and accelerates recovery. The standard also mandates controls that prevent common attack vectors, directly reducing incident frequency.
- Prevent: Implementing access controls, encryption, and regular vulnerability scans to block threats.
- Detect: Using monitoring systems and regular reviews to identify suspicious activity early.
- Respond: Executing a well-defined plan to contain, eradicate, and recover from incidents.
- Learn: Analyzing incidents post-mortem to strengthen controls and prevent recurrence.
For instance, IBM's "Cost of a Data Breach Report" consistently shows that organizations with mature security practices, like those mandated by ISO 27001, save an average of $1.76 million per breach. A European financial services firm reportedly avoided over €20 million in potential GDPR fines after a breach because its ISO 27001 certification demonstrated due diligence to regulators.
Actionable Implementation Tips
Start by documenting and tracking all security incidents, no matter how small, before certification to create a baseline. This data will allow you to measure the ROI of your ISMS implementation over time. Understanding the non-negotiable importance of cybersecurity is the first step toward building this resilient foundation.
Key Insight: A robust incident response plan is not just about recovery; it’s a powerful tool for demonstrating compliance, reducing liability, and maintaining customer trust during a crisis.
To ensure your team is prepared, maintain and regularly test your incident response drills. A well-prepared team can significantly reduce the impact of a breach. For a head start, you can build your strategy with a comprehensive data breach response plan template designed to meet compliance standards.
6. Improved Organizational Efficiency and Culture
Beyond its primary security function, one of the most transformative benefits of ISO 27001 certification is its impact on organizational excellence. By mandating clear processes, roles, and responsibilities, the standard streamlines operations and fosters a culture where security is a shared value, not just an IT problem. This framework enhances cross-departmental communication, reduces human error, and creates more resilient, efficient workflows.

The process of defining and documenting security controls forces you to map out business processes and clarify who is responsible for what. This clarity eliminates ambiguity and operational bottlenecks, leading to smoother execution of daily tasks. A security-aware culture empowers employees to identify risks and follow best practices, making the entire organization a stronger, more cohesive unit.
How It Works in Practice
ISO 27001 creates a common language and set of procedures for handling information, which naturally improves efficiency. The framework promotes:
- Clear Roles: Explicitly defining responsibilities for information assets and security controls.
- Standardized Processes: Creating repeatable, documented procedures for everything from access control to incident response.
- Security Awareness: Embedding security consciousness into the company DNA through mandatory training and communication.
- Process Synergy: Aligning security controls with existing quality management or operational workflows.
For instance, Siemens integrated its ISO 27001 and ISO 9001 (Quality Management) systems, reporting a 15% improvement in overall operational efficiency. Similarly, Accenture leverages the standard as a core component of its employee onboarding, instilling a consistent security mindset across its massive global workforce from day one.
Actionable Implementation Tips
To maximize this benefit, align your ISMS with existing business workflows rather than creating entirely separate processes. Integrate security training into regular employee development programs and appoint "security champions" in each department to promote awareness and best practices.
Key Insight: ISO 27001 isn't about adding bureaucratic hurdles; it's about embedding smart, secure practices into your existing operations. A well-implemented ISMS makes your organization more efficient, not less.
For growing companies, making security training engaging is crucial for cultural adoption. Consider using gamification techniques or interactive modules to reinforce key concepts. Celebrate security wins, such as passing an audit or successfully thwarting a phishing attempt, to build positive momentum and reinforce the value of a strong security culture.
7. Supply Chain Security and Vendor Management
In today's interconnected business environment, your security is only as strong as its weakest link, which is often a third-party vendor. A major benefit of ISO 27001 certification is its formal requirement to secure the supply chain. The framework mandates rigorous processes for managing vendors, suppliers, and partners, ensuring they adhere to your security standards before they are granted access to your data or systems. This transforms vendor management from an operational checklist into a strategic security function.
By embedding security requirements into procurement and ongoing relationship management, you systematically reduce the risk of a breach originating from an external partner. This proactive stance prevents scenarios like the infamous 2013 Target breach, which was initiated through a compromised HVAC vendor. Establishing these controls is critical for protecting your organization from downstream vulnerabilities.
How It Works in Practice
ISO 27001, specifically through controls in Annex A.15 (Supplier Relationships), requires organizations to establish and maintain a secure supply chain policy. This involves:
- Plan: Defining security requirements for vendors based on the type of data and system access they need.
- Do: Integrating these requirements into contracts, conducting due diligence, and onboarding vendors securely.
- Check: Regularly monitoring and auditing vendor compliance with agreed-upon security policies.
- Act: Taking corrective action when a vendor fails to meet requirements or when new risks emerge.
This structured oversight is standard practice in risk-averse industries. For example, major banks often mandate ISO 27001 certification for their fintech partners to ensure customer financial data is protected. Similarly, Toyota requires key suppliers to be ISO 27001 certified to safeguard intellectual property and maintain production integrity across its complex supply chain.
Actionable Implementation Tips
To strengthen your vendor management, start by creating tiered security requirements based on vendor risk profiles and data access levels. Make sure to include ISO 27001 compliance clauses directly in new vendor contracts and Requests for Proposals (RFPs) to set clear expectations from the outset.
Key Insight: Effective vendor management is a continuous lifecycle, not a one-time check. It requires ongoing monitoring, regular security reviews, and collaborative incident response planning to remain effective against evolving supply chain threats.
For growing businesses, manually tracking dozens of vendors is unsustainable. Automation platforms can streamline vendor risk assessments, manage contract reviews, and centralize documentation for audits. By implementing a robust framework, you can confidently manage external relationships. You can learn more about how to establish these essential controls by exploring this guide to third-party risk management .
8. Business Continuity and Disaster Recovery Resilience
Beyond preventing threats, one of the key benefits of ISO 27001 certification is its focus on ensuring your organization can survive and recover from them. The standard mandates a structured approach to business continuity planning (BCP) and disaster recovery (DR), preparing your business to withstand and quickly resume operations after significant disruptions. This resilience isn't just for cyberattacks; it covers everything from hardware failures to natural disasters, safeguarding revenue and reputation.
This framework moves your organization from hoping a disaster won't happen to having a concrete, tested plan for when it does. By identifying critical processes and defining recovery objectives, ISO 27001 ensures you can minimize downtime and financial impact, maintaining customer trust even in a crisis.
How It Works in Practice
ISO 27001 requires organizations to establish, implement, and maintain a process for business continuity management. This involves:
- Plan: Conducting a business impact analysis (BIA) to identify critical activities and the resources required to support them.
- Do: Developing and documenting formal disaster recovery and incident response plans.
- Check: Regularly testing these plans through drills and simulations to identify weaknesses and ensure they are effective.
- Act: Reviewing test results and updating the plans to improve recovery capabilities and adapt to business changes.
This proactive approach is critical for operational stability. For instance, shipping giant Maersk credited its ISO-aligned disaster recovery procedures for enabling its recovery from the devastating NotPetya ransomware attack in just 10 days. Similarly, cloud providers like AWS use ISO 27001 continuity controls to deliver on their stringent 99.99% uptime service level agreements.
Actionable Implementation Tips
To build true resilience, start by conducting a thorough business impact analysis to prioritize your most essential functions. It is crucial to test your backup systems frequently to confirm they are not just being created but are also fully restorable when needed.
Key Insight: A business continuity plan is only effective if it's tested and understood. Regular drills ensure that when a real incident occurs, your team can act decisively and without panic, following a clear, practiced procedure.
For growing businesses, automating the documentation and management of these plans is key. Platforms like Comp AI can help structure your BIA, manage incident response documentation, and schedule regular reviews, ensuring your recovery plans remain current and effective. To build a solid foundation, you can learn more about how to create a robust business continuity policy that aligns with ISO 27001 standards.
Benefits Comparison of ISO 27001 Certification
| Aspect | Enhanced Information Security and Risk Management | Competitive Advantage and Business Growth | Regulatory Compliance and Legal Protection | Customer Trust and Stakeholder Confidence | Reduced Security Incidents and Financial Losses | Improved Organizational Efficiency and Culture | Supply Chain Security and Vendor Management | Business Continuity and Disaster Recovery Resilience |
|---|---|---|---|---|---|---|---|---|
| Implementation Complexity | High - requires systematic risk assessment and ISMS setup | Moderate - mainly involves certification and marketing efforts | Moderate - mapping ISMS to multiple regulations | Moderate - requires maintaining certification and audits | High - involves extensive controls and incident planning | Moderate - needs process definition and cultural change | Moderate to High - requires vendor assessments and contracts | High - requires backup systems and regular plan testing |
| Resource Requirements | Significant time, dedicated security and compliance staff | Certification costs, marketing resources | Ongoing compliance documentation and audits | Ongoing investment to maintain certification | Substantial initial cost plus ongoing security investments | Time for training, process setup, and cross-department efforts | Resources for vendor management and continuous monitoring | Investment in infrastructure, testing, and continuity training |
| Expected Outcomes | Proactive threat management, reduced breaches | Increased market opportunities and brand reputation | Simplified multi-regulation compliance and legal defensibility | Enhanced customer and stakeholder confidence | Lower frequency and cost of security incidents | Improved communication, reduced errors, and security culture | Reduced third-party risks and improved vendor security | Faster recovery, reduced downtime, and operational resilience |
| Ideal Use Cases | Organizations needing robust data protection | Businesses seeking market differentiation via security | Firms facing complex regulatory environments | Companies wanting to build trust with clients and investors | Entities seeking to minimize breach impact and losses | Organizations aiming to foster security-aware culture | Companies with extensive vendor and supply chain dependencies | Businesses needing resilient operations against disruptions |
| Key Advantages | Comprehensive ISMS, continuous improvement, clear accountability | International recognition, access to contracts, marketing edge | Supports diverse regulatory needs, legal protection | Independent verification, reputation boost, customer retention | Reduced breach costs, cyber insurance savings | Clear roles, process clarity, and basis for other ISO standards | Standardized vendor security, contractual protections | Minimized downtime, stakeholder confidence, improved insurance |
Turn Compliance from a Hurdle into a Strategic Advantage
Embarking on the ISO 27001 certification journey is not merely about checking a box; it's a strategic business decision that fundamentally transforms your organization's approach to information security. Throughout this guide, we've detailed the extensive benefits of ISO 27001 certification, moving far beyond basic compliance. It's about building a resilient, trustworthy, and efficient enterprise poised for sustainable growth in a data-driven world.
The advantages are interconnected and create a powerful flywheel effect. By establishing a robust Information Security Management System (ISMS), you systematically reduce vulnerabilities and minimize the financial and reputational damage of security incidents. This enhanced security posture directly translates into increased customer trust and stakeholder confidence, unlocking new markets and strengthening relationships with enterprise clients who demand verifiable security assurances.
From Cost Center to Growth Engine
Ultimately, ISO 27001 certification redefines information security's role within your company. It shifts from being a reactive cost center to a proactive driver of strategic value. The standard instills a culture of security awareness, improves operational efficiency by standardizing processes, and provides a powerful differentiator in a crowded marketplace. You're not just protecting data; you're building a foundation for scalable, secure, and resilient operations.
The key takeaways are clear:
- Trust is a Currency: Certification is a globally recognized signal that you take data protection seriously, making you the preferred partner for security-conscious clients.
- Resilience is a Requirement: An effective ISMS ensures you can withstand and recover from disruptions, protecting your revenue and reputation.
- Efficiency is a Byproduct: Standardized security controls and clear processes reduce ambiguity, streamline operations, and empower your team to work more effectively.
While the path to certification has traditionally been viewed as resource-intensive and complex, modern compliance automation platforms have completely changed the landscape. You no longer need to choose between speed and security. By leveraging AI-driven solutions, you can automate evidence collection, streamline risk assessments, and maintain continuous compliance with a fraction of the manual effort. This allows your team to focus on strategic initiatives, confident that your security framework is robust, audit-ready, and aligned with international best practices. Embracing this modern approach makes achieving the benefits of ISO 27001 certification faster and more accessible than ever before.
***
Ready to transform your security posture and unlock your business's full potential? See how Comp AI automates over 90% of the work required for ISO 27001, getting you audit-ready in weeks, not months. Schedule your demo with Comp AI today and turn compliance into your competitive advantage.
Share this article
Help others discover this content
More from Compliance Hub
Explore more insights and stay ahead of regulatory requirements.
Your 8-Point HIPAA Compliance Audit Checklist for 2025
Prepare for your OCR audit with our definitive HIPAA compliance audit checklist. Covers administrative, physical, and technical safeguards to ensure success.
Top 12 HIPAA Risk Assessment Tools for 2025
Explore our expert review of the top 12 HIPAA risk assessment tools. Find the right platform to simplify compliance and protect your organization in 2025.
12 Best Vulnerability Management Tools of 2025
Discover the 12 best vulnerability management tools for 2025. Our in-depth review covers features, pros, cons, and use cases to secure your assets.