Every business today relies on external vendors. Cloud providers store your data, payment processors handle transactions, and marketing platforms manage customer communications. But here's the reality: roughly 30% of data breaches involve a third party, according to recent Verizon DBIR research. That percentage has been climbing steadily, and the costs are staggering.
If you're a CTO, CISO, founder, or security leader, you've probably felt the pressure. Your team is racing to close deals, but enterprise customers keep sending those lengthy security questionnaires. Regulators are tightening rules about vendor oversight (PCI DSS 4.0 just went into effect in March 2025). And every headline about another supply chain attack reminds you that your security is only as strong as your weakest vendor.
This guide cuts through the noise. You'll learn exactly what third-party risk management is, why it matters more than ever, what types of risks you're facing, and how to build a pragmatic program that actually works (without boiling the ocean). By the end, you'll have a clear roadmap to protect your business from vendor-related disasters while accelerating sales and staying compliant.
What Does Third-Party Risk Management Mean?
Third-party risk management (TPRM) is the systematic process of identifying, assessing, and mitigating risks that arise when you rely on external organizations. These "third parties" include anyone you depend on: software vendors, cloud service providers, consultants, payment processors, contractors, supply chain partners, and more.
Think of TPRM as extending your internal security and risk practices to cover everyone in your ecosystem. The goal is simple: ensure vendors meet your security and compliance standards, protect the data or systems they access, and don't introduce unacceptable risk into your operations.
In practice, a strong TPRM program ensures third parties:
- Protect data and systems by maintaining solid cybersecurity and handling your information safely
- Comply with regulations and ethics by following privacy laws, financial requirements, and avoiding practices that could implicate your company
- Maintain quality and continuity by meeting service levels, having resilience plans for disruptions, and upholding performance standards
By managing vendor relationships this way, you reduce the likelihood of breaches, service outages, compliance violations, or other incidents originating from outside partners.
Some people call this vendor risk management (VRM) or supply chain risk management. All refer to the same core idea: controlling risks from external dependencies.
Why Are Third-Party Data Breaches Increasing in 2025?
Third-party risk isn't theoretical. It's become one of the biggest threats to organizational security and stability. Recent incidents and studies make this crystal clear:
How Do Vendors Cause Data Breaches?
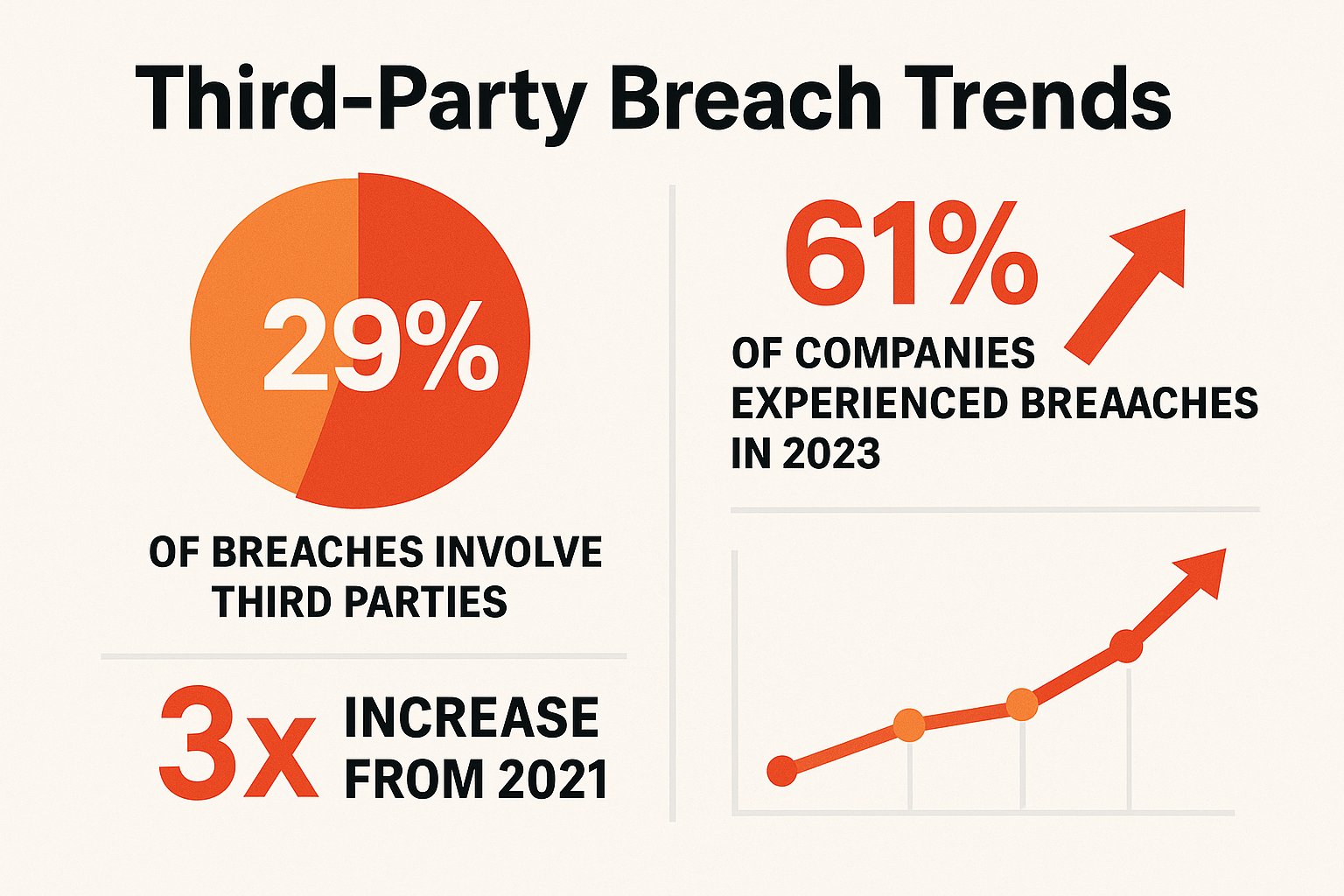
Attackers increasingly target less-secure suppliers and service providers as a back door into well-protected companies. Research shows at least 29% of all data breaches involve a third-party attack vector.
Even more alarming: in 2023, over 61% of companies experienced a data breach or cybersecurity incident because of a third party. That's triple the rate from 2021.
High-profile examples drive the point home. The Target breach in 2013 started through an HVAC subcontractor, exposing 40 million customer card records. The 2020 SolarWinds incident showed how a compromised software supplier can infect thousands of organizations downstream. In 2024, the Snowflake-related data thefts affected multiple enterprises when attackers exploited access patterns tied to a single platform dependency.
A security weakness in one vendor can cascade into a massive breach affecting you and your customers.
What Are the Financial Costs of Third-Party Breaches?
Third-party failures can disrupt your business or hit your bottom line hard. If a critical supplier in your supply chain can't deliver due to a cyber incident, bankruptcy, or natural disaster, your own operations may grind to a halt. If your cloud hosting provider goes down, your product stays offline until they recover.
Studies find that breaches involving third parties cost roughly 40% more to remediate than incidents confined to your own systems. The average financial impact of a third-party data breach reached $4.88 million globally (IBM's 2024 Cost of a Data Breach report).
Beyond direct costs, companies suffer loss of revenue from downtime and increased expenses to resolve vendor-caused issues.
Can You Be Liable for Your Vendor's Compliance Failures?
When a vendor mismanages data or fails to meet obligations, your organization may face regulatory penalties and lawsuits, even if the mistake wasn't yours. Privacy laws like GDPR make you liable if your vendor breaches personal data. Banking regulators require banks to rigorously oversee outsourcing relationships.
U.S. financial regulators (OCC, Federal Reserve, FDIC) and many international authorities have established strict expectations for third-party risk oversight, with power to levy fines or sanctions if your TPRM program is deemed inadequate.
Simply put: "I trusted my vendor" is not a defense. You're expected to vet and monitor vendors as extensions of your own enterprise.
How Do Vendor Failures Damage Company Reputation?
Customers and business partners trust you to safeguard data and deliver reliably. A failure by one of your vendors can tarnish your reputation and erode customer trust just as much as if your own systems were breached.
If your payment processor leaks customer payment information or your marketing partner emails out spam, your brand will be in the headlines alongside theirs.
Studies indicate the biggest impacts of third-party security incidents (besides financial loss) are reputational damage and heightened regulatory scrutiny. It can take years to rebuild credibility after a supply chain incident.
How Many Third-Party Vendors Does Your Company Actually Have?
Organizations today rely on more third parties than ever before. Cloud services, SaaS apps, outsourcing, and global supply chains mean even a small firm might have dozens of vendors with access to its data or systems.
A 2024 survey found companies were sharing confidential information with an average of 583 third-party vendors. Enterprise TPRM surveys report supply chains involving thousands of third parties on average.
Each of those relationships is a link in your security chain. The weakest link principle applies: one poorly secured or ill-prepared partner can compromise the whole chain. This massive exposure makes a strong TPRM program essential.
Bottom line: TPRM matters because it tackles one of the highest-impact risk vectors organizations face today. The stakes are too high and the incidents too frequent to ignore third-party risk management.
What Are the Main Types of Third-Party Risks?
Third-party risk is an umbrella term covering several threat categories. When you engage an outside vendor or partner, these forms of risk can arise:
What Is Cybersecurity Risk in Third-Party Relationships?
The most prominent concern is that a third party could be the weak link hackers exploit. If a vendor with network access or sensitive data privileges gets compromised, attackers might use that foothold to infiltrate your systems or steal data. Third parties broaden your attack surface beyond your own perimeter.
Common scenarios include:
- Vendor employee credentials are stolen and used to hack your account
- Software supplier ships a malware-infected update (supply chain attack)
- Contractor's laptop with your data on it gets breached
- Cloud provider suffers a configuration error that exposes customer data
The resulting impacts can include data breaches, ransomware infections, and loss of system integrity via the third party. Strong TPRM aims to ensure vendors have robust security controls and to detect any cyber weakness before it bites you.

How Can Third Parties Disrupt Your Business Operations?
This is the risk of a third party disrupting your ability to serve customers or run day-to-day operations. It often relates to supply chain and continuity issues.
If a crucial component supplier fails to deliver parts, a manufacturer's production line could halt. If a cloud hosting provider suffers an outage, your online service may go down until they restore service.
Third-party operational failures can stem from many causes: financial insolvency, internal malfunctions, labor strikes, natural disasters affecting the vendor. The COVID-19 pandemic and other global events highlighted how a breakdown at one supplier can ripple outward.
TPRM addresses this by vetting vendors' resiliency (do they have backup plans, multiple data centers?) and creating contingency plans to maintain business continuity if a vendor can't deliver.
What Compliance Violations Can Third Parties Cause?
If a vendor in your ecosystem violates laws, regulations, or industry standards, your organization can be exposed to legal penalties, regulatory fines, or contractual breaches.
For instance, a payroll processor that mishandles tax filings could land you in trouble with tax authorities. Or a third-party data processor that doesn't follow privacy laws could cause you to be fined under GDPR or HIPAA.
Many regulations include specific vendor oversight requirements. If your TPRM is lax and a vendor fails a compliance obligation, regulators may deem you non-compliant. There's also contractual risk: if your contract with a client requires certain standards across all subprocessors, and one of your subcontractors falls short, you could be in breach of client obligations.
What Are the Financial Risks from Third-Party Failures?
Third-party failures can carry direct and indirect financial impacts. Direct financial risk includes scenarios like a vendor overbilling you, experiencing fraud, or suffering a data breach that leads to penalties or lawsuits impacting your finances.
Indirect financial risk comes from operational disruptions: if a key supplier's outage means you lose sales, or if a vendor's breach causes customer churn and incident response costs.
Another angle is credit risk: if you rely on a small vendor and they go bankrupt, you may lose prepaid funds or face costs to find a replacement. Any hit to your revenue, expenses, or asset values stemming from a third-party issue is a financial risk.
How Do Vendor Actions Affect Your Company's Brand Value?
Your reputation is intertwined with your vendors' behavior. If a third party engages in unethical conduct or suffers a publicized incident, it can reflect poorly on your organization.
For example, if your overseas supplier is found using child labor or your marketing partner leaks customer data, your company could face public outrage and loss of trust.
These reputational hits can translate to strategic business risks: loss of market share, drop in stock value, or inability to achieve key objectives because stakeholders no longer have confidence. TPRM isn't only about preventing discrete incidents. It's about safeguarding your organization's standing and long-term strategy from the actions of third parties.
Important note: These risk categories often overlap. A vendor data breach, for example, can trigger cybersecurity, operational, compliance, financial and reputational risks all at once.
What Are the Stages of Third-Party Risk Management?
Managing third-party risk is an ongoing cycle that spans the entire relationship with a vendor, from initial selection to offboarding. While organizations may tailor the details, a typical TPRM lifecycle consists of several key stages:
How Do You Assess Vendor Risk Before Signing a Contract?
Before you onboard a new vendor, thoroughly vet their risk profile. This involves gathering information about the third party's security controls, privacy practices, financial stability, operational capabilities, and compliance history.
Common due diligence activities include:
- Sending security questionnaires for the vendor to answer (covering areas like access control, encryption, incident response)
- Reviewing any audits or certifications they have (SOC 2 reports, ISO 27001 certificate, PCI compliance attestations)
- Conducting background checks or reputation research (have they had past breaches or legal issues?)
- Evaluating their financial statements or insurance coverage
High-criticality vendors might also undergo a more in-depth assessment such as an on-site audit or penetration test of their systems. The goal at this phase is to identify inherent risks and decide if the vendor meets your minimum risk criteria.
It's important to categorize vendors by risk level during assessment. For example, assign a tier (Tier 1 high risk, Tier 2 medium, Tier 3 low) based on factors like the sensitivity of data they'll handle or how critical their service is. This risk tier will dictate how much scrutiny and ongoing monitoring they require.
What Security Requirements Should Be in Vendor Contracts?
Once you decide to proceed with a vendor, the contract negotiation and onboarding phase is crucial for risk management. Ensure that the vendor contract includes clear security and compliance requirements.
For example, you may write in clauses that the vendor must:
- Maintain specific security measures (encryption standards, regular patching, employee training)
- Notify you of any data breach or security incident within X hours
- Comply with all relevant regulations (like GDPR, HIPAA)
- Allow periodic audits or security reviews
- Carry liability insurance
Service Level Agreements (SLAs) should cover not just performance metrics but also recovery time objectives if a disruption occurs. Also, specify controls around data: who owns the data, how it must be returned or deleted on request, and restrictions on subcontracting (to manage fourth-party risk: your vendor's vendors).
At onboarding, also verify that the vendor's access to your systems and data is set up with the principle of least privilege (only the minimum necessary access). This stage is about formally binding the vendor to risk-mitigating measures and setting expectations before work begins.
How Do You Monitor Third-Party Risks Continuously?
Once the vendor is onboarded and working, TPRM shifts into a continuous mode. Ongoing monitoring means you don't "set and forget" a vendor after the initial vetting. You regularly track their risk posture throughout the relationship.
Key aspects of continuous TPRM include:
- Keeping an up-to-date inventory of all third parties (so none fall through the cracks)
- Subscribing to security rating services or threat intelligence feeds that can alert you to issues with the vendor (for example, if a vendor's systems show up in darknet breach databases or their security rating drops significantly, indicating new vulnerabilities)
- Setting reminders for periodic reassessments (many organizations do a yearly review for critical vendors, including sending an updated questionnaire or requesting evidence of controls)
- Monitoring news and adverse media for incidents involving the vendor
- Staying aware of any changes in the vendor's situation (leadership changes, acquisitions, financial trouble that could increase risk)
Essentially, treat third-party risk like a living risk that needs consistent watching, much like you monitor internal systems with dashboards and alerts. Many companies employ automated tools for this.
Continuous control monitoring can be done via integrations that check a vendor's security configurations in real time, and external attack surface monitoring can reveal if the vendor's domain has new vulnerabilities.
The idea is to get early warning of any degradation in the vendor's security or compliance standing, rather than waiting for the next scheduled audit (or a breach) to find out.
What Should You Do When a Vendor Has a Security Incident?
Despite all precautions, incidents can still happen. A robust TPRM program includes plans for responding to vendor-related incidents or performance failures. This involves establishing clear procedures for various scenarios: what to do if the vendor notifies you of a breach, if the vendor misses an SLA or has an outage, or if they're implicated in a compliance violation.
It's critical to have communication channels and escalation paths defined with each key vendor. You should know how to reach their security team 24/7 and they should know how to reach yours. Your contract should oblige them to provide timely information during incidents.
Internally, your incident response policy should account for third-party incidents (often called supply chain incident response). For example, if a vendor is breached, you may need to quickly disable integrations or connections to that vendor to contain damage, notify mutual customers or regulators, and perhaps provide forensic support.
Also, think in advance about backup solutions: if a critical service provider goes down, do you have a secondary provider or workaround to keep business running? If a vendor fails to meet standards despite remediation efforts, are you prepared to terminate the relationship?
Business continuity and disaster recovery planning should incorporate the possibility of vendor failures. In practice, many companies perform periodic drills or tabletop exercises that include third-party scenarios (like "What if our payment processor is hacked?").
The goal of this phase is to minimize damage and recover quickly when a third-party issue occurs.
How Do You Properly End a Vendor Relationship?
The TPRM lifecycle doesn't end until after you've severed ties with the vendor and ensured no residual risk remains. When a third-party contract comes up for renewal, it's an opportunity to re-evaluate risk versus benefit and decide whether to continue the relationship (possibly with updated terms) or terminate it.
If you choose to offboard a vendor, follow a formal process:
- Confirm all your data has been returned or securely destroyed
- Terminate the vendor's access credentials or integrations
- Retrieve any assets or equipment
- Update your internal records to reflect the end of the relationship
It's wise to perform a final risk review at offboarding. For instance, check that there are no lingering accounts left active and no outstanding obligations. Document the steps taken in an offboarding checklist. Regulators may expect proof that you properly disentangled the vendor.
Even after termination, keep records of the vendor's performance and any incidents, as these can inform future relationships or legal needs. Proper offboarding ensures that loose ends are tied up and that the end of a partnership doesn't become the beginning of a breach or compliance issue.
Remember: These stages form a continuous cycle. TPRM is not a one-time project but an ongoing program. As long as you rely on third parties, their risks must be actively managed.
Third-Party Risk Management Best Practices
Implementing TPRM can be challenging, especially as vendor networks grow and threats evolve. Following industry best practices will greatly strengthen your program. Here are some key best practices used by leading organizations:
1. Build Governance for Vendor Risk Management
Treat TPRM as a formal part of your enterprise risk management. Secure executive buy-in and clear ownership of the TPRM process. For example, designate who is ultimately accountable (Chief Risk Officer or similar) and establish a cross-functional steering committee that meets regularly to review major vendor risks.
Develop a comprehensive Vendor Risk Management Policy (and supporting procedures) that defines how vendors are evaluated, what controls are required, how often to review them. This policy should align with your overall risk appetite and regulatory obligations.
Governance also means keeping an eye on regulatory changes and updating your TPRM policy accordingly. Many organizations map their TPRM controls to frameworks like ISO 27001, NIST Cybersecurity Framework, or specific industry guidelines to ensure completeness.
2. Categorize Vendors by Risk Level
You can't manage what you don't know about. Maintain an accurate, centralized inventory of every third-party relationship, including what data or systems they can access and a point of contact for each.
As part of onboarding, assign each vendor a risk tier or rating based on inherent risk factors (data sensitivity, business criticality). Focus your resources where risk is highest: Tier 1 (high risk) vendors get the most stringent due diligence and frequent monitoring, whereas Tier 3 (low risk) vendors may go through a lighter process.
This risk-based approach ensures you're not wasting effort assessing a catering service as deeply as your cloud provider. It also helps in reporting, so you can communicate how many high-risk versus low-risk vendors you have and how each category is managed.
3. Good Vendor Risk Assessment Process
Consistency is key. Use standardized questionnaires and assessment frameworks for evaluating vendors. Industry-standard questionnaires (like the SIG Lite, SIG Full, CAIQ for cloud providers, or custom checklists aligned to your policies) help gather comparable information from each vendor.
Having a fixed set of criteria also guards against ad hoc risk decisions. Ensure assessments cover not just IT security but also areas like privacy, compliance, resiliency, and any domain-specific risks (a healthcare vendor should be assessed for HIPAA safeguards, a finance vendor for FFIEC compliance).
It's also a best practice to score or rate vendor risks quantitatively wherever possible. For instance, assigning a risk score 1 to 5 on categories like network security, financial health. This makes it easier to compare vendors and track improvement or decline over time.
If a vendor doesn't meet your minimum score, have a formal process to mandate remediation before contract (they must fix certain issues or implement multi-factor authentication as a condition of doing business). Document all assessment results and decisions for audit trail purposes.
For example, Comp AI's SOC 2 Compliance Checklist provides a comprehensive standardized framework that organizations can use as a starting point for vendor assessments. This type of structured checklist ensures consistent evaluation across all vendors while making the process more efficient.
4. Contract Clauses Protect Against Third-Party Risk
Legal agreements are your enforceable safeguard. Always include specific clauses in vendor contracts that address security and risk. Require breach notifications, compliance with laws, audit rights, and even the right to terminate the contract for serious security failures.
Ensure there are indemnification clauses if the vendor's negligence leads to a loss. This won't save your reputation, but it can help recoup costs. If applicable, include language that allows you to conduct security testing or bring in a third-party auditor to assess the vendor.
Clearly outline data handling requirements (encryption, geographic restrictions, subcontractor approvals) in the contract. A strong contract sets expectations from day one and gives you leverage to enforce them. It also gets all internal stakeholders (legal, procurement, IT) on the same page regarding vendor obligations.
5. Monitor Vendors in Real Time
Don't rely solely on annual check-ins. Implement a mix of continuous monitoring tools and frequent communication with vendors to stay updated. Many firms use automated solutions that provide real-time security ratings or alerts about vendors.
These can detect issues like exposed credentials, unpatched vulnerabilities, or network misconfigurations at a vendor, sometimes even before the vendor is aware. Set risk threshold triggers: for example, if a vendor's external security rating drops below a B, it flags a review.
Plus, maintain regular touchpoints: quarterly calls or questionnaires for critical vendors to discuss any changes, share new compliance requirements, and review performance.
Upward communication inside your organization is also crucial. Keep senior management and relevant teams informed about major third-party risks, mitigation plans, and any incidents. This can be done through periodic TPRM reports that summarize the risk posture of your vendor portfolio (covering metrics like how many vendors in each risk tier, recent assessment findings, outstanding issues).
By continuously monitoring and communicating, you can catch problems early and avoid nasty surprises.
6. Business Continuity Plans for Vendor Failures
Hope for the best, but prepare for vendor failures. Develop and test contingency plans for your most critical third parties. For example, identify backup vendors or alternative processes if your primary vendor can't deliver. If you use a single cloud provider, consider a strategy for migrating to an alternate environment if needed.
Ensure your business continuity plan includes scenarios like "key supplier X is down for 1 week" or "vendor Y had a data breach affecting our data" and spells out the steps your team must take.
Establish clear internal procedures for handling vendor breaches: who is responsible for coordinating with the vendor, what notifications must be made (to customers, regulators), and how to remove or replace the vendor if the situation is irreparable.
Conduct training or drills on these procedures so that your team isn't figuring it out from scratch under pressure. Many organizations also form a dedicated incident response team or involve the existing IR team to specifically handle third-party incidents, since these can involve complex coordination.
Remember that a vendor issue can quickly become your issue in the public's eyes, so having a solid response playbook is part of protecting your brand and customers.
7. Manage Fourth-Party Risk (Your Vendor's Vendors)
Your third parties have their own third parties, which becomes fourth-party risk to you. For instance, if you use a payroll service, they might rely on a cloud hosting provider. That hosting provider is a fourth-party in your chain. It's easy to lose sight of these extended relationships.
A best practice is to require critical vendors to disclose their key subcontractors or suppliers that support the service they provide you. Assess the subcontractor risks indirectly. You may not have a direct contract, but you can ask your vendor how they vet and monitor their vendors.
In some cases, you might insist on approving subcontractors or at least being notified of changes. Also, incorporate fourth-party considerations in your questionnaires ("Do you outsource any part of the service? Provide details.").
Be aware that fourth-party risk is harder to manage (since you often lack privity), but awareness is growing that it's a major blind spot. At minimum, document known critical fourth parties in your risk register. If a crucial fourth party has a public issue, treat it as a red flag for your own vendor and seek assurance or mitigation steps.
In summary, don't stop your risk mapping at the first layer. Probe the supply chain depth as much as possible to avoid hidden risks downstream.
8. Resources Third-Party Risk Management Needs
Many organizations struggle with TPRM because they try to do it with insufficient staff or outdated methods. Surveys show over 60% of companies cite understaffing as a major obstacle in third-party risk management. On average, organizations felt they needed double the dedicated staff to manage vendor security properly.
To bridge this gap, make sure you allocate enough personnel and budget to TPRM proportional to your vendor portfolio's size and risk. Also, move away from manual, siloed processes (like spreadsheets) and invest in tools that can automate and streamline TPRM.
Modern TPRM software platforms can centralize your vendor inventory, send and score questionnaires, track remediation tasks, and integrate with threat intelligence for continuous monitoring. Many also provide dashboards for reporting to executives.
Using such a platform not only saves time but ensures nothing falls through cracks (automated reminders when a vendor review is due). Some organizations even integrate their TPRM system with procurement systems so that no new vendor can be onboarded without a risk check.
Emerging technologies like AI are starting to play a role. For instance, AI can auto-answer parts of questionnaires or sift through news about vendors to flag relevant risks. While adoption is still early (only about 5% of companies currently use AI in TPRM according to one 2024 Prevalent study), interest is high in using AI for smarter risk analysis and faster incident detection in supply chains.
Using these technologies and services (such as continuous vendor risk rating services) can significantly enhance your program's efficiency and effectiveness. In short: use humans for judgment, use automation for grunt work. This frees your risk analysts to focus on high-value analysis rather than chasing paperwork.
9. Build Trust with Your Vendors on Security
Successful TPRM is as much about relationships and culture as it is about checklists. Build collaborative relationships with your vendors' management and compliance teams. Communicate your security expectations clearly and early. For example, share your vendor security policy or handbook with them.
Encourage an environment where vendors feel comfortable reporting issues or near-misses (rather than hiding them). Some companies incorporate security into quarterly business reviews with key vendors to keep the topic on the agenda.
When possible, treat vendors as extensions of your team: if you learn of a new threat (say, a critical software vulnerability), you might notify important vendors so they can patch it too. This not only reduces risk for both parties but strengthens trust.
Conversely, if a vendor isn't responsive to your risk concerns or continually falls short, be willing to escalate through leadership or ultimately part ways. Your risk posture depends on others, so you need others to take it seriously.
Internally, train your employees (especially those who engage vendors) about third-party risks as well. For instance, procurement staff should know to loop in security before signing up a new SaaS tool. By making third-party risk management everyone's responsibility, you create a culture that values due diligence over convenience.
How Comp AI Simplifies Third-Party Risk Management
If you're building a TPRM program from scratch or trying to scale an existing one, you know the challenges: hundreds of vendors to track, endless questionnaires to process, evidence to collect and refresh, and constant monitoring to maintain. Traditional approaches rely heavily on manual spreadsheets, email chains, and periodic check-ins that can't keep pace with today's dynamic vendor ecosystems.
This is where automation makes a transformative difference. Comp AI helps organizations accelerate and strengthen their third-party risk management in several key ways:
Automated Evidence Collection and Refresh: Instead of manually chasing vendors for SOC 2 reports, ISO certificates, or policy documents, Comp AI can auto-collect and refresh evidence from vendors. The platform maps this evidence to your controls, so you always know which vendors are current and which need attention. This dramatically reduces the time spent on evidence gathering and lets you focus on actual risk analysis.
AI-Powered Security Questionnaires: Processing security questionnaires is one of the most time-consuming parts of TPRM. Comp AI's AI-powered Trust Center can answer security questionnaires in minutes instead of days. When a vendor or customer sends you a questionnaire, the AI pulls from your documented policies, controls, and compliance posture to generate accurate responses. This turns vendor risk assessment from a bottleneck into a competitive advantage, helping you respond to RFPs and security reviews at speed.
Continuous Monitoring and Risk Dashboards: Rather than waiting for annual reviews, Comp AI provides continuous monitoring of key signals. The platform keeps your vendor inventory, sub-processor lists, and risk dashboards up to date automatically. This means you can spot emerging risks (like a vendor losing a certification or experiencing a security incident) in real time and take action before it impacts your business.
Audit-Ready Compliance: Whether you're pursuing SOC 2, ISO 27001, HIPAA, or other frameworks that require vendor oversight, Comp AI helps you get audit-ready in days, not months. The platform centralizes all your third-party documentation and evidence in one place, making it easy to demonstrate to auditors that you have a comprehensive TPRM program in place.
When you combine AI-powered automation with expert support, you get the benefits of a mature TPRM program without the overhead of building and maintaining it manually. This is especially valuable for growing companies that need to scale vendor oversight as they onboard more third parties and pursue enterprise customers.
Comp AI's intuitive interface makes vendor risk management accessible to teams without dedicated compliance staff, while still providing the depth and automation needed to satisfy auditors and enterprise customers.
What Mistakes Should You Avoid in Third-Party Risk Management?
Even with the best intentions, organizations often stumble into these common traps when implementing third-party risk management:
One-and-Done Questionnaires: Sending a security questionnaire during vendor selection and then never following up is a recipe for trouble. Assurance decays fast. A vendor that was secure last year might have had a breach, lost key security staff, or let certifications lapse. Build a refresh cadence by tier (annual for critical vendors, every two years for medium-risk, etc.) and stick to it.
Paper-Only Compliance: Don't just accept a vendor's word that they have certain controls in place. Ask for artifacts (log screenshots with timestamps, config exports, recent audit reports) and cross-verify when possible. For example, if a vendor claims they enforce MFA, ask to see the last 90 days of SSO access logs. Spot-checking keeps everyone honest.
Ignoring Fourth Parties: Many TPRM programs stop at the first layer of vendors. But your vendors' vendors can introduce significant risk. Require a sub-processor list and change notifications from critical vendors. Assess the most important fourth parties, especially those handling your most sensitive data paths.
No Exit Plan: Offboarding is where data often lingers and creates risk. When you terminate a vendor relationship, demand deletion certificates and verify that credentials have been revoked and data has been destroyed. Don't assume the vendor will clean up properly without explicit requirements and verification.
Treating All Vendors the Same: Not every vendor poses the same risk. Don't spend equal effort assessing your coffee supplier and your cloud infrastructure provider. Use risk tiering to focus deep assessments on high-risk vendors and streamlined processes for low-risk ones. This makes your program both more effective and more sustainable.
Third-Party Risk Management Checklist: What Should You Verify?
Use this checklist to ensure you're covering the essentials:
- Policy & RACI defined: Third-party risk policy approved; roles and responsibilities clear; risk appetite documented
- Unified vendor inventory: Centralized list of all third parties (finance systems, SSO logs, procurement records, shadow IT)
- Tiering model in place: All vendors categorized by risk tier (Tier 1 high, Tier 2 medium, Tier 3 low)
- Due diligence kits ready: Standardized questionnaires and evidence requests by tier (SIG, CAIQ, SOC 2, ISO 27001)
- Critical vendor gate: Minimum controls and contract clauses required before production access
- Contracts with security clauses: Breach notification requirements, audit rights, data handling terms, subcontractor disclosure
- Continuous monitoring active: Automated alerts for vendor security ratings, certificate expirations, adverse media
- Incident response playbook: Documented procedures for vendor breaches and failures; tested via tabletop exercises
- Fourth-party visibility: Sub-processor lists collected; critical fourth parties identified and assessed
- Board metrics defined: Regular reporting on vendor risk posture, coverage, findings, and remediation progress
Frequently Asked Questions About Third-Party Risk Management
What's the difference between third-party risk management and vendor risk management?
They're essentially the same thing. TPRM and VRM both refer to the process of identifying and mitigating risks from external parties you do business with. Some organizations use "vendor risk management" when referring specifically to suppliers and service providers, while "third-party risk management" is a broader term that can include partners, contractors, and other external relationships. In practice, the terms are used interchangeably.
How often should I reassess my vendors?
It depends on the vendor's risk tier. Critical vendors (Tier 1: handling sensitive data, mission-critical services, privileged access) should be reassessed annually at minimum, with continuous monitoring in between. Medium-risk vendors (Tier 2) might be reassessed every 18 to 24 months. Low-risk vendors (Tier 3) may only need reassessment when the contract comes up for renewal or if there's a significant change (like a breach or acquisition). Always reassess immediately if a vendor has a security incident or major change in their risk profile.
What should I do if a vendor won't complete my security questionnaire?
First, explain why the questionnaire is important and what specific concerns you're addressing. Offer to reduce the questionnaire to only the most critical questions for their service. If they still refuse, you have several options: accept alternative evidence (existing SOC 2 or ISO 27001 reports that cover the same ground), escalate to their management or your executive sponsor, or consider whether this vendor is worth the risk. A vendor that won't engage on basic security questions is a red flag. Sometimes the answer is to find a different vendor.
Do I need a dedicated TPRM team?
It depends on the size and complexity of your vendor ecosystem. Small companies (fewer than 50 vendors) can often manage with security or IT staff spending part of their time on vendor oversight. Mid-sized companies (50 to 500 vendors) typically need at least one dedicated person. Large enterprises (thousands of vendors) usually have a full TPRM team with specialized roles (assessment analysts, contract specialists, monitoring operators). Survey data shows most organizations feel they need about double their current TPRM staffing, so if you're stretched thin, you're not alone. Technology and automation can help bridge the gap.
How do I know if my TPRM program is effective?
Look at these indicators: You can produce an accurate list of all vendors within minutes. Critical vendors have been assessed within the past 12 months. You have documented evidence of key controls for high-risk vendors. You've caught and remediated at least one vendor issue before it caused an incident. Executive leadership receives regular updates on third-party risk. Auditors or customers accept your vendor assessments without major questions. Vendor-related incidents are rare and quickly contained. If you can check most of these boxes, your program is on solid footing. If not, focus on the gaps.
What's the biggest mistake companies make with third-party risk?
The biggest mistake is treating TPRM as a one-time checklist exercise rather than an ongoing process. Companies will assess a vendor thoroughly before signing the contract, then never look at them again until something goes wrong. Vendor risk changes over time: they get breached, lose certifications, get acquired, change their technology stack, add new subcontractors. A program that doesn't include continuous monitoring and periodic reassessment is essentially flying blind. The second biggest mistake is not tiering vendors by risk and wasting resources assessing low-risk vendors as thoroughly as critical ones. Focus your effort where it matters most.
How does TPRM fit with compliance frameworks like SOC 2 and ISO 27001?
Most compliance frameworks explicitly require vendor risk management. SOC 2 includes trust service criteria about monitoring vendor performance and ensuring vendors meet your control objectives. ISO 27001:2022 has specific controls in Annex A for supplier relationships (5.19, 5.20, 5.21) covering security agreements, monitoring, and managing changes. PCI DSS 4.0 has detailed requirements for managing third-party service providers (TPSPs) that handle cardholder data. HIPAA requires Business Associate Agreements and oversight of anyone who handles PHI on your behalf. Building a solid TPRM program not only reduces risk but also helps you meet these compliance requirements more efficiently. Auditors want to see evidence that you're actively managing vendor risks throughout the relationship lifecycle.
What role does AI play in modern TPRM?
AI is starting to transform several aspects of third-party risk management. Automated questionnaire processing: AI can help answer repetitive security questionnaires by pulling from your documented controls and policies, reducing response time from days to minutes. Risk scoring and analysis: AI can analyze vendor responses, certifications, and external signals to generate risk scores more consistently than manual review. Threat intelligence: AI-powered tools can monitor darknet chatter, breach databases, and news feeds to alert you when a vendor appears in a negative context. Natural language processing: AI can extract relevant information from vendor contracts, policies, and documentation to identify gaps or inconsistencies. While AI adoption in TPRM is still relatively early (about 5% of organizations currently use it), the technology is maturing quickly and showing real potential to make vendor oversight faster and more effective.
Conclusion: Make Third-Party Risk Management Your Competitive Advantage
In an era where companies rely on a complex web of vendors and partners, third-party risk management has become as fundamental as securing your own network. Your security is only as strong as your weakest link, and often that weakest link lies outside your walls.
TPRM is about shining a light on those shadowy corners of risk: the outsourced processes, the cloud services, the suppliers. A well-run TPRM program gives you visibility into who your third parties are, how they're performing, and what threats might be coming down the line. This allows you to act before small issues become crises.
The effort is well worth it. Organizations with mature TPRM report far fewer surprises and recover faster from incidents than those taking a passive approach. Strong third-party risk controls are increasingly a market differentiator. Business customers and regulators feel more confident when you can demonstrate a robust vendor management process.
Conversely, failing to manage third-party risk can mean severe consequences: multi-million dollar breaches, legal penalties, and loss of customer trust.
If your team is just starting to formalize third-party risk management, focus on the fundamentals:
- Get an inventory of vendors
- Assess them rigorously (especially the high-risk ones)
- Close any gaps with contracts and remediation
- Monitor continuously
Use available resources to accelerate your program. For example, Comp AI's free Third-Party Risk Policy Generator can instantly create a tailored policy framework to kickstart your program.
Consider modern TPRM tools or platforms that can automate assessments and watch your vendor landscape in real time, since scaling the program manually becomes tough as the number of third parties grows.
Ultimately, third-party risk management is about resilience and accountability. It sends a message that your organization takes its extended ecosystem seriously and will not be caught off guard by someone else's mistake. By integrating TPRM into your overall risk strategy, you build a business that not only trusts its partners but also verifies that trust continuously.
In doing so, you safeguard what matters most: your data, your customers, your operations, and your hard-earned reputation.
Stay vigilant. Third-party risks will never be zero, but with diligent management, you can drive them down to an acceptable level and avoid most disasters. As threats evolve and your vendor list changes, keep reviewing and refining your TPRM practices.
In the long run, a proactive approach to third-party risk is far easier and cheaper than reacting to the fallout of a major vendor-related incident. With the right processes and tools in place, you can confidently embrace the benefits of outsourcing and partnerships without leaving your organization exposed.
Share this article
Help others discover this content