Best Penetration Testing Tools for 2025
Compare the best penetration testing tools for 2025. Expert reviews, current pricing, and real recommendations for web apps, networks, and cloud security.
- Home
- Compliance HubHub
- Best Penetration Testing Tools for 2025
Finding vulnerabilities before hackers do isn't optional anymore. It's the difference between catching a breach during your pentest and explaining one to your customers (or worse, regulators). But here's the reality: with hundreds of security tools out there, figuring out which penetration testing tools will actually protect your systems can feel overwhelming. We've cut through the noise.
This guide covers the best penetration testing tools in 2025, from free open-source options to enterprise-grade platforms. You'll learn what each tool does well, where it falls short, current pricing (verified for 2024-2025), and how they fit into a modern security program. Whether you're a startup CTO building your first security stack or a seasoned security engineer refining your toolkit, you'll find actionable insights here.

What Makes a Penetration Testing Tool "The Best" in 2025?
Before diving into specific tools, let's get clear on what we're looking for. The best pentest tools share these traits:
Current and maintained: Active development with regular updates for new vulnerabilities and attack techniques. Tools with stale signatures miss emerging threats.
Proven coverage: Finds real security issues across your specific environment (web apps, networks, cloud, APIs). Coverage is only valuable if it applies to your stack.
Practical workflows: Integrates into your existing processes without massive overhead. If it takes six months to operationalize, it's not helping.
Clear value: Either saves significant time, finds issues others miss, or both. You need measurable security improvement.
Transparent pricing: You can actually budget for it without three sales calls (when possible). Hidden costs kill security budgets.
Throughout this guide, we'll evaluate tools against these criteria and give you the truth about what each one delivers.

Penetration Testing Tools by Category: Quick Navigation
If you're building from scratch: Start with Best Web Application Security Testing Tools for 2025 and Best Vulnerability Scanning Tools for 2025
If you need breadth fast: Jump to Best External Attack Surface Management (EASM) Tools
If you're going deep on exploitation: Check out Best Exploitation and Post-Exploitation Frameworks for Red Teams
If you're securing code: Head to Best Static Analysis and Code Security Tools (SAST)
Best Web Application Security Testing Tools for 2025
Web applications remain the primary attack vector for most organizations. These tools help you find and fix vulnerabilities before attackers exploit them.
Burp Suite Professional: Why It's the Web App Testing Standard
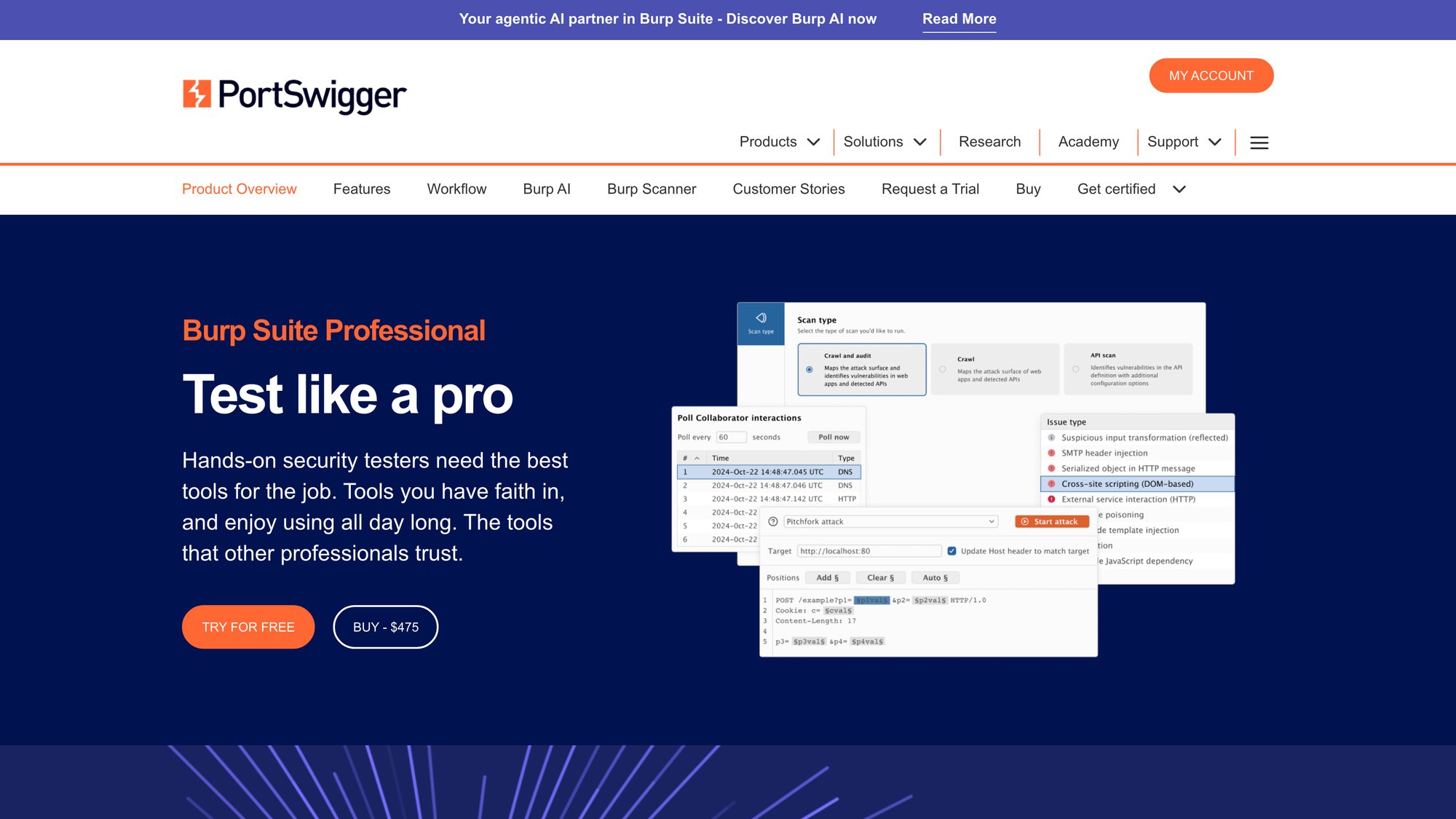
Burp Suite has been the go-to tool for web application penetration testing for years, and for good reason. The Professional edition combines an intercepting proxy, automated scanner, and manual testing tools (Intruder, Repeater, Decoder) into one powerful package.
Why security pros choose it: Burp's strength lies in manual testing capabilities. You can intercept and modify HTTP/HTTPS traffic, test authentication flows, probe for injection vulnerabilities, and build custom attacks through its Extender API and BApp Store extensions. The scanner component handles automated testing of OWASP Top 10 vulnerabilities with impressively low false positive rates.
Current pricing: $475 per user per year for Burp Suite Professional. Enterprise Edition (for automated CI/CD integration and team workflows) starts around $6,040 annually, with unlimited concurrent scanning packages reaching about $49,000.
Best for: Individual security engineers and AppSec teams who need surgical control over web app testing. If you're testing complex authentication, APIs, or modern single-page applications, Burp Pro is worth every penny.
Limitations: The learning curve is steep if you're new to web security. Enterprise edition pricing scales quickly for larger teams. You'll need expertise to use it effectively (it's a professional tool that assumes security knowledge).
OWASP ZAP: Best Free Alternative to Burp Suite

OWASP ZAP (Zed Attack Proxy) is the leading open-source web application security scanner. It's free, actively maintained, and included in penetration testing distributions like Kali Linux.
What it does well: ZAP provides both automated scanning and manual testing through its proxy interface. The active scanner catches common vulnerabilities, passive scanners identify issues without intrusive testing, and the authentication engine handles complex login scenarios. For DevSecOps teams, ZAP integrates cleanly into CI/CD pipelines with Docker containers and command-line automation.
Current version: ZAP 2.16.1 (released March 25, 2025) with continued active development.
Best for: Teams standardizing on open-source tools, security engineers who need baseline web app scanning in CI pipelines, and organizations with tight budgets who still need solid web security testing.
Trade-offs: Compared to Burp Suite, ZAP has a less polished interface and can produce more false positives. The extension ecosystem isn't as mature. But for finding common web vulnerabilities at zero cost, it's unbeatable.
Acunetix by Invicti: Enterprise Web Vulnerability Scanner

Acunetix (now part of Invicti Security) focuses on automated web vulnerability scanning with a twist: proof-based scanning. Rather than just flagging potential issues, Acunetix can safely exploit certain vulnerabilities to prove they're real, significantly reducing false positives.
Standout features: Deep crawling of modern web apps (including JavaScript-heavy single-page applications), over 3,000 vulnerability tests, out-of-band detection for blind vulnerabilities, and the ability to confirm SQL injection by safely extracting proof. The platform combines DAST (dynamic testing) with IAST (interactive testing) when you can instrument your application.
Pricing: Starts at about $4,500 per year for 5 websites, scaling to around $26,000 for 50 sites. No per-user limits on the platform itself.
Ideal users: Mid-size to enterprise organizations needing to scan dozens or hundreds of web applications efficiently. The proof-based approach means security teams spend less time validating findings and more time fixing real issues.
Watch out for: Fully automated testing won't catch business logic flaws or design-level security issues. You'll still need manual testing for full coverage.
Intruder: Cloud-Based Vulnerability Scanner for Startups
Intruder represents the newer wave of cloud-based vulnerability management platforms. Point it at your external infrastructure and web apps, and it continuously scans for vulnerabilities, misconfigurations, and emerging threats.
Why startups love it: Zero installation, simple setup, automatic scanning schedules, and compliance integrations with platforms like Drata and Vanta. Intruder automatically sends scan reports as audit evidence for SOC 2 and ISO 27001, which saves countless hours during certification.
Pricing: Essential plan starts at $108 per month for up to 5 targets. Pro and Cloud tiers add features like internal network scanning and cloud account security checks, typically ranging from $180 to $300+ monthly depending on your environment size.
Best for: Tech startups and growing companies that need to demonstrate continuous vulnerability management for compliance but don't have dedicated security teams. If you're working toward SOC 2 certification, Intruder's automated compliance reporting is incredibly valuable.
Limitations: Being fully automated, it won't find complex logic vulnerabilities that require human intuition. Think of it as your always-on first line of defense, not a replacement for skilled penetration testers.
Astra Pentest: Continuous Penetration Testing as a Service (PTaaS)
Astra blends automated scanning with human security expertise delivered through a SaaS platform. It's Penetration Testing as a Service (PTaaS) designed for continuous security rather than annual point-in-time tests.
What sets it apart: You get automated DAST scans plus manual penetration testing from Astra's security engineers, all through one dashboard. Their approach aligns with modern DevOps: test continuously as you release, not once a year.
Pricing: Scanner plans start at $199 per month per web app (unlimited scans plus 4 expert manual rechecks annually). Full pentest-as-a-service runs about $5,999 per application per year, including one thorough manual pentest plus continuous automated scanning.
Compliance value: Astra's reports explicitly map to SOC 2, PCI DSS, and ISO 27001 requirements. Auditors recognize their testing, and you get an engagement letter immediately (useful for proving you've engaged professional pentesting for compliance).
Best suited for: SaaS companies, fintech startups, and businesses that ship code frequently. If you're doing Agile releases and need security testing that keeps pace, Astra's continuous model makes sense.
Consider this: For organizations only needing one-off annual tests, traditional consulting might be more cost-effective than a year-round subscription.
Nuclei: Fast Template-Based Vulnerability Scanner
ProjectDiscovery's Nuclei has exploded in popularity for good reason. It's a lightning-fast vulnerability scanner that uses YAML templates to define checks. With thousands of community templates covering CVEs, misconfigurations, and security issues, you can scan your entire attack surface quickly.
Practical use: Run Nuclei as your first pass to catch obvious issues (exposed admin panels, known CVE exploits, common misconfigurations). Then follow up with deeper manual testing on the interesting findings. Many teams run Nuclei nightly to catch regression or new exposures.
Pricing: Free and open source. Templates are community-maintained and continuously updated for 2025 CVEs.
Perfect for: Perimeter security, regression testing between manual pentests, and finding quick wins before dedicating time to deep testing.
Keep in mind: Templates can only catch known patterns. Novel vulnerabilities and complex business logic flaws require human analysis.
Best Vulnerability Scanning Tools for 2025
Vulnerability scanners provide breadth across your infrastructure. They're not substitutes for penetration testing, but they're necessary for continuous security monitoring.
Tenable Nessus: Industry-Standard Vulnerability Scanner
Nessus remains the industry standard for vulnerability assessment. With over 68,000 vulnerability checks and decades of development, it's trusted by organizations worldwide.
What it delivers: Thorough vulnerability scanning across servers, network devices, databases, and workstations. Nessus detects missing patches, misconfigurations, weak services, and compliance violations. The plugin database updates frequently, and reports can be customized for different compliance frameworks (CIS benchmarks, PCI DSS, etc.).
Current pricing: Nessus Professional is $4,390 for a 1-year license (as of July 2024). Nessus Expert adds cloud infrastructure assessment and external scanning capabilities for $6,390 annually.
Ideal for: IT security teams performing routine vulnerability assessments, organizations with PCI DSS requirements (which mandate regular scanning), and anyone needing reliable infrastructure vulnerability detection.
Strategic use: Run Nessus scans before penetration tests to clean up obvious issues, allowing pentesters to focus on complex exploitation. Re-scan after remediation to prove vulnerabilities are fixed.
Limitations: Nessus identifies and reports vulnerabilities but doesn't exploit them. You'll need additional tools (like Metasploit) to validate impact. Scanning large environments can be resource-intensive if not tuned properly.
Qualys VM: Cloud-Based Enterprise Vulnerability Management
QualysGuard offers cloud-managed vulnerability scanning with global reach. Deploy lightweight scanners anywhere, manage everything from a central cloud platform.
Enterprise strengths: Excellent for organizations with distributed infrastructure. Features like continuous asset discovery, automated scan scheduling, and integration with enterprise ticketing systems make it powerful at scale. The PCI Compliance module handles external scans and generates submission-ready reports.
Pricing model: Typically subscription-based, about $200-300 per asset per year for vulnerability management. Volume discounts available, and bundling with web app scanning and compliance modules is common.
Best suited for: Large enterprises managing thousands of assets across multiple locations. If you need centralized visibility and orchestration of security scanning worldwide, Qualys excels.
Consider: The interface can feel complex for smaller teams. For startups, Nessus's simplicity might be preferable.
Best Static Analysis and Code Security Tools (SAST)
Catching vulnerabilities during development (before they reach production) is far cheaper than finding them in production. Static Application Security Testing (SAST) tools scan source code and binaries for security flaws.
Aikido Security: Unified Code-to-Cloud Security Platform
Aikido represents a newer approach: combining SAST, Software Composition Analysis (dependency scanning), secret scanning, cloud configuration checks, and DAST in one platform. Think of it as thorough AppSec coverage from your code repositories through your cloud deployments.
What it covers: Code scanning for vulnerabilities, open-source dependency analysis, hardcoded secret detection, cloud misconfigurations (via CSPM), and even autonomous penetration testing driven by AI.
Pricing: Basic tier is about $350 per month for up to 10 users, Pro tier around $700 monthly. A free tier exists for small projects.
Value proposition: Instead of juggling separate tools for code scanning, dependency checks, and cloud security, you get unified visibility. The AI AutoFix feature can even generate one-click remediation for certain findings.
Trade-offs: As a newer platform, it might lack the depth of best-of-breed dedicated SAST tools for specific languages. But for DevSecOps teams wanting broad coverage with less tool sprawl, it's compelling.
Checkmarx, Veracode, and GitHub Advanced Security: Enterprise SAST Tools
Enterprise organizations have long relied on tools like Checkmarx CxSAST and Veracode Static Analysis. These integrate into the software development lifecycle, scanning code in IDEs, pull requests, and CI pipelines.
Modern SAST features: AI-assisted false positive reduction, integration with developer workflows (GitHub code scanning alerts), precise remediation guidance, and support for dozens of programming languages.
Example pricing: GitHub Advanced Security (which includes CodeQL scanning) costs about $49 per developer per month on GitHub Enterprise Cloud. Traditional SAST licenses often run tens of thousands annually depending on applications and code volume.
Strategic value: SAST finds issues pentesters might not catch, like subtle data leakage patterns, weak cryptography usage, or hardcoded credentials. For compliance frameworks (ISO 27001, SOC 2), demonstrating secure coding practices through SAST is valuable evidence.
Reality check: SAST produces false positives and can miss runtime-only issues. Combine it with DAST and manual testing for thorough coverage.
Best External Attack Surface Management (EASM) Tools
Your attack surface constantly changes as you launch new services, acquire companies, or migrate to cloud. EASM platforms continuously discover and assess your external-facing assets from an attacker's perspective.
CyCognito: Enterprise Attack Surface Management Platform
CyCognito uses "seedless discovery" to map your entire internet-facing attack surface starting with minimal information (just your company name). It finds assets you didn't even know you had, tests them for vulnerabilities, and prioritizes risks by actual exploitability.
Core capabilities: Autonomous asset discovery across subsidiaries and cloud providers, continuous vulnerability testing on discovered assets, risk prioritization based on attacker attractiveness and exploitability, and integration with security workflows.
Pricing expectations: Typically tens of thousands of dollars annually for mid-size deployments, scaling into six figures for large enterprises. Quote-based on your asset footprint.
Perfect for: Large enterprises with complex IT estates, organizations that have grown through acquisitions, and security teams that need to answer "what does an attacker see when they look at us?"
Compliance angle: Helps satisfy requirements around continuous monitoring and asset inventory (ISO 27001, NIST frameworks). You can demonstrate proactive external risk management to auditors.
Not ideal for: Very small organizations with simple infrastructure. The platform's power shines when you have a sprawling attack surface to monitor.
Best Network and Infrastructure Penetration Testing Tools
Not all attacks target web applications. Network pentesting tools help assess servers, services, wireless networks, and internal infrastructure.
Nmap: Network Scanning and Reconnaissance Tool

Nmap (Network Mapper) remains indispensable after decades. The latest version (7.98, released August 12, 2025) includes modern NSE scripts for service detection, vulnerability checks, and protocol analysis.
Why it's foundational: Before you exploit anything, you need to understand what's running where. Nmap's service fingerprinting, version detection, and scriptable checks (NSE) provide that context. Practically every penetration test starts with Nmap scans.
Pricing: Free and open source.
The Nmap project has been the gold standard for network reconnaissance since 1997. The official homepage showcases its extensive documentation, active development, and trusted community support:
Use cases: Network discovery, service enumeration, OS fingerprinting, and targeted vulnerability checks via NSE scripts.
Pro tip: Export Nmap results and feed them into specialized tools like Nuclei or targeted Burp/Metasploit sessions for efficient testing workflows.
Metasploit Framework: Open-Source Exploitation Tool

Metasploit is the canonical framework for exploit development and validation. With over 2,000 exploits, post-exploitation modules, and the powerful Meterpreter payload, it's how security pros prove vulnerabilities are actually exploitable.
Real-world use: Find a vulnerability with Nessus, validate it's exploitable with Metasploit. Demonstrate to stakeholders that theoretical findings have real impact. Use post-exploitation modules to show what an attacker could do after initial compromise.
Pricing: Free and open source, with active development and weekly updates through 2025.
Metasploit remains the most powerful open-source penetration testing framework. The official site demonstrates its extensive module library and professional security testing capabilities:
Ideal users: Experienced penetration testers and security engineers who need to validate findings or demonstrate risk to executives (nothing says "urgent" like showing an exploit in action).
Important note: Metasploit is powerful and can cause system instability if misused. Only use it on systems you're authorized to test, with proper safeguards in place.
Core Impact: Commercial Penetration Testing Platform
Core Impact is a commercial alternative to Metasploit, offering automated attack chains, team collaboration features, and polished reporting. Think of it as Metasploit with enterprise tooling.
What it costs: Basic edition starts at $9,450 per user annually. Pro edition (which bundles Cobalt Strike) runs $12,600 per user per year.
Why pay for it: Automation wizards that chain exploits, professional reporting templates, client-side testing capabilities, and integrated password cracking (CloudCypher). For consulting firms running multiple engagements, the efficiency gains can justify the cost.
Who should consider it: Professional pentest teams that value time savings and polished client deliverables over open-source flexibility.
Honest take: The feature gap between Metasploit (free) and Core Impact has narrowed. You're paying for convenience, support, and enterprise workflows rather than fundamentally different capabilities.
Aircrack-ng: Wireless Network Security Testing Tool
Aircrack-ng is the standard toolkit for wireless network security assessment. It captures packets, performs deauthentication attacks, and cracks WEP and WPA2-PSK encryption.
Practical application: Testing corporate Wi-Fi security during internal penetration tests. An attacker who compromises your wireless network can pivot into sensitive systems.
Pricing: Free and open source.
Use responsibly: Only test wireless networks you're explicitly authorized to assess. Deauth attacks can disrupt legitimate users.
Best Exploitation and Post-Exploitation Frameworks for Red Teams
Red team operations require sophisticated command-and-control (C2) frameworks to simulate advanced attackers.
Cobalt Strike: Professional Command and Control (C2) Framework

Cobalt Strike is the industry-leading post-exploitation platform. Its Beacon payload enables stealthy command-and-control, lateral movement, privilege escalation, and data exfiltration in ways that mimic real threat actors.
Why red teams use it: Mature operator workflows, team collaboration via team server, flexible C2 channels (HTTP, DNS, SMB), and the Aggressor scripting engine for automation. It's designed for realistic adversary simulation.
Pricing: Quote-based and varies by region. Some partners advertise pricing as low as $3,540 per user annually when bundled, but expect to pay more depending on your needs. Fortra (the vendor) vets buyers due to past misuse.
Critical for: Mature security teams running full-kill-chain exercises to test detection and response capabilities. If you need to evaluate how your SOC performs against advanced persistent threats, Cobalt Strike enables that testing.
⚠️ CRITICAL SECURITY WARNINGThis is dangerous software in the wrong hands. Strict rules of engagement, blue team coordination, and proper containment are *non-negotiable*.
Sliver and Mythic: Open-Source C2 Alternatives to Cobalt Strike
For teams that can't access Cobalt Strike, open-source options like Sliver (by BishopFox) and Mythic provide similar capabilities without the price tag or vendor vetting.
What they offer: Multiple implant types, flexible C2 profiles, and active development communities. Sliver, written in Go, is gaining traction in the security community.
Trade-offs: Less polished than commercial tools, smaller ecosystems, and you're responsible for maintaining and securing your own infrastructure.
How Penetration Testing Supports Compliance Programs (SOC 2, ISO 27001, HIPAA)
If you're pursuing SOC 2, ISO 27001, PCI DSS, or HIPAA compliance, penetration testing isn't optional. Here's how these tools help you meet requirements:
Penetration Testing Requirements for SOC 2 Compliance
Trust Service Criterion CC7.1 requires detecting and mitigating vulnerabilities. Satisfy this with:
Continuous scanning: Intruder or Nessus for regular vulnerability assessment that feeds into your risk management process.
Annual penetration testing: Tools like Astra, or engaging a professional pentest firm to validate your security controls work as intended.
Automated evidence: Intruder integrates with compliance platforms (Drata, Vanta) to automatically provide scan reports as audit evidence, saving massive manual work.
Many startups use Astra's PTaaS model to get audit-recognized pentest certificates annually, satisfying customer due diligence along with SOC 2 requirements.
ISO 27001 Penetration Testing Requirements
Annex A.12.6 (technical vulnerability management) and A.14 (secure development) drive testing requirements:
SAST in development: Aikido or Checkmarx demonstrate secure SDLC practices (A.14.2.8).
Regular vulnerability scanning: Nessus or Qualys with tracked remediation shows you're managing technical vulnerabilities (A.12.6.1).
Periodic penetration testing: Annual testing or after major changes validates your controls work in practice.
Intruder's compliance reporting templates can be used directly in ISO audits to show continuous scanning and improvement trends.
PCI DSS Penetration Testing Requirements
Payment Card Industry requirements are explicit about security testing:
Quarterly external scans: Qualys or Nessus can perform ASV (Approved Scanning Vendor) scans required by PCI.
Annual penetration testing: Requirement 11.3 demands manual penetration testing of applications and networks handling cardholder data.
Testing after changes: Any significant infrastructure or application changes require re-testing to validate security controls.
Tools like Acunetix can perform pre-pentest scanning to clean up low-hanging fruit before manual testing validates your cardholder data environment controls.
HIPAA Penetration Testing and Security Assessment Requirements
Healthcare organizations need to regularly evaluate technical safeguards protecting ePHI:
Risk assessments: Vulnerability scanning identifies technical risks to electronic protected health information.
Evidence for partners: Many healthcare companies use PTaaS platforms to generate attestation letters for business associates who ask "how do you test your security?"
Regular pentesting helps satisfy HIPAA's requirement for regular technical evaluations of safeguards.
How Comp AI Automates Compliance After Penetration Testing
Finding vulnerabilities is crucial, but so is proving you've addressed them for compliance. After you complete penetration testing and remediation, you'll face customer security questionnaires and audit evidence requests. This is where the real work begins for most teams.
Comp AI bridges the gap between security testing and compliance documentation. While penetration testing tools find and validate vulnerabilities, Comp AI automates the compliance side:
Evidence collection: Automatically gather proof that you've implemented security controls based on your pentest findings. User access logs, configuration screenshots, policy documentation, and remediation tracking all get collected without manual work.
Questionnaire responses: When customers ask "do you perform regular penetration testing?" or "how often do you scan for vulnerabilities?", Comp AI generates AI-powered answers based on your actual implemented controls and testing cadence.
Trust Center: Keep customers and auditors informed about your security posture in real-time. Show them your latest pentest results, remediation status, and continuous monitoring without sharing sensitive details.
The combination is powerful: penetration testing tools ensure your defenses actually work, while Comp AI proves it to stakeholders without drowning you in spreadsheets.
If you're working toward SOC 2, ISO 27001, or HIPAA compliance while running regular security testing, Comp AI can save hundreds of hours by automating the evidence and questionnaire burden that follows good security practices. Security teams spend less time on documentation, more time on actual security.
How to Build Your Penetration Testing Stack (4 Budget Options)
Your ideal toolkit depends on your environment, team expertise, and budget. Here are proven stacks for different scenarios:
Free Penetration Testing Tools Stack (Bootstrap Option)
For startups and teams just getting started:
Core tools:
- Nmap for network discovery
- OWASP ZAP for web app testing
- Nuclei for quick perimeter checks
- Metasploit for exploitation validation
- Wireshark for traffic analysis
What this gets you: Solid coverage across web, network, and exploitation with zero licensing costs. You're trading money for time (more manual work, less polished reporting), but the security value is real.
Best for: Early-stage startups, internal purple team pilots, security training environments, and teams learning penetration testing fundamentals.
Budget Penetration Testing Stack ($1,500-$2,500/year)
For individual consultants or lean security teams:

Add commercial tools where they matter: Burp Suite Professional ($475) for web app depth and speed, keep the free tools (Nmap, Metasploit, Nuclei) for specialized tasks. Consider modest spend on wordlists, DNS datasets, and threat intelligence feeds.
Value proposition: Professional-grade tools where they provide the most leverage (web testing), while maintaining cost efficiency. You'll be 2-3x faster on complex authentication flows, APIs, and chained logic bugs.
Best for: Security consultants, small AppSec teams, and growing companies starting to professionalize security testing.
Continuous Security Testing Stack for Compliance ($10,000+/year)
For growing companies with compliance requirements:
Build for automation:
- Intruder ($1,000-$2,000+/year) for automated external scanning and compliance reporting
- Astra PTaaS ($5,999+/year) for continuous testing with human expertise
- Aikido ($4,200+/year) for code-to-cloud security coverage
- Keep Burp Suite Pro, Nmap, and Metasploit for specialized testing
Strategic benefit: Automated continuous testing plus expert validation, with compliance evidence built in. This stack supports modern DevSecOps practices and satisfies audit requirements without massive manual overhead.
Best for: SaaS companies, fintech startups, and any business pursuing SOC 2 or ISO 27001 certification while maintaining rapid development velocity.
Enterprise Red Team Penetration Testing Stack ($25,000+/year)
For mature security programs:
Full-spectrum coverage:
- Nessus Expert or Qualys VM for enterprise-scale scanning
- Burp Suite Enterprise for automated web app security in CI/CD
- Cobalt Strike for adversary simulation
- CyCognito for attack surface management
- Optional: Core Impact for streamlined pentesting with polished deliverables
What this enables: Complete security testing from code to cloud, continuous monitoring of your entire attack surface, and realistic adversary simulation to validate your detection and response capabilities work under pressure.
Best for: Enterprises with mature security teams, organizations in highly regulated industries, and companies with sophisticated threat models requiring advanced red team capabilities.
Frequently Asked Questions About Penetration Testing Tools
Do I Need Commercial Penetration Testing Tools or Are Open-Source Tools Enough?
It depends on your priorities and resources. Open-source tools (ZAP, Metasploit, Nmap) provide excellent coverage at zero cost. Commercial tools buy you time savings through automation and polished interfaces, support when you hit issues, compliance-ready reporting, and integration with enterprise workflows.
For professional security teams where time is money, commercial tools often pay for themselves. For smaller organizations or individual learners, open source is incredibly powerful. Many teams use a hybrid approach: free tools for specialized tasks, commercial tools where efficiency matters most.
Can Automated Scans Replace Manual Penetration Testing?
No. A penetration test requires manual analysis and exploitation to demonstrate real impact and reduce false positives. Automated scanners are valuable for breadth and continuous monitoring, but they can't replace skilled human testing for depth and business logic vulnerabilities.
Think of scanners as your signal generators. Pentesters provide the signal quality and context. Scanners find potential issues; pentesters prove which ones matter and demonstrate how an attacker would chain them together.
How Often Should You Run Penetration Tests and Vulnerability Scans?
Recommended testing cadence for most organizations:
| Testing Type | Frequency | Purpose |
|---|---|---|
| Vulnerability scanning | Weekly or monthly | Catch new CVEs, validate patch management |
| Automated web scanning | With each major release or weekly | Catch regressions before production |
| Manual penetration testing | Annually minimum, or after significant changes | Deep validation, compliance requirements |
| Red team exercises | Annually for mature programs | Test detection and response capabilities |
Your specific requirements depend on compliance obligations, risk appetite, and how quickly your environment changes. Fast-moving SaaS companies often need more frequent testing than static environments.
Are These Penetration Testing Tool Prices Current for 2025?
Burp Suite Professional ($475), Nessus ($4,390-$6,390), and other prices cited are from vendor pages updated in 2024-2025. Cobalt Strike pricing varies by partner and region. Always confirm current pricing when purchasing, as vendors adjust prices periodically (Nessus raised prices in March 2024, for example).
We've verified pricing through official vendor pages and trusted resellers, but your actual costs may vary based on volume discounts, multi-year agreements, and bundling options.
How to Prioritize Vulnerabilities After a Penetration Test
Focus on vulnerabilities that combine high severity with high exploitability and affect your most critical assets. Not all "critical" findings are equally urgent.
A critical SQL injection flaw in your customer-facing payment system takes priority over a medium-severity issue in an internal development tool that's behind three layers of network segmentation. Tools like CyCognito and good pentest reports should provide this context.
When in doubt, ask "if an attacker exploited this tomorrow, what's the worst that could happen?" Then prioritize based on that answer, considering both likelihood and impact.
Should You Run Penetration Tests in Production or Staging?
Both, ideally, but with different approaches. Staging environments let you test aggressively without risking production stability. You can run destructive tests, attempt denial-of-service scenarios, and validate fixes without customer impact.
But production environments often have configurations, integrations, and edge cases that staging doesn't perfectly replicate. Production testing finds the real-world issues that only appear under actual load and with real customer data patterns.
Many teams run full scans and aggressive testing in staging, then carefully validate findings in production with production-safe checks. Always get proper authorization before testing production systems, and inform relevant teams about testing windows.
What to Do After a Penetration Test Finds Critical Vulnerabilities
First, validate that findings are accurate (eliminate false positives). Then prioritize based on risk and business impact. Communicate findings to relevant teams (development, infrastructure, leadership) with clear remediation guidance, not just "you have a problem."
Track fixes through your ticketing system with specific acceptance criteria. After remediation, re-test to verify the vulnerabilities are actually fixed (not just masked). Finally, update your processes and controls to prevent similar issues in the future. Root cause analysis matters.
Document everything for compliance: the finding, risk assessment, remediation plan, verification of fix, and process improvements. This creates a trail auditors love to see.
How Penetration Testing Tools Integrate with Compliance Frameworks
Many tools provide reporting templates mapped to compliance requirements. Nessus has PCI DSS and CIS benchmark policies built in. Intruder sends scan results directly to Drata and Vanta for SOC 2 evidence. Astra provides audit-recognized penetration test reports that map to multiple frameworks.
The key is choosing tools that not only find issues but also produce documentation your auditors will accept. Generic reports require manual mapping; compliance-aware tools save that work.
If you're using Comp AI for compliance automation, you can feed pentest findings directly into your control evidence to show continuous security testing without manual documentation overhead.
The Future of Penetration Testing: AI and Automation in 2025
AI is already changing how we test security, and the pace is accelerating. Current trends to watch:
AI-assisted prioritization: Tools like Aikido use AI to rank findings by actual risk based on your specific environment, cutting through noise to surface the issues that actually matter.
Automated exploitation: More tools are moving beyond detection to proving exploitability. This reduces false positives and demonstrates real risk to stakeholders who don't understand technical jargon.
Continuous testing: The shift from annual pentests to continuous validation. Modern development velocity demands testing that keeps pace with releases.
Template-driven speed: Nuclei-style approaches that let you write security checks once and run them everywhere, forever. Community knowledge compounds.
But don't fall for "fully AI pentest" hype. The best security testing combines automated breadth with human expertise for depth. AI accelerates discovery and reduces false positives, but complex vulnerabilities (especially business logic flaws and novel attack chains) still require creative human thinking.
AI will make penetration testers more effective, not obsolete. The winners will be security teams that embrace AI for the grunt work while applying human expertise to the hard problems.
Getting Started with Penetration Testing: Next Steps
Based on what you've read, here's how to move forward:
Assess your current gaps: What parts of your attack surface aren't being tested regularly? External perimeter? Web applications? Internal network? Cloud infrastructure? Start by understanding your blind spots.
Start with fundamentals: If you have nothing, begin with Nmap, ZAP, and Nessus before adding specialized tools. Master the basics before investing in advanced capabilities.
Prioritize by risk: Invest in testing for your highest-risk assets first. The application that generates $10M in revenue deserves more security attention than an internal wiki.
Build repeatable processes: Document scan schedules, tool configurations, and remediation workflows. Make security testing a system, not a heroic effort.
Tie to compliance: If you need SOC 2, ISO 27001, or other certifications, ensure your testing produces audit-ready evidence. Tools like Intruder and Astra make this easier.
Remember that tools are only as good as the people using them. Invest in training and expertise alongside your toolkit. A skilled pentester with basic tools will find more real issues than a novice with expensive commercial platforms.
Choosing the Right Penetration Testing Tools for Your Organization
The best penetration testing tools in 2025 strike a balance between automation and human expertise. Your web apps need both Burp Suite's depth and Nuclei's breadth. Your infrastructure needs Nessus's thorough coverage and Metasploit's proof of impact. Your compliance program needs continuous scanning (Intruder) and expert validation (Astra or professional pentests).

No single tool does everything. Build a complementary stack that matches your environment, expertise, and budget. Run automated tools continuously to catch obvious issues early. Engage skilled pentesters periodically to find what automation misses. And integrate your findings into systematic remediation tracked through your security program.
Security is a continuous practice, not a point-in-time event. The tools in this guide help you practice it well. They give you visibility into vulnerabilities before attackers find them. They help you validate that fixes actually work. And they generate the evidence you need to prove security to customers and auditors.
Start simple, build systematically, and measure improvement over time. Your security posture should get stronger every quarter as you find and fix issues, not just accumulate more tools.
If you're building a security program that needs to prove itself for SOC 2, ISO 27001, or customer trust, Comp AI can help you turn penetration testing findings into compliance evidence without the manual documentation burden. Check out how Comp AI automates security questionnaires and evidence collection so you can focus on actually securing your systems instead of filling out spreadsheets.
Share this article
Help others discover this content
More from Compliance Hub
Explore more insights and stay ahead of regulatory requirements.
Cloud Security Compliance Guide for SaaS Teams (2025)
Complete guide to cloud security compliance for startups: 12 essential controls, framework comparisons, and a 30-day audit readiness roadmap.
NIST Compliance Guide : CSF 2.0, 800-171, 800-53 (2025)
Complete NIST compliance guide: CSF 2.0, 800-171, 800-53 explained. Implementation roadmaps, ready-to-use templates, and Comp AI automation.
CCPA Compliance Requirements: Complete Guide (2025)
Complete CCPA compliance guide for B2B SaaS: consumer rights handling, opt-out infrastructure, vendor contracts, and defensible documentation.