Your Essential Data Breach Response Plan Template
Build a robust data breach response plan template with our expert guide. Learn to manage incidents, protect your business, and maintain customer trust.
- Home
- Compliance HubHub
- Your Essential Data Breach Response Plan Template
Having a data breach response plan isn't just checking a box—it's the difference between managed crisis and total chaos. Think of it as a strategic blueprint that guides your team through those first critical moments, helping you contain the threat, sidestep legal nightmares, and hold onto your customers' trust.
Honestly, it’s what separates a controlled recovery from a catastrophic failure.
Why a Response Plan Is Non-Negotiable

The moments after you discover a breach are pure, high-stakes confusion. Without a clear plan, teams scramble, critical evidence gets wiped, and the window to contain the damage slams shut. Fast.
A solid data breach response plan template flips the script, moving your organization from reactive panic to proactive control. It’s not about foolishly thinking you can prevent every single attack. It's about ensuring your response is swift, effective, and predictable when one inevitably gets through.
The Staggering Cost of Unpreparedness
Let’s talk numbers, because the financial fallout from a disorganized response is crippling.
Globally, the average cost of a data breach has hit $4.44 million. Here in the United States, that number skyrockets to an insane $10.22 million per incident. A well-rehearsed plan directly shrinks these figures by shortening the incident lifecycle. The average time to spot and contain a breach recently dropped to 241 days, proving that prepared companies act faster and mitigate damage more effectively.
An untested plan is just a document. An executed plan is a shield for your revenue, reputation, and regulatory standing. It ensures every action you take is deliberate, documented, and defensible.
This proactive approach also dramatically reduces your legal exposure. Regulations like GDPR and CCPA come with tight notification deadlines and eye-watering fines for non-compliance. Your plan makes sure you hit those deadlines, helping you avoid penalties that can tack on millions to the final bill.
Preserving Your Most Valuable Asset
Beyond the dollars and cents, a botched response erodes customer trust—an asset that can take years, if ever, to rebuild. When customers feel their data isn't safe, they walk. A clear, transparent communication strategy, baked right into your response plan, is your best tool for managing public perception and keeping your customer base loyal.
A good plan also clears up who does what. It assigns clear roles and responsibilities across IT, legal, HR, and communications, preventing internal chaos and ensuring everyone presents a unified front. For a deeper dive into building that kind of defense, check out this comprehensive data breach response plan guide .
And don't forget your supply chain. Managing vendors is a huge piece of the puzzle, which is why effective third-party risk management is so critical. At the end of the day, you're preparing for a "when," not an "if."
Deconstructing an Effective Response Plan
Alright, let's move past the theory and get our hands dirty building a practical blueprint. A truly world-class data breach response plan template isn't just one document; it's a strategic architecture designed for resilience. It’s what guides your team from that first gut-wrenching hint of trouble all the way through to a full recovery.
The plan has to cover a few core phases: detection and analysis, containment and eradication, and finally, post-incident recovery. Each of these stages needs clearly defined roles, pre-approved actions, and solid communication channels. Think of it as building the muscle memory your organization will desperately need when the pressure is on.
The Foundation: People and Protocols
Before you can respond to a single alert, you need to know who's in charge and how they'll talk to each other. This is the foundational layer where so many generic templates completely miss the mark, leading to chaos when every single second counts.
This infographic nails the first three critical steps for setting up your response infrastructure.
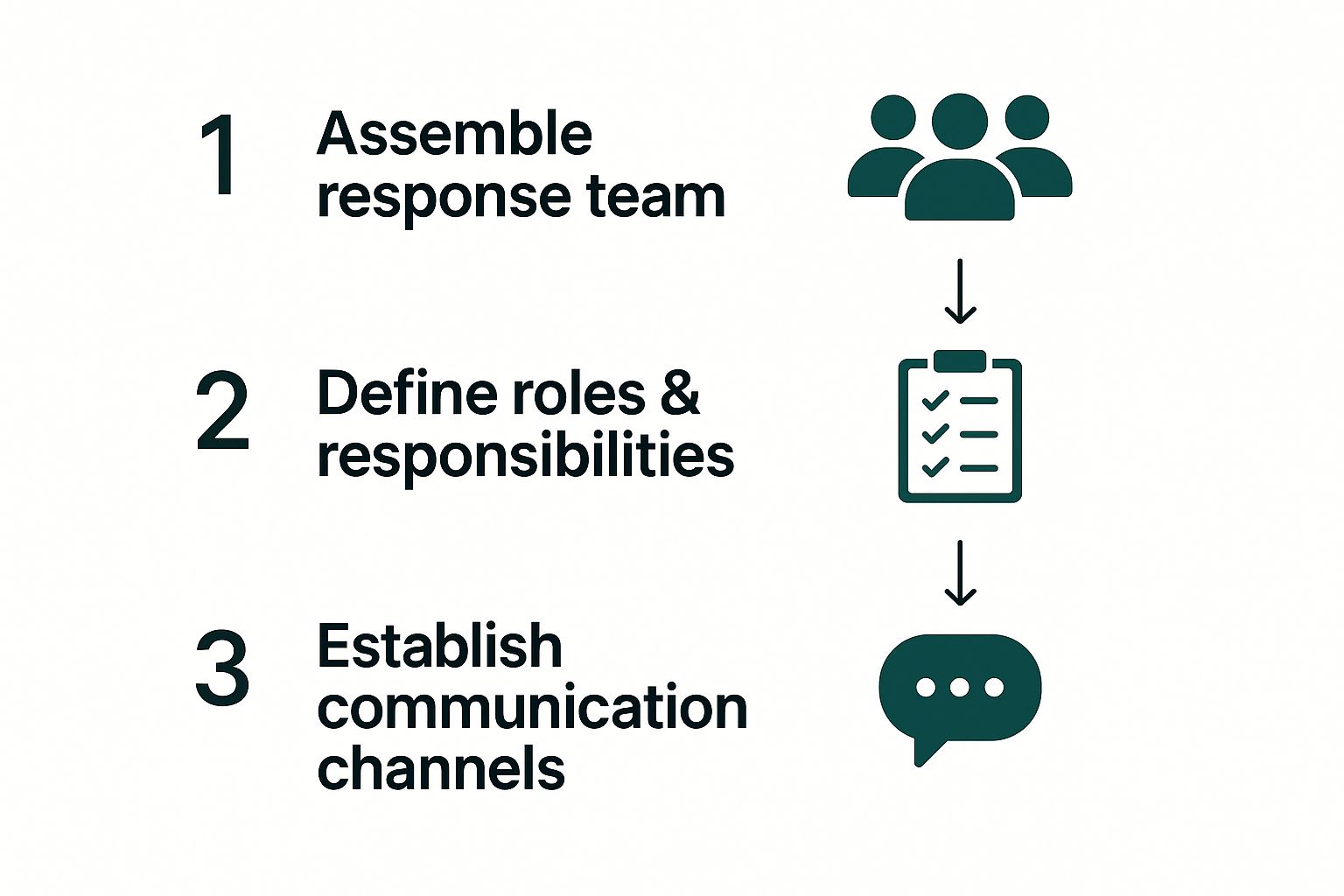
What I love about this flow is that it puts people first. Technology comes second to a well-organized human response. Always remember: a solid plan starts with people, not software.
Detection and Analysis
You can't fight an enemy you don't understand. This phase is all about speed—rapidly identifying an incident, figuring out its scope, and classifying just how bad it is.
Modern breach analysis shows that system intrusions make up 53% of breaches, with phishing involved in 16% and credential abuse in 22%. These numbers tell you that you need specific playbooks for different attack vectors. A phishing attack isn't the same as a server compromise.
Your plan needs to spell out:
- Incident Triage: A simple checklist for the first responders to quickly sort out if an alert is a false alarm or a genuine threat.
- Escalation Triggers: Clear, no-nonsense thresholds for when an issue has to get kicked up from the IT helpdesk to the core incident response team.
- Evidence Preservation: Strict rules on how to handle affected systems. You need to prevent well-meaning team members from accidentally wiping crucial forensic data in a panic.
The goal of the analysis phase isn't to solve the breach—it's to define its boundaries. A rushed diagnosis almost always leads to a botched containment effort.
Containment, Eradication, and Recovery
Once you know what you're dealing with, it's time to act. This part of your plan is the technical heart of the response, focused on stopping the bleeding and getting back to business.
Containment is about isolating the problem—think disconnecting a server from the network or disabling compromised user accounts. Eradication means kicking the attacker and their tools out of your environment for good. Finally, recovery involves restoring systems from clean backups and double-checking their integrity before bringing them back online.
Every action here has to line up with legal and ethical standards, which should be laid out in your organization's privacy policy .
If you want to see how these pieces all fit together in a broader context, you can explore our complete incident response policy . It’s a great way to visualize the entire lifecycle.
This methodical, phased approach turns your plan from an overwhelming document into a truly actionable guide for when things go sideways.
From Template to Actionable Plan
Grabbing a template is a great first step, but let’s be real—it's just the starting blocks. The real race begins when you start molding that generic document into a living, breathing plan that actually fits your company.
This isn’t about just filling in some blanks. It's about thinking strategically and mapping the template’s framework onto your actual operations. A plan that doesn’t know your specific tech stack, data flows, or team structure is pretty much guaranteed to fall apart under pressure.
Identify Your Crown Jewels
First things first: you can't protect what you don't know you have. Before you do anything else, you need to conduct a thorough inventory of your digital assets. This is more than a simple list of servers—it’s a deep dive into what information is most valuable, or what would be most dangerous if it got out.
Take a hard look at where your most sensitive data lives. We're talking about:
- Customer PII: Names, addresses, payment info, and contact details.
- Employee Records: Social Security numbers, payroll data, and healthcare information.
- Intellectual Property: Your proprietary code, trade secrets, and strategic business plans.
- Operational Data: Things like system configurations and network credentials.
When you know exactly what you’re protecting, you can prioritize your response. During a breach, you’ll know instantly which systems need to be locked down right now to stop the bleeding. This asset inventory also directly informs your recovery strategy, which is why a solid backup and recovery policy is the perfect companion to your response plan.
A data breach response plan built without a clear asset inventory is like a firefighter trying to save a building without knowing where the most flammable materials are stored. You're just guessing.
Assemble and Empower Your Response Team
Your plan is just a piece of paper without the right people to bring it to life. Putting together your response team is one of the most critical parts of customizing your template. And this isn't a task force you create during a crisis; they need to be defined, trained, and ready to go at a moment's notice.
A classic mistake is making the team too IT-centric. A real breach response takes a cross-functional village, with each person having clearly defined roles and the authority to act.
Your Core Response Team Roster
| Role | Primary Responsibility | Example Action |
|---|---|---|
| Incident Lead | Coordinates the entire response, acting as the central point of contact for all technical and operational efforts. | Authorizes network segmentation to isolate affected systems. |
| Legal Counsel | Manages legal risks, advises on regulatory notification duties, and handles all things compliance. | Determines if the breach triggers GDPR's 72-hour notification rule. |
| Communications | Drafts and sends out all internal and external communications about the incident. | Prepares a customer notification email and an internal employee update. |
| HR Lead | Manages employee-related issues, like compromised employee data or even insider threats. | Communicates with affected staff and offers identity theft protection services. |
Tailoring Your Plan for Your Industry
A generic data breach response plan template is a starting point, not the finish line. Frankly, using one off-the-shelf is like a doctor prescribing the same medicine to every patient—it’s not just ineffective, it’s downright dangerous. The threats, data, and legal obligations facing a small e-commerce shop are a world away from those of a massive healthcare provider.
Your industry ultimately dictates your risks and responsibilities. A financial firm’s worst nightmare is probably compromised banking details. A tech company, on the other hand, might lose sleep over stolen intellectual property. Tailoring your plan means mapping it directly to the ground truth of how your business actually operates.
Regulations Shape Your Response
Let's be clear: compliance isn't optional. It's a core driver of how your response plan needs to be structured. Different industries answer to different regulators, each with its own non-negotiable breach notification timelines and eye-watering penalties.
- Healthcare (HIPAA): The Health Insurance Portability and Accountability Act gives you a bit of breathing room, demanding notification to affected individuals without unreasonable delay, but no later than 60 days after discovery.
- Finance (NYDFS): The New York Department of Financial Services Cybersecurity Regulation is much tighter, with a strict 72-hour notification requirement for specific types of incidents.
- Global Operations (GDPR): If you handle data from EU citizens, the General Data Protection Regulation also enforces a 72-hour notification window to the supervisory authority.
These aren't suggestions; they are hard deadlines. Your entire response plan has to be built to meet them, setting the pace and flow for all your internal processes. Just figuring out which regulations apply to you is the first real step in building a legally defensible plan.
Data Types and Third-Party Risks
The kind of data you handle directly impacts your containment strategy. A breach involving anonymized user analytics is a headache; a breach exposing sensitive Personally Identifiable Information (PII) is a full-blown crisis. Your plan has to classify data by sensitivity and define the right response level for each. It's also why your policies for managing that data in the first place are so critical—having solid data retention policy examples helps you minimize your attack surface from the get-go.
And your risk doesn't stop at your own firewall. Cyberattacks are getting more complex and often snake their way in through third-party vendors. A perfect example is the Oracle Cloud breach that hit over 140,000 tenants when crucial credentials and keys were stolen. It was a massive wake-up call about the risk posed by cloud providers.
A modern response plan absolutely must include protocols for incidents involving your key vendors. You need to detail exactly how you'll coordinate with them to shut down a threat.
Your response plan isn't just about your organization; it's an ecosystem plan. It must account for every partner, vendor, and cloud service that touches your critical data, treating their security as an extension of your own.
Testing and Refining Your Response Plan

Creating your data breach response plan is a huge step, but an untested document is just a theory. Think of it like a fire extinguisher you've never checked; you’re just hoping it works when you see smoke. To make your plan genuinely resilient, you have to put it under pressure, find the weak spots, and constantly make it better.
This cycle of testing and improving is what transforms a good plan into a bulletproof one. It builds the critical muscle memory your team needs to act decisively—not frantically—when a real incident hits.
Choosing the Right Testing Method
Not all tests are created equal, and you don’t have to jump straight into a full-blown simulation that feels like a scene from a hacker movie. The key is to pick an approach that matches your team's maturity and resources. Start simple and work your way up.
Different situations call for different drills. Here’s a quick rundown of your options:
Data Breach Response Plan Testing Methods
| Testing Method | Description | Best For |
|---|---|---|
| Tabletop Exercise | A guided discussion where the response team talks through a simulated breach scenario. It's a low-stress way to check roles and communication plans. | Teams new to incident response, identifying high-level gaps, and getting everyone on the same page without a huge time investment. |
| Walk-through Drill | A step up from a tabletop, where team members actually perform simple tasks from the plan, like drafting a mock notification email or checking a specific system log. | Verifying that people not only know what to do but also how to do it. It tests practical skills on a smaller scale. |
| Full-Scale Simulation | The most intense test, mimicking a live attack. This often involves ethical hackers (a "red team") to see how your people, processes, and tech hold up under real pressure. | Mature teams looking to pressure-test their entire security posture, including technical defenses and human responses in real-time. |
Learning from Drills and Real Incidents
The single most valuable part of any test is the debrief afterward. Once the drill is over, gather everyone involved for an open, blameless discussion about what went right and what went wrong. The goal isn't to point fingers but to uncover opportunities for improvement.
An effective post-mortem turns every mistake into a lesson. It’s where you identify process bottlenecks, communication failures, and technical gaps before a real attacker does.
Document these findings like your business depends on it—because it does. Was the legal team slow to get back? Did IT struggle to isolate the right server? These observations are pure gold, and they become the fuel for the next version of your data breach response plan template.
This continuous loop—test, review, refine, repeat—is non-negotiable. You should schedule reviews for your plan at least annually, or immediately after any significant organizational change, like adopting new tech or restructuring a team. Threats are always evolving, and your defense has to keep pace.
Common Questions About Data Breach Plans
Even with a rock-solid data breach response plan template, questions always come up. Getting the answers right is what turns a document on a shelf into a real-world, confident response when things go sideways. It’s all about creating clarity before a crisis hits.
Let’s dig into some of the most common questions teams ask when they’re building out their plans. These insights can help you patch up common holes and make sure everyone is actually ready to move.
How Often Should We Update Our Plan?
Think of your response plan as a living document, not a project you finish and forget. At a bare minimum, it needs a thorough review at least once a year. But honestly, the real trigger for an update is change.
Any time your business goes through a significant shift, the plan needs a refresh. This includes stuff like:
- Rolling out major new technologies or moving to a different cloud platform.
- Key people on your response team leaving or changing roles.
- New data privacy laws (like GDPR or CCPA updates) coming on the scene.
- Changing how your company gathers or handles sensitive customer data.
And here’s the most critical part: always, always update the plan right after a drill or, heaven forbid, a real incident. That’s when the lessons are fresh and you have the best chance to harden your defenses based on what you just learned.
Who Are the Non-Negotiable Team Members?
Your full-blown incident response team might have a dozen people, but a few roles are absolutely essential. If you don't have these key players at the table from minute one, a coordinated response is pretty much a fantasy.
Your core team has to include:
- An Incident Lead: This is usually someone from your IT or security team who can quarterback the entire technical side of the response.
- A Legal/Compliance Rep: This person is your guide through the minefield of legal risks and mandatory breach notification laws. You can’t afford to guess here.
- A Communications Lead: This role owns the narrative, managing everything from internal updates to external statements to keep panic and misinformation at bay.
For most companies, you’ll also want an executive leader on this core team. They have the authority to make big, fast, and sometimes expensive decisions without getting bogged down in red tape.
The single biggest mistake is making the team too IT-focused. A breach is a business crisis, not just a technical problem, and your team must reflect that reality from day one.
What Is the Most Important First Step?
The moment you even suspect a breach, the most important first step is to activate your response plan and get your core team on a call immediately. This stops people from making panicked, freelance decisions that could destroy evidence or make the situation a whole lot worse.
That team's first job isn't to sound the alarms—it's to quietly confirm if a breach actually happened and get a handle on the initial blast radius. That means no yanking servers offline or sending company-wide alerts that could tip off an attacker who's still in your network. The priority is to isolate the affected systems while starting the documentation process with painstaking detail.
--- Ready to build a compliance program that makes audit readiness effortless? Comp AI centralizes your controls, automates evidence collection, and provides expert guidance to get you SOC 2, ISO 27001, or HIPAA ready in a fraction of the time. Learn more about Comp AI .
Share this article
Help others discover this content
More from Compliance Hub
Explore more insights and stay ahead of regulatory requirements.
7 Data Retention Policy Examples to Implement in 2025
Explore 7 real-world data retention policy examples. Learn how to implement time-based, event-based, and value-based policies for optimal compliance.
12 Best Penetration Testing Tools for Security Pros in 2025
Discover the 12 best penetration testing tools of 2025. In-depth reviews of Burp Suite, Metasploit, Nessus, and more for ethical hacking.
How to Get SOC 2 Certification The Smart Way
Learn how to get SOC 2 certification with our guide. We cover everything from readiness to audit, using automation to simplify the entire compliance process.