A failed SOC 2 audit can feel like a crushing setback. You've invested months of preparation, countless engineering hours, and significant budget only to receive a qualified or adverse opinion from your auditor.
Customer deals are stalled, stakeholders are asking tough questions, and the timeline to compliance just got reset.
Here's the reality: a failed SOC 2 audit doesn't mean game over. It's actually a detailed roadmap showing exactly what needs fixing.
With the right recovery strategy, many companies turn a qualified report into a clean one faster than their original audit attempt took.
This guide walks through everything you need to know about SOC 2 audit failures, from understanding what went wrong to implementing a systematic recovery plan that gets you audit-ready in weeks (not months).

What Happens When You Fail a SOC 2 Audit (Qualified vs Adverse Opinion)
First, let's clarify something important: SOC 2 audits don't technically have pass/fail grades. Instead, auditors issue opinions on whether your controls meet the Trust Services Criteria established by the American Institute of CPAs (AICPA).
In an ideal outcome, you receive an unqualified opinion, meaning your controls operate effectively and meet all requirements. This is what everyone wants, essentially a clean bill of health.
However, when significant issues are found, auditors issue a modified opinion, which takes three forms:
→ Qualified opinion: One or more exceptions exist where you didn't meet SOC 2 requirements. Some controls failed or couldn't be verified.
→ Adverse opinion: Widespread or major failures across multiple control areas. Most of your security controls didn't operate effectively.
→ Disclaimer of opinion: The auditor couldn't gather enough evidence to reach any conclusion. This typically happens when you're severely unprepared.
From a practical standpoint, any modified opinion is treated as a failure by customers. A report showing control deficiencies or exceptions will block enterprise deals just as effectively as having no report at all.
Top 5 Reasons Why SOC 2 Audits Fail (And How to Fix Them)
Understanding failure patterns helps prevent them. Here's what typically goes wrong:
▸ Incomplete evidence or documentation gaps
You couldn't prove a control operated over the entire audit period. Maybe access review logs are missing for two months, or you can't show consistent backup testing.
Auditors mark these controls as ineffective because they can't verify your claims. This is one of the most common failure points, especially for teams managing evidence manually.
▸ Control design flaws
Your controls existed on paper but weren't designed to actually mitigate the risks.
For example, you have a user offboarding process that's supposed to remove access within 24 hours, but it doesn't actually enforce that timeline. The control design itself is inadequate.
▸ Operating failures during the audit period
For Type II audits (which observe controls over 3-12 months), controls must operate consistently.
If multi-factor authentication was implemented halfway through the period, or an incident revealed that your incident response process wasn't followed, that's a serious exception.
Auditors aren't looking at a single point in time but sustained operation. The CISA Cybersecurity Best Practices guidance reinforces that consistent implementation and monitoring of security controls over time is essential for maintaining a strong security posture.
▸ System description mismatches
Your system description (the document explaining your infrastructure and controls) doesn't accurately reflect reality.
Perhaps you omitted a critical system, or described controls that don't actually exist. When what you documented doesn't match what the auditor observes, that's a qualification waiting to happen.
▸ Scope problems
You may have accidentally excluded services or data that should've been in scope, or included trust criteria (like Confidentiality or Availability) without adequate controls to support them.
In every case, the result is the same: you don't have a passing SOC 2 report to show customers. Instead, you have a document detailing exactly what didn't work.
The good news? It's also your blueprint for fixing everything.

Business Impact of Failed SOC 2 Audit: Revenue Loss and Recovery Timeline
A failed SOC 2 audit isn't just an internal setback; it creates tangible business problems that need immediate attention.
▸ Revenue impact and deal blockers
This is usually the most painful consequence. Enterprise customers who were waiting for your SOC 2 report will pause contracts or walk away. Some prospects will eliminate you from their vendor shortlist entirely.
If you're a startup trying to move upmarket, a failed audit can cost you months of pipeline progress and hundreds of thousands in potential ARR.
One startup reportedly unlocked $500k in contracts after finally getting SOC 2 compliant, showing just how much revenue can be tied to this certification.
▸ Erosion of customer trust
Current customers may question whether their data is truly secure. Even if you explain you're remediating the issues, doubt has been planted.
Some customers might request additional security questionnaires or impose extra oversight until you achieve a clean report.
▸ Financial costs spiral quickly
You'll need to pay for remediation work (which could mean buying new security tools, hiring consultants, or implementing new infrastructure). Then you'll pay for another audit.
The combined cost of failed audit fees + remediation + re-audit can easily exceed $50,000 for startups.
According to IBM's Cost of a Data Breach Report, the average cost of non-compliance and security failures continues to rise year over year, making prevention far more cost-effective than remediation.
Compare that to getting it right the first time with modern platforms:
| Metric | Price with Comp AI | Price with others |
|---|---|---|
| Platform + Audit Cost | $5,000-10,000 | $15,000+ |
| Time Investment | <5 hours total | 100+ hours |
| Success Rate | 100% guarantee | No guarantee |
The cost of failure makes the initial investment in the right platform look cheap by comparison.
▸ Operational disruption
Your engineering and IT teams will be pulled away from product work to fix security gaps. Policies need rewriting, infrastructure needs reconfiguring, evidence collection starts over.
This can disrupt normal operations for weeks or even months. Management attention shifts from growth initiatives to compliance firefighting.
▸ Reputational damage in tight-knit industries
Word spreads, especially in tech communities. Partners, investors, and prospects talk. Being known as the company that failed their audit can hurt your brand credibility in ways that take time to rebuild.
▸ Future audits become harder
Until you fix the issues, you're in a state of non-compliance. If you rush into a re-audit without adequate changes, you risk failing again.
Auditors will scrutinize you more carefully next time, and stakeholders will have less patience.
⚠️ CRITICAL BUSINESS IMPACT: Every day without a clean SOC 2 report is a day of lost revenue opportunities, eroded trust, and mounting costs. That's why speed in recovery matters enormously.
How to Recover from Failed SOC 2 Audit: 8-Step Remediation Plan
Recovering from a failed SOC 2 audit requires a methodical, urgent approach. Here's how to systematically fix the problems and get back on track.
Step 1: Analyze Your Failed SOC 2 Audit Report (What Went Wrong)
Start by understanding exactly what went wrong. Obtain your full audit report and create a detailed list of every exception, deficiency, and observation the auditor noted.
Pay attention to which Trust Services Criteria were affected (Security, Availability, Confidentiality, etc.) and whether issues were isolated incidents or systemic problems.
Were there patterns? Did most failures center around access controls, or was it scattered across multiple domains?
Schedule a debrief call with your auditor. This is critical.
Ask clarifying questions:
- How severe is each issue?
- Which ones led to the qualified opinion?
- Are there quick wins vs. complex fixes?
Understanding severity helps you prioritize remediation efforts.
Involve your department heads in this analysis. If policies weren't followed, ask why. If technical controls failed, determine the root cause.
Was it a configuration error, lack of automation, or simply no one being assigned to monitor the control?
This detailed review prevents misdirected fixes. You need to target the actual problems, not symptoms.
Step 2: How to Communicate Failed SOC 2 Audit to Customers and Stakeholders
Transparency builds trust, even in failure.
Notify internal leadership immediately with a clear plan. They need to understand the business impact and what you're doing about it.
For customers and prospects, consider who needs to be informed. If a major client was expecting your SOC 2 report by a certain date, be honest:
"Our audit identified several security control gaps that we're actively remediating. We're implementing fixes now and will undergo a fresh audit. We expect a compliant report by \[specific date\]."
Customers appreciate accountability. Share what you're fixing and your timeline, but don't overshare sensitive details about specific vulnerabilities.
Emphasize that you're taking the issues seriously and implementing improvements that will make your security posture stronger.
If you already have a modified report in hand that customers might see, be prepared to explain each major finding and your remediation plan. This proactive communication can actually demonstrate operational maturity rather than incompetence.
Step 3: Root Cause Analysis for SOC 2 Audit Failures
For each audit finding, dig into why it occurred. Don't stop at surface-level explanations.
If user access reviews weren't conducted, was it because no one was assigned? Was there no reminder system? Did the team lack a process?
If a backup failed during testing, was it due to misconfiguration, lack of documentation, or insufficient infrastructure?
Use the "Five Whys" technique: keep asking why until you uncover the underlying cause.
Often, the root cause is systemic:
- No one owned compliance
- The team lacked proper tools
- Security wasn't prioritized early enough
This root cause analysis methodology, widely used in quality management, helps organizations identify and address fundamental issues rather than just symptoms.
Understanding root causes ensures your fixes actually prevent recurrence. If you just add a policy without fixing the underlying process gap, the same issue will surface in your next audit.

Step 4: SOC 2 Remediation Plan Template: Actions, Owners, and Deadlines
Create a comprehensive remediation plan that addresses every finding. Treat this like a project plan with specific actions, owners, and deadlines.
Prioritize by severity and business impact. Fix critical security exposures immediately (like unencrypted databases or excessive admin access). Schedule less critical improvements on a reasonable timeline.
Your plan should include:
- Policy updates or net-new policy creation
- Security tool implementations (MFA enforcement, logging solutions, endpoint management)
- Process changes (quarterly access reviews, change management procedures, security training)
- Infrastructure reconfigurations
- Staff training on new procedures
Assign clear ownership for each action item.
For example: "Finding: Developers had admin access to production → Action: Implement role-based access controls, remove broad admin rights → Owner: CTO → Deadline: 30 days"
Be specific about deliverables. Auditors will want evidence of each fix. Map every remediation back to the audit's Trust Criteria to ensure complete coverage.
This plan will likely involve multiple teams coordinating. Management should review and approve it, ensuring you have the resources (budget, tools, time) to execute.
Step 5: How to Execute SOC 2 Remediation and Collect Evidence
Now comes the hard work: implementing the fixes according to your plan.
As you address each issue, collect evidence of completion. You'll need to prove to auditors (and potentially customers) that remediation happened.
Evidence types:
- Screenshots
- Configuration exports
- Policy approval records
- Training completion certificates
Document everything.
Go beyond the specific items the auditor flagged. If you discovered related weaknesses during root cause analysis, fix those too.
For example, if one vendor risk assessment was missing, implement a complete vendor review process so nothing slips through next time.
Implement continuous monitoring wherever possible. After fixing an issue, set up alerts or checks to ensure it stays fixed.
This could be as simple as a monthly script verifying certain settings remain enabled, or using automated compliance software that monitors continuously.
During execution, communicate progress to leadership and any critical customers who are waiting. Quick wins help rebuild confidence.

Step 6: SOC 2 Readiness Assessment Before Re-Audit
Once all gaps are addressed, perform a fresh internal audit or gap assessment before calling your external auditor back. This is your safety net.
Go through each control area and test it as if you were the auditor. Would you find any remaining issues?
For Type II re-audits, ensure you have evidence of controls operating over the required period after your fixes.
Consider bringing in a third-party consultant for an objective readiness review. Better to catch lingering problems now than during the official re-audit.
Verify your documentation is current:
- Policies
- Network diagrams
- Risk assessments
- Especially your system description
All should reflect your current state accurately. Scope problems contributed to many audit failures, so pay extra attention here.
Use a comprehensive SOC 2 compliance checklist to ensure nothing is overlooked.
By the end of this readiness review, you should be confident an auditor would find no major exceptions.
Step 7: SOC 2 Re-Audit Process: Type I vs Type II for Recovery
With fixes verified, coordinate with your audit firm for re-engagement.
Decide on the audit type. For Type II failures, you might start with a Type I audit to quickly validate your controls are now designed and in place.
This gives you a report to share with customers while you gather the 3-6 months of evidence needed for Type II.
Many experts recommend this approach: getting a Type I first proves your controls work before committing to a long observation period.
Understanding the difference between SOC 2 Type 1 vs Type 2 can help you make the right decision for your recovery timeline.
Share your remediation documentation with the auditor upfront. Show them exactly what you fixed and how.
This transparency helps focus the audit and demonstrates you took the previous findings seriously.
During the re-audit, be prepared to show not just that specific issues were resolved, but that your overall security program matured.
Auditors will look for evidence you didn't just patch individual holes but strengthened your entire approach.
Step 8: Maintaining SOC 2 Compliance After Passing Re-Audit
Once you pass the re-audit and achieve a clean SOC 2 report, don't let the momentum stop.
Incorporate lessons learned into your ongoing security and compliance program. If lack of monitoring caused issues, implement continuous compliance monitoring tools that flag problems before the next audit.
If policies weren't followed, set up internal quarterly compliance check-ins.
Many organizations assign a compliance owner or program manager responsible for maintaining SOC 2 readiness year-round, not just at audit time.
This person:
- Tracks all compliance requirements
- Maintains the evidence repository
- Coordinates across teams
Treat the failure as a catalyst to mature your security posture. In fact, some companies emerge from a failed audit with stronger programs than competitors who passed on first try but cut corners.
Your goal is to make the next year's audit sail through with minimal findings. Make compliance a business-as-usual activity rather than an annual scramble.
How to Prevent SOC 2 Audit Failure: Best Practices for 2025
Prevention is far cheaper and less painful than recovery. Here's how to ensure you never fail another SOC 2 audit.
▸ Invest in pre-audit readiness assessments
Always perform a gap analysis or readiness assessment before your official audit begins. Catch weaknesses when you still have time to fix them quietly.
This could be an internal self-check or a third-party consultant review. A SOC2 readiness assessment helps you identify gaps before the auditor does.
▸ Implement continuous compliance monitoring
Rather than checking controls once before the audit, monitor them continuously throughout the year.
Modern platforms can automatically collect evidence and alert you to any control drift in real-time.
The NIST Cybersecurity Framework emphasizes continuous monitoring as a core component of effective security programs, enabling organizations to detect and respond to issues before they become audit findings.
| Approach | Platform Cost | Team Time Required | Automation Level |
|---|---|---|---|
| Comp AI | $5,000-10,000 | <5 hours total | 90%+ automated |
| Traditional GRC | $15,000+ | 100+ hours | 30-40% automated |
| Manual/DIY | $0-3,000 | 300+ hours | 0-10% automated |
Comp AI's automation means your team spends less than 5 hours total managing compliance.
For example, if encryption gets disabled on a database or a new employee bypasses security training, you'll know immediately and can fix it before it becomes an audit finding.
Traditional manual approaches might only catch these issues during the audit itself, when it's too late.
▸ Automate evidence collection aggressively
Missing or incomplete evidence is a top audit failure cause. Automation eliminates this risk by continuously pulling evidence from your systems.
Platforms like Comp AI have AI agents that actively hunt for evidence across your infrastructure, take screenshots, and document controls automatically.
You're no longer dependent on remembering to collect proof each quarter.
▸ Assign clear ownership and accountability
Designate a compliance officer or program manager responsible for SOC 2 readiness year-round.
This person maintains a compliance calendar (when to do access reviews, policy refreshes, disaster recovery tests) so nothing is missed.
Without clear ownership, compliance tasks fall through the cracks. "Everyone's responsible" often means "no one's actually managing it."
▸ Keep documentation aligned with reality
A common audit failure is when your documented policies don't match what you actually do.
Make it a practice to update documentation when you change processes. Pay special attention to your system description in your SOC 2 report, keeping a living version that updates as your infrastructure evolves.
▸ Consider a Type I audit as a trial run
If you're new to SOC 2 or just made major changes after a failure, doing a Type I audit first can validate your controls work before committing to the longer Type II observation period.
It's a safety net that catches issues early.
▸ Use automation platforms with guarantees
Some modern compliance platforms are so confident in their automation that they offer success guarantees.
Comp AI provides a 100% money-back guarantee covering your re-audit costs if you fail after using their platform.
That's how effective automated, AI-driven compliance can be at eliminating the failure risk.
▸ Learn from others
Study why companies in your industry have failed audits. Common pitfalls include:
- Neglecting physical security (if you have an office)
- Not realizing a critical SaaS tool needed SSO
- Assuming a vendor's certification covered you
There are communities and case studies that highlight these mistakes so you don't repeat them.
By treating compliance as an ongoing priority rather than a once-a-year project, and by using modern automation to eliminate manual errors, you dramatically reduce your audit failure risk.

Fastest Failed SOC 2 Audit Recovery: Automated Platforms vs Manual
If you're recovering from a failed audit, speed matters. The faster you remediate and pass a re-audit, the less revenue you lose and the sooner you rebuild customer trust.
Traditional compliance approaches (DIY with spreadsheets, or even older platforms) can take 3-6 months just to prepare for a re-audit.
Modern AI-driven platforms have changed that timeline dramatically.
Comp AI: 24-Hour SOC 2 Audit Readiness After Failure
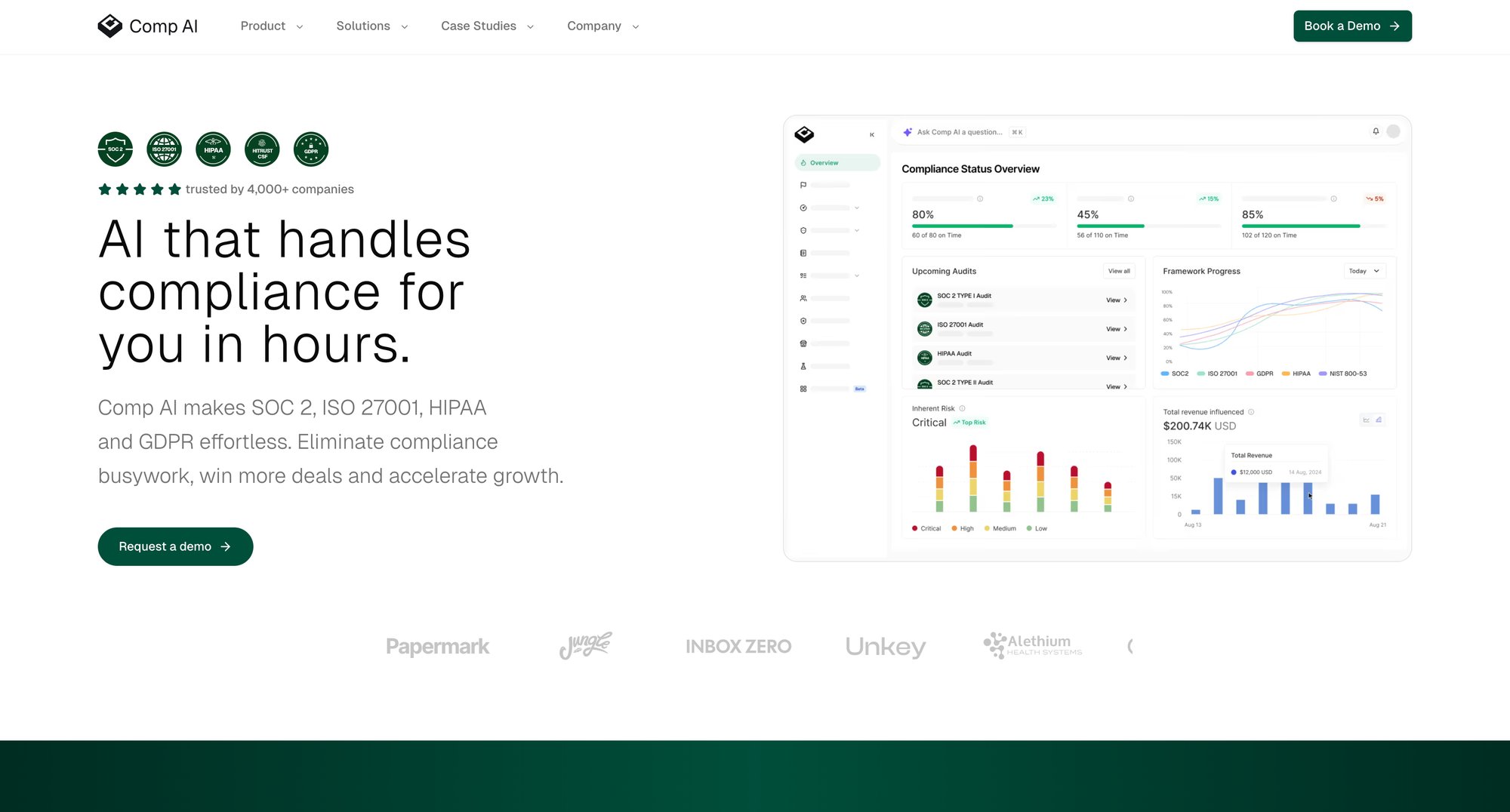
Comp AI was designed specifically to help companies get compliant faster than any other solution. When you're recovering from a failed audit, every week counts.
Speed that matters
With Comp AI, companies typically go from "compliance is blocking deals" to "observation period started" in under a week.
For SOC 2 Type I, you can be audit-ready in as little as *24 hours*.
For Type II, all controls can be implemented and tested in about 14 days, then the standard 3-month observation clock runs in the background while you close deals.
Learn more about realistic SOC 2 compliance timelines.
Compare this to traditional remediation timelines:
| Timeline Stage | Comp AI | Traditional Approach | Time Saved |
|---|---|---|---|
| Gap Analysis | 2 hours (AI-powered) | 2-3 weeks (manual) | 95% faster |
| Remediation Setup | 1 day (done-for-you) | 3-6 weeks (DIY) | 90% faster |
| Evidence Collection | Continuous (automated) | Ongoing manual work | 100+ hours saved |
| Audit-Ready Status | 24 hours (Type I) | 3-6 months | 12x faster |
You save months of time on top of the cost savings.
100% automation means fewer failure points
Comp AI's AI agents automate 90%+ of compliance tasks. They actively hunt for evidence across your systems, take screenshots, document controls, and even answer security questionnaires automatically.
This level of automation eliminates the manual evidence gaps that cause many audit failures.
One startup that switched from another platform reported: "With Vanta we were only 30-40% through SOC2 after 4 months; we switched to Comp AI and they had us audit-ready in a couple of days."
That kind of acceleration is exactly what you need in a recovery scenario.
Done-for-you setup and white-glove support
When you're remediating from a failure, you don't have bandwidth for another learning curve.
Comp AI's team handles the heavy lifting:
- Configure integrations
- Customize policies
- Guide you through every step
You get 1:1 Slack support with 5-minute response times and compliance experts who've seen hundreds of similar situations.
Comp AI offers a 100% money-back guarantee. If you fail your audit after using Comp AI, they refund your money. For companies recovering from a previous failure, this eliminates the risk of another expensive setback.
Continuous monitoring prevents future failures
After you pass your re-audit, Comp AI continues monitoring your infrastructure 24/7.
If anything drifts out of compliance (like a developer accidentally disabling a control), you're alerted immediately.
This ensures you stay audit-ready year-round and never face another qualification.
Why Comp AI Works for Failed Audit Recovery: Features and Advantages
When you're bouncing back from a failed audit, you need a partner who understands urgency and can deliver results fast. Here's what makes Comp AI uniquely suited for audit recovery:
→ Pre-vetted auditor network
Comp AI connects you with auditors who already know the platform and can fast-track your certification. No ramp-up time, no confusion about where to find evidence.
→ Real-time trust center
While you're working toward your audit, you can share your progress with customers via Comp AI's free public trust center.
It shows them the frameworks you're pursuing and your current security posture, helping maintain confidence during the remediation period.
→ Multi-framework efficiency
If you need to pursue multiple certifications (SOC 2, ISO 27001, HIPAA, GDPR), Comp AI handles them simultaneously without duplicating work.
Many controls overlap, and the platform maps them intelligently.
| Framework | Comp AI Cost | Traditional Cost | Typical Timeline |
|---|---|---|---|
| SOC 2 | $5,000-10,000 | $15,000+ | 24 hours ready |
| ISO 27001 | $5,000-10,000 | $15,000+ | 1 week ready |
| HIPAA | $5,000-10,000 | $15,000+ | 1 week ready |
| Multi-framework | $8,000-15,000 | $40,000+ | Parallel processing |
For context, see our guide on alongside SOC 2.
→ Built by founders who've been there
The Comp AI team built this platform because they experienced compliance pain themselves. They understand the pressure of blocked deals, the confusion of first-time compliance, and the urgency of recovery situations.
The bottom line: if you've just received a qualified SOC 2 opinion and need to recover fast, modern automation platforms like Comp AI can compress your recovery timeline from months to weeks.
For the cost difference and time savings, it's worth seriously evaluating whether your current approach is setting you up for success or another failure.
Failed SOC 2 Audit FAQs: Recovery, Timeline, and Success Rates
Can You Actually Fail a SOC 2 Audit?
Technically, SOC 2 audits don't have pass/fail grades. Auditors issue opinions: unqualified (good), qualified (some issues), adverse (major problems), or disclaimer (insufficient evidence). However, from a business perspective, any modified opinion is treated as a failure because customers won't accept it.
How Long Does It Take to Recover from a Failed SOC 2 Audit?
Recovery timelines vary by the severity and number of findings. With traditional approaches, expect 3-6 months to remediate, collect new evidence, and complete a re-audit. Modern AI-driven platforms can dramatically accelerate this: Comp AI customers typically remediate and become audit-ready in 1-2 weeks, then undergo the necessary audit observation period.
Will a Failed Audit Permanently Damage Our Reputation?
Not if you handle it right. Many successful companies have failed their first SOC 2 audit and recovered. The key is transparent communication with stakeholders, rapid remediation, and ultimately achieving a clean report. Customers care more about your current security posture than past missteps, especially if you demonstrate you fixed everything systematically.
Do We Need to Use the Same Auditor for Our Re-Audit?
Not necessarily. Some companies switch auditors after a failure, though your original auditor already understands your environment. If you switch, the new auditor might need more time to get up to speed. Consider whether the relationship with your current auditor is still productive before making a change.
Can We Fix Issues During the Audit to Avoid Failure?
Once an audit has formally started, you generally cannot fix issues during the observation period and count them as resolved for that audit. However, auditors might note in their report that you began remediation, which can help with customer communications. Your fixes will be evaluated in the next audit cycle.
How Much Does a Failed SOC 2 Audit Cost in Total?
The direct costs include the original audit fee ($3,000-15,000), remediation costs (varies widely, often $20,000-50,000+ for tools, consulting, and labor), and re-audit fees ($3,000-15,000). Indirect costs from lost deals and delayed revenue can easily exceed $100,000 for growth-stage startups. This makes investing in the right compliance platform upfront critical.
What's the Success Rate of Second SOC 2 Audit Attempts?
Companies that perform thorough remediation and readiness assessments before re-auditing have high success rates (80%+ pass on second attempt). The key is not rushing back to audit before fixes are complete and verified. Platforms with automation and guarantees (like Comp AI) report virtually 100% success rates because they eliminate the manual errors that cause most failures.
Should We Pursue Type I or Type II for Our Re-Audit After Failure?
If you failed a Type II audit, consider starting with Type I on your re-audit. This quickly validates your controls are now properly designed and in place, giving you a report to share with customers in weeks. Then you can pursue Type II with the 3-6 month observation period, confident your controls will pass sustained testing.
Can Automation Platforms Really Prevent SOC 2 Audit Failures?
Yes. The majority of audit failures stem from incomplete evidence, manual errors, or controls not operating consistently. Automation platforms eliminate these issues by continuously monitoring controls, automatically collecting evidence, and alerting you to any drift. Modern platforms like Comp AI have such high confidence in their automation that they offer money-back guarantees if you fail.
What to Do After Failed SOC 2 Audit: Immediate Action Plan
A failed SOC 2 audit is undoubtedly a setback, but it's also an opportunity to build a dramatically stronger security and compliance program.
Companies that systematically address their findings often emerge with more robust controls and processes than competitors who barely scraped by on their first attempt.
The key to successful recovery is speed and thoroughness. Every day without a clean SOC 2 report is a day of blocked revenue and eroded trust.
By following the systematic remediation plan in this guide and using modern automation platforms, you can turn a qualified opinion into an unqualified one faster than your original audit attempt took.
If you're currently dealing with a failed audit, here's what to do right now:
Immediate actions (this week):
- Schedule a debrief with your auditor to understand every finding in detail
- Create a prioritized list of all remediation items
- Communicate honestly with key stakeholders about your recovery timeline
- Evaluate whether your current compliance approach set you up for failure
Short-term actions (next 30 days):
- Execute your remediation plan with clear ownership and deadlines
- Implement continuous monitoring to prevent future control drift
- Conduct a thorough readiness self-assessment before scheduling re-audit
- Consider switching to an automation platform if manual processes caused your failure
Long-term approach (ongoing):
- Build compliance into your regular operations rather than treating it as a project
- Assign dedicated ownership for maintaining audit readiness year-round
- Use automation to eliminate the human errors that cause most failures
- Treat your recovery as a foundation for continuous security improvement
If you're looking for the fastest, most reliable path to recovery, consider platforms built specifically for rapid compliance like Comp AI.
With audit-ready timelines measured in days (not months), 100% automation of evidence collection, and a money-back guarantee if you fail, it's designed to prevent the exact problems that caused your audit failure.
The difference between companies that recover quickly and those that struggle for months often comes down to having the right tools and approach. Don't let a second failure compound the damage from the first.
You've learned what went wrong. Now apply those lessons systematically, use automation to eliminate manual failure points, and rebuild stakeholder confidence by achieving a clean SOC 2 report faster than anyone expects.
Your recovery starts today.
Share this article
Help others discover this content