How to Get SOC 2 Certification The Smart Way
Learn how to get SOC 2 certification with our guide. We cover everything from readiness to audit, using automation to simplify the entire compliance process.
- Home
- Compliance HubHub
- How to Get SOC 2 Certification The Smart Way
Getting a SOC 2 certification is a multi-step process. You'll need to define your scope based on the relevant Trust Services Criteria, get your internal controls in order, run through a readiness assessment, and finally, complete an audit with a licensed CPA firm. The whole thing wraps up with either a Type I report (a snapshot in time) or a Type II report (a look at your controls over a period).
Figuring Out Your SOC 2 Starting Point
Getting SOC 2 certified is a massive step toward building customer trust and landing those bigger enterprise deals. But let's be clear: SOC 2 isn't some rigid, one-size-fits-all checklist. It's a flexible framework from the American Institute of Certified Public Accountants (AICPA) designed to show you're serious about data security and operational rigor. It’s how you prove your systems are built to keep sensitive customer data safe.
For most companies, the hardest part is just figuring out where to start.
The timeline to get certified can really vary. We've seen it take anywhere from 3 to 12 months, depending on how complex your organization is and which report you’re going for.
Choosing Between a Type I and Type II Report
One of the first big calls you have to make is which type of SOC 2 report you need. This decision pretty much sets the tone for your entire audit process and timeline.
- SOC 2 Type I Report: Think of this as a snapshot. The auditor looks at the design of your security controls at a single point in time. It’s a faster way to prove you have the right policies and procedures documented and in place.
- SOC 2 Type II Report: This one is more like a feature film. The auditor tests the operating effectiveness of your controls over a set period, usually 6 to 12 months. This gives your customers a much higher level of assurance that you're consistently secure.
A lot of companies start with a Type I to get a baseline and check the box for immediate customer requests. Then, they tackle the Type II in their next audit cycle. Splitting it up can make the whole thing feel a lot less overwhelming.
This image gives you a good idea of what an official SOC report looks like and what the auditor is focused on.
You can see how the System Description and the Controls sections are the real meat of the report.
Key Takeaway: A Type I report validates the design of your controls at one moment, while a Type II report validates their operational effectiveness over several months. Most enterprise customers will eventually ask for a Type II.
SOC 2 Type I vs Type II At a Glance
Feeling a bit stuck on which report is right for you? This quick comparison should help clear things up and guide you toward the best fit for your business needs right now.
| Attribute | SOC 2 Type I | SOC 2 Type II |
|---|---|---|
| Focus | Design of controls at a specific point in time | Operating effectiveness of controls over a period |
| Timeline | Faster; typically 1-3 months | Longer; requires a 3-12 month observation period |
| Effort | Less intensive; focuses on documentation and setup | More intensive; requires evidence collection over time |
| Assurance Level | Good; shows you have the right policies | Highest; proves your controls work consistently |
| Best For | Startups needing quick validation or meeting an urgent customer request | Companies targeting enterprise clients or needing to show long-term security posture |
Before you jump into implementing controls, it's smart to figure out where you stand today. A great first move is to gauge your current security posture. You can get a much clearer picture of your gaps by completing a SOC 2 readiness assessment .
And if you’re looking at the bigger compliance picture, it’s helpful to understand related information security standards like ISO 27001 certification to see how everything fits together.
Defining Your Scope with Trust Services Criteria
Okay, you've figured out whether you need a Type I or Type II report. Next up is one of the most important decisions you'll make in the entire SOC 2 process: defining your audit scope. This isn't just about ticking boxes; it's about strategically choosing the right Trust Services Criteria (TSCs) that actually match what your business does and what you promise your customers.
Every single SOC 2 audit starts with the Security criterion. Think of it as the foundation of your house—it's non-negotiable. This is also called the Common Criteria, and it covers all the baseline ways you protect your systems and data from people who shouldn't have access to them.
From there, you have four other TSCs to consider: Availability, Processing Integrity, Confidentiality, and Privacy. The key here is that you don't need all of them. In fact, picking criteria that don't apply to your business is a classic rookie mistake that wastes a ton of time and money. The real goal is to choose only the ones that reflect the services you sell.
Choosing the Right Criteria for Your Business
The best way to pick the right TSCs is to put yourself in your customer's shoes. What are they really worried about when they hand over their data or rely on your service?
- Availability: Is your platform absolutely critical to your customers' daily operations? If your service going down means their business grinds to a halt—think a cloud hosting provider or a B2B SaaS platform with a tough SLA—then you absolutely need to include Availability. This proves you have the right monitoring, backups, and disaster recovery plans to stay up and running.
- Processing Integrity: Does your system crunch numbers or handle transactions where accuracy is everything? This is a must-have for a fintech company processing payments or an e-commerce platform that has to get sales tax right every single time. Processing Integrity shows your system does exactly what it's supposed to, without errors, funny business, or weird delays.
- Confidentiality: Are you handling sensitive information that isn't personal data but is still protected by an NDA or contract? This could be anything from intellectual property and financial models to secret business plans. A legal tech platform or a firm managing M&A deals would be lost without this one. It's your promise to clients that their secrets are safe with you.
- Privacy: This one is laser-focused on Personally Identifiable Information (PII). If your business collects, uses, or stores things like names, email addresses, phone numbers, or health information, the Privacy TSC is non-negotiable. It’s how you prove you're on top of data protection rules like GDPR and CCPA.
Choosing your TSCs is like building a custom security framework. Security is the foundation, and you add the other pieces—Availability, Confidentiality, etc.—based on the unique structure of your business and the specific promises you make to your customers.
This visual shows how the core Security criterion combines with others like Availability and Confidentiality to create a complete picture of your compliance scope.
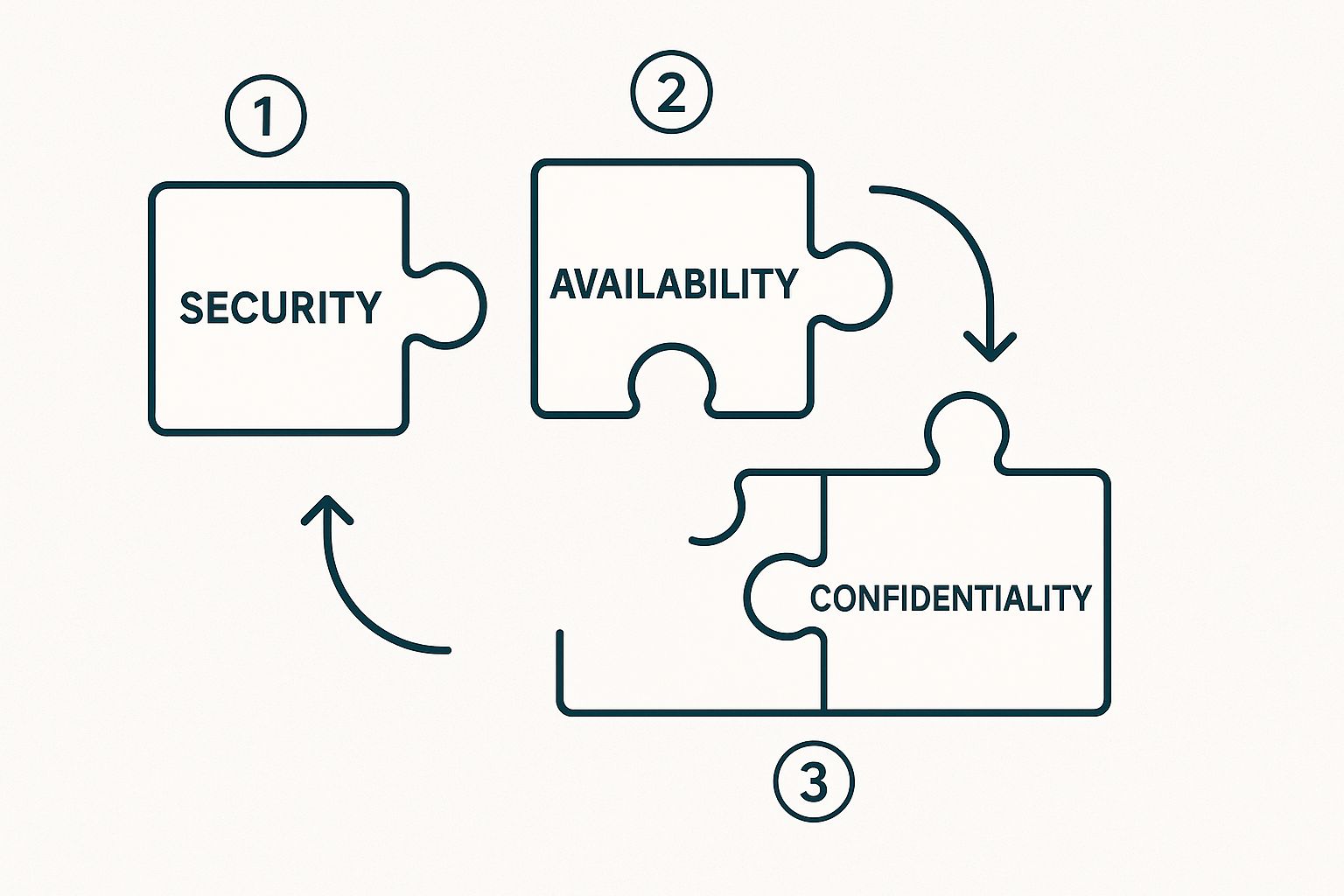
Each piece of the puzzle represents a commitment you're making to your customers, showing them you've built a comprehensive approach to data protection that's perfectly suited to what you do.
How Automation Simplifies Scope Definition
Figuring out your scope can feel like a huge headache, but modern compliance platforms have made this a whole lot easier. Instead of trying to manually translate your business processes into the dense language of AICPA criteria, an automation tool can walk you right through it. For a deeper look at the specific controls tied to each criterion, you can check out our detailed guide on SOC 2 compliance requirements .
Platforms like Comp AI completely change the game by:
- Guiding you through it: They ask smart, targeted questions about your business to help recommend the TSCs that actually make sense for you.
- Mapping what you already have: The platform can connect the security practices you already follow directly to specific SOC 2 requirements, instantly showing you where you're covered and where the gaps are.
- Giving you pre-built templates: You get instant access to policies and control templates designed for the TSCs you've picked, which can save you hundreds of hours of mind-numbing documentation work.
By using automation, you can confidently set a scope that's both relevant and easy to defend to an auditor. This makes sure you aren't over-committing to things you don't need or, even worse, leaving out something critical your customers are counting on.
Building Your Internal Controls Framework
Once you’ve locked in your audit scope, it's time to build the engine of your SOC 2 compliance program: the internal controls framework. This isn't about writing policies that just sit on a shelf collecting dust. It's about creating real, repeatable, evidence-backed processes that become part of your company's DNA.
A strong controls framework is how you prove to auditors—and more importantly, to your customers—that your security promises are more than just words on a website. It’s the collection of specific, documented actions you take to meet the Trust Services Criteria you've chosen.

From High-Level Policies to Actionable Controls
SOC 2 criteria are intentionally broad. They tell you what you need to achieve, but they don't prescribe how to do it. For example, the Security criterion requires you to manage access, but it doesn't say you must use role-based access control (RBAC) or require MFA. Your job is to translate these high-level requirements into concrete controls that fit your specific environment.
This is where a lot of companies get stuck. It’s one thing to write up an "Access Control Policy," but proving it actually works is a whole different ball game. You need documented, repeatable processes that generate evidence. Without a solid policy foundation, your controls will feel random and inconsistent. If you need a hand, check out our guide on crafting an effective information security policy to serve as your blueprint.
Let's walk through a practical example for employee offboarding, a make-or-break control area.
- The Policy: "Employee access to company systems will be revoked in a timely manner upon termination." (A bit vague, right?)
- The Control: A documented offboarding workflow is created in your HR system. When an employee is marked as terminated, tickets are automatically generated and assigned to IT to revoke access to all critical systems within 24 hours.
- The Evidence: The completed IT tickets, with timestamps, serve as undeniable proof that the control is operating exactly as designed.
See the difference? We’ve moved from a vague promise to a testable, auditable system.
Core Controls Every Business Needs
While every SOC 2 audit is unique to the company, certain foundational controls show up in nearly every report. Think of these as the pillars supporting your security posture—and they're often the first things an auditor looks for.
Here are a few essential areas to get right:
- Change Management: How do you manage and document changes to your production environment? A rock-solid control involves linking every single code deployment back to a documented change request, like a Jira ticket that shows approval, testing, and deployment details.
- Access Reviews: You need a process to regularly review who has access to what. A practical control is to conduct quarterly access reviews for critical infrastructure, where system owners must formally sign off on each user's continued need for access. No exceptions.
- Risk Assessment: This is all about identifying, analyzing, and mitigating risks to your organization. A tangible control here is maintaining a risk register that gets reviewed and updated annually by management, complete with clear action plans for the big, scary risks.
Pro Tip: Don't try to build all of this from scratch. It's a massive headache. Compliance automation platforms like Comp AI provide libraries of pre-built, auditor-approved controls mapped directly to the SOC 2 criteria. This can save you hundreds of hours and make sure you’re not missing anything critical.
The Power of Automation in Evidence Collection
Let's be honest, the single most time-consuming part of any SOC 2 audit is gathering evidence. Manually taking screenshots, downloading logs, and chasing down colleagues for proof is a fast track to burnout and human error. This is where automation becomes a total game-changer.
Modern compliance platforms integrate directly with your tech stack—think AWS, GitHub, Jira, and your HR system—to continuously and automatically collect evidence in the background.
| Manual Evidence Collection | Automated Evidence Collection |
|---|---|
| Taking screenshots of cloud configurations weekly. | Continuous monitoring of cloud settings with alerts for misconfigurations. |
| Pinging engineers for pull request approvals. | Automatically linking Git commits and approvals to change management controls. |
| Manually checking if new hires completed security training. | Integrating with your HR system to track and flag incomplete training automatically. |
Using Automation to Speed Up SOC 2 Readiness
The old-school way of getting SOC 2 compliant is a notorious time-suck. We’re talking about a world of giant spreadsheets, endless manual evidence collection, and a calendar overflowing with meetings just to figure out where things stand. This manual slog isn't just slow—it's a breeding ground for human error and a massive drain on your engineers' time.
Thankfully, there’s a much smarter way to work. Compliance automation platforms were built specifically to kill the painful, repetitive tasks that bog down the entire readiness phase. They can turn a months-long marathon into an automated workflow, shrinking your prep time from half a year down to just a few weeks.
From Manual Drudgery to Continuous Monitoring
Instead of relying on quarterly check-ins and frantic fire drills right before the audit, automation helps you build a compliance posture that’s always on. Think of a platform like Comp AI constantly scanning your cloud environment. It's like having a security expert watching your back 24/7, instantly flagging any misconfigurations in AWS or Azure that could create a compliance gap.
This constant monitoring is a fundamental shift. Rather than finding out about problems during a painful readiness assessment, you get alerted in real-time. This lets your team fix issues as they pop up, long before an auditor ever lays eyes on them.
This screenshot gives you a feel for a typical dashboard in an automation tool, where you can see control status and evidence collection all in one place.

You can see at a glance which controls are passing, which have failed, and what evidence has been pulled automatically. It's a live view of your audit readiness.
How Automation Plugs Into Your Tech Stack
The real magic of this approach is how it integrates deeply with the tools your team already uses every single day. An effective compliance automation platform connects directly to your entire tech stack, automating tasks that would otherwise eat up hundreds of hours.
Here’s what that looks like in the wild for a mid-sized SaaS company:
- Evidence from GitHub: A developer merges a pull request, and the platform automatically grabs the approval and links it as evidence for your change management controls. No more bugging engineers for screenshots.
- Tasks in Jira: The platform spots that a new hire hasn't finished their security awareness training. Boom—it automatically creates a Jira ticket and assigns it to their manager.
- Checks in AWS: The system is always monitoring your AWS setup to make sure critical security settings—like MFA on root accounts or encryption on S3 buckets—are locked down correctly.
This kind of integration makes compliance a background process. It becomes a natural part of your existing workflows, not some disruptive, separate thing that everyone dreads.
Key Insight: Automation doesn't just make evidence collection faster; it makes it more reliable. By taking manual steps out of the equation, you kill the risk of forgotten tasks, inconsistent evidence, and last-minute audit surprises.
The Financial and Strategic Upside of Automation
Investing in a compliance platform might feel like another expense, but it pays for itself by slashing direct costs and the opportunity cost of manual work. Getting SOC 2 certified can get pricey. For small businesses, preparation and certification costs can easily hit around $91,000, while larger companies might see bills closer to $186,000. By automating the most labor-intensive parts of readiness, you dramatically reduce the internal hours and consulting fees needed to get ready.
Beyond the money you save, automation builds a compliance foundation that can scale. As your company grows—adding new people, new services, and more cloud infrastructure—your automated compliance program grows with you. Instead of your security processes cracking under the strain of growth, they adapt, keeping you "always audit-ready" so you can chase those enterprise deals with total confidence.
Successfully Navigating the SOC 2 Audit
Alright, you've done the hard work. Your internal controls are in place, and Comp AI is handling the evidence collection automatically. Now comes the final boss: the audit itself. This is where an independent CPA firm comes in to validate everything you've built. It can feel like a final exam, but it doesn't have to be.
If you've followed the process, this is less of an interrogation and more of a victory lap.
Think of it this way: auditors aren't there to trip you up. Their job is to verify that your controls work the way you say they do. When you’ve used a platform like Comp AI to lay the groundwork, you’re not just prepared—you're walking in with a serious head start.
This whole process is becoming table stakes for doing business. The market for SOC reporting is expected to balloon from USD 4.2 billion in 2024 to USD 9.1 billion by 2033. That tells you everything you need to know: proving your security posture isn't a nice-to-have anymore.
Choosing the Right Audit Partner
This is a big one. Picking your CPA firm is one of the most important decisions in the entire SOC 2 journey. Don't just go with the first name you find.
You need a firm that gets modern, cloud-native companies. They need to understand your tech stack and appreciate how much easier automation makes their job. A good auditor will see your use of Comp AI as a massive green flag—it signals that you’re organized and take compliance seriously.
My two cents: Don't just shop on price. A cheap audit might save you a few bucks upfront, but if the firm doesn’t understand your world, you'll pay for it in friction, endless back-and-forth, and a mountain of headaches for your team.
Making the Audit Process Painless
The audit is a partnership. It involves interviews, reviewing evidence, and answering questions. Your goal is to make this as smooth as humanly possible for everyone involved.
A little prep goes a long, long way.
- Prep Your Team: Figure out who will talk to the auditors—maybe your lead engineer or head of HR. Give them a quick rundown of what to expect. The main thing is to be honest and direct.
- Centralize Communication: Pick one person to be the main point of contact for the auditors. This keeps things from getting chaotic and prevents your entire team from being bombarded with requests.
- Lean on Your Platform: This is where the magic happens. An auditor asks for proof that you've done quarterly access reviews for your production database. Instead of a mad scramble through old spreadsheets, you just pull a report from your Comp AI dashboard. Done.
If you want to get ahead of the game, a solid cybersecurity audit checklist can help you anticipate the kinds of things auditors will dig into.
What Auditors Really Look For
Auditors live for two things: consistency and proof. They need to see that your controls are not just written down somewhere, but are actually being followed day in and day out.
They'll do this by sampling. For instance, they might pick five employees who left the company during the audit period. Then, they’ll ask for evidence that their access to critical systems was shut off within the timeframe your policy dictates.
With an automated platform, this isn't a fire drill. It's a two-minute task. All the evidence is already there, neatly organized with timestamps.
That’s the kind of preparedness that makes auditors happy. It means a faster, more efficient audit, fewer follow-up questions, and getting that final SOC 2 report in your hands much, much sooner.
Your Top SOC 2 Certification Questions, Answered
Let's be real, the world of SOC 2 can feel like a maze. When you're just starting out, you're bound to have questions about the practical stuff—how much is this going to cost, how long will it take, and what the heck happens after the audit is done?
Getting a handle on these details from the get-go will save you a ton of headaches down the road. Let's clear up some of the most common things that trip teams up.
How Much Does a SOC 2 Report Actually Cost?
There's no simple price tag for SOC 2. The cost swings wildly based on a few key things: your company's size, how complex your systems are, and, frankly, how good (or bad) your security is right now. A smaller startup that's already got its security ducks in a row might spend anywhere from $20,000 to $60,000 for a SOC 2 Type I report.
For bigger companies or anyone jumping straight to a Type II, the costs can easily sail past $100,000. That total bill usually breaks down into three chunks:
- Readiness Assessment: A preliminary check to see where your security gaps are.
- Automation Software: Platforms like Comp AI that do the heavy lifting for you.
- The Audit Itself: The fee you pay the independent CPA firm to do the actual audit.
Using an automation platform is a game-changer here. It drastically cuts down the internal hours and pricey consultant fees, making the whole thing a much smarter investment.
How Long Does It Take to Get SOC 2 Certified?
Just like cost, the timeline depends on your starting line and which report you’re after. The biggest factor by far is your current security posture.
A SOC 2 Type I report is basically a snapshot of your controls at a single point in time. If you're organized, you can often knock this out in 3 to 6 months. It's the go-to for companies that need a report, like, yesterday to unblock a deal.
A SOC 2 Type II report is more of a marathon than a sprint. It needs an "observation period" to prove your controls are actually working consistently over time. From start to finish, you're usually looking at 6 to 12 months. If your security is already rock-solid, you can definitely speed things up, but that observation window is non-negotiable.
Expert Insight: Here's a pro tip: start with a Type I to get a report in hand quickly. Then, immediately kick off the observation period for your Type II. This two-step approach satisfies those urgent customer demands while you work toward the more robust report.
We Got the SOC 2 Report. Now What?
Popping the champagne after getting your SOC 2 report is a huge win, but it’s not the end of the story. SOC 2 isn't a one-and-done deal; it’s a year-round commitment to keeping your security tight.
Your SOC 2 report is typically considered valid for 12 months. After that, you'll need to go through another audit to renew it and show customers you're still on top of your game.
This means your compliance program needs to be a living, breathing thing. You have to keep maintaining controls, gathering evidence, and watching your environment all year long. This is where automation platforms really earn their keep—they turn compliance from an annual panic attack into a smooth, continuous process. When you stay on top of it, your next audit is just a simple check-in, not another massive project.
--- Ready to stop worrying about compliance and start winning deals? Comp AI transforms SOC 2 from a months-long headache into an automated, audit-ready process. Our AI-first platform centralizes controls, automates evidence collection, and provides expert guidance to get you certified in a fraction of the time. See how you can achieve SOC 2 readiness and get back to building your business. Get started with Comp AI today .
Share this article
Help others discover this content
More from Compliance Hub
Explore more insights and stay ahead of regulatory requirements.
12 Top Risk Management Software Platforms for 2025
Discover the 12 top risk management software platforms for 2025. In-depth reviews comparing features, pros, cons, and pricing to help you choose.
What Is Third Party Risk Management?
Learn what is third party risk management and why it's critical. Our guide breaks down the process, frameworks, and strategies for protecting your business.
Your Guide to a Compliance Automation Platform
Learn how a compliance automation platform transforms GRC strategy by streamlining tasks, reducing risk, and ensuring regulatory adherence.