Getting ISO 27001 certified can feel like climbing a mountain, especially when you're trying to close deals and grow your business at the same time. With the right approach and modern automation tools, what used to take 6-12 months can now be accomplished in weeks, even days.
Comp AI has helped hundreds of companies achieve ISO 27001 certification in record time. Some reached audit readiness in just 14 days using Comp AI's AI-powered compliance platform. This guide walks you through exactly how to get ISO 27001 certified, whether you're doing it for the first time or renewing your certification.
What Is ISO 27001 Certification?
ISO 27001 is an international standard for information security management systems (ISMS). Think of it as a comprehensive framework that helps organizations protect sensitive data through systematic risk management and security controls.
Unlike regional standards like SOC 2 (which is primarily US-focused), ISO 27001 is recognized globally. This makes it especially valuable if you're doing business internationally or targeting enterprise customers in Europe, Asia, or anywhere else.
The certification demonstrates that your organization:
- Has identified and assessed information security risks
- Implemented appropriate controls to manage those risks
- Continuously monitors and improves its security posture
- Follows a documented, auditable process for protecting data
For growing tech companies, ISO 27001 often becomes a "must-have" when enterprise prospects ask: "What security certifications do you hold?" It signals that you take security seriously and have systems in place to protect their data.
Why Companies Need ISO 27001 Certification
Companies pursue ISO 27001 for very practical business reasons (nobody wakes up excited about compliance documentation):
Unlocking enterprise deals: Many large organizations require vendors to hold ISO 27001 before they'll even consider a contract. Without it, you're simply not in the running for six or seven-figure deals.
Global market access: If you're expanding internationally (particularly in Europe), ISO 27001 is often expected or even required for certain industries. It opens doors that would otherwise remain closed.
Customer trust and differentiation: In crowded markets, ISO 27001 certification helps you stand out. It's a trust signal that reassures security-conscious buyers that you've invested in protecting their data.
Regulatory alignment: For companies in regulated industries (healthcare, finance, etc.), ISO 27001 can help satisfy multiple compliance requirements simultaneously. The controls often overlap with other frameworks like GDPR, making compliance more efficient.
Actual security improvements: Beyond the business benefits, going through ISO 27001 forces you to think systematically about security risks. Many companies discover and fix vulnerabilities they didn't know existed.
Comp AI has seen companies close deals worth hundreds of thousands of dollars within weeks of achieving certification. The ROI is often immediate and substantial.
How the ISO 27001 Certification Process Works
The ISO 27001 certification process follows a structured path with several distinct phases. Understanding this journey helps you plan effectively and avoid surprises.
How to Define Your ISO 27001 Scope
First, you define what parts of your organization the ISMS will cover. Will it include all operations, or specific business units? Which information assets need protection? Which locations are in scope?
This scoping decision matters because it determines how much work you'll need to do. A narrowly scoped ISMS (perhaps just your SaaS platform and the team that supports it) requires less documentation than one covering your entire global operation.
For most tech startups and growth-stage companies, scoping makes sense. You might focus on:
- Your core product or platform
- The engineering and operations teams that support it
- The data processing activities related to customer information
- Specific geographic locations or legal entities
Clear scoping helps you get certified faster and keeps the process manageable. You can always expand the scope later as you grow.
How to Conduct an ISO 27001 Risk Assessment
ISO 27001 is fundamentally risk-based. You must identify information security risks, evaluate their likelihood and impact, and determine how to treat them.
This involves:
- Asset identification: Cataloging your information assets (customer data, intellectual property, systems, etc.)
- Threat and vulnerability analysis: Identifying what could go wrong (data breaches, system failures, insider threats, etc.)
- Risk evaluation: Assessing which risks are most significant
- Risk treatment: Deciding how to handle each risk (mitigate, accept, transfer, or avoid)
Traditionally, this meant weeks of workshops, spreadsheets, and documentation. Modern platforms automate much of this by:
- Scanning your infrastructure to identify assets automatically
- Suggesting common threats and vulnerabilities based on your tech stack
- Helping you prioritize risks with built-in scoring
- Generating risk treatment plans with recommended controls
What used to take a consultant months can now happen in days with the right tools.
How to Choose and Implement ISO 27001 Controls
Based on your risk assessment, you select controls from Annex A of ISO 27001 (which lists 93 security controls organized into categories).
You don't have to implement all 93 controls. Only those relevant to your risks. This is where expertise helps, because choosing the wrong controls wastes time, while missing critical ones creates gaps.
Common controls for tech companies include:
- Access control: Who can access what systems and data
- Cryptography: How you protect data in transit and at rest
- Asset management: Tracking and protecting company devices and data
- Operations security: Ensuring systems run securely and reliably
- Network security: Protecting your infrastructure from external threats
- Incident management: How you detect and respond to security events
- Business continuity: Ensuring operations can continue during disruptions
Implementation means making these controls real in your environment. For example, if you select "multi-factor authentication," you need to actually deploy and enforce MFA across relevant systems.
Comp AI integrates with your existing tools (AWS, Google Workspace, GitHub, Okta, etc.) to help you implement controls and automatically collect evidence that they're working.
Required Documentation for ISO 27001 Certification
ISO 27001 requires specific documented policies and procedures. At minimum, you need:
- Information Security Policy: Your high-level commitment to security
- Risk Assessment Methodology: How you identify and evaluate risks
- Statement of Applicability (SoA): Which Annex A controls you're implementing and why
- Risk Treatment Plan: How you're addressing identified risks
- ISMS procedures: Documented processes for key activities (incident response, access reviews, change management, etc.)
Many first-timers get intimidated by this documentation burden. The reality is that you don't need to write everything from scratch. Most controls already exist in some form. You're often just documenting what you already do.
PRO TIP: Don't start with a blank page. Modern platforms use AI to generate policy templates customized to your specific tech stack. Instead of spending weeks writing an "Access Control Policy," the AI drafts it in minutes based on your actual systems (mentioning your SSO provider by name, your encryption methods, etc.). You review and refine, but the heavy lifting is done.
This cuts documentation time from weeks to hours.

What to Expect During Your ISO 27001 Audit
Once your ISMS is operational and documented, you're ready for the certification audit. This is conducted by an accredited certification body (an independent auditor authorized to issue ISO 27001 certificates).
The audit typically happens in two stages:
Stage 1 (Documentation Review): The auditor reviews your ISMS documentation to ensure it meets ISO 27001 requirements. They're checking that you have the required policies, procedures, and evidence. This usually takes 1-2 days and can often be done remotely.
Stage 2 (Implementation Assessment): The auditor verifies that your ISMS is actually operating as documented. They'll interview staff, examine evidence, review systems, and test controls. For a small to medium organization, this typically takes 2-5 days depending on scope.
If the auditor finds no major non-conformities, they recommend certification. You receive your ISO 27001 certificate, valid for three years.
How to Maintain ISO 27001 Certification Long-Term
ISO 27001 certification isn't one-and-done. To maintain your certificate, you'll undergo:
- Annual surveillance audits: Lighter audits each year to ensure you're maintaining compliance
- Recertification audit: A more thorough audit every three years to renew your certificate
The good news? Once you have systems and automation in place, maintaining certification becomes routine. Comp AI helps by continuously monitoring your controls, collecting evidence automatically, and alerting you to any gaps before audits.
How Long Does ISO 27001 Certification Take?
This is the question everyone asks. The answer: it depends, but it's getting dramatically faster.

Timeline comparison:
| Approach | Duration | Key Bottlenecks |
|---|---|---|
| Traditional (DIY/Consultant) | 6-12+ months | Manual documentation, learning curve, evidence gathering, auditor scheduling |
| Modern (with Comp AI) | 14 days to audit-ready + 3-4 weeks for audit | Minimal - automation handles most tasks |
Why traditional approaches take so long:
- Weeks spent learning ISO 27001 requirements
- Months writing policies and procedures from scratch
- Manual asset inventories and risk assessments
- Implementing controls one by one across systems
- Gathering evidence manually (screenshots, reports, emails)
- Coordinating with auditors and waiting for their schedule
How automation changes the timeline:
Comp AI has demonstrated this with multiple clients. The difference comes from:
- AI-generated documentation: Policies and procedures drafted in minutes, not weeks
- Automated evidence collection: AI agents pull evidence from your systems continuously
- Smart risk assessments: Platform guides you through risk analysis with templates and recommendations
- Integrated control implementation: Direct connections to your tech stack to deploy controls quickly
- Pre-vetted auditors: Fast-tracked scheduling with certification bodies familiar with the platform
REAL-WORLD RESULT"We expected ISO 27001 to be a six-month distraction. With Comp AI, we were audit-ready in two weeks and certified within 30 days total. It was shockingly fast."\- CTO, Series B SaaS Company

The timeline also depends on your organization's readiness:
- Companies with existing security practices (MFA already deployed, access controls in place, incident response process) can move fastest
- Startups building from scratch take longer, but automation still cuts the time dramatically
- Complex organizations (multiple locations, legacy systems, lots of third parties) need more time regardless of tools
A realistic modern timeline with automation:
- Weeks 1-2: Onboarding, scoping, risk assessment, initial documentation
- Weeks 2-3: Control implementation and evidence collection
- Week 3: Documentation finalization and internal readiness review
- Week 4: Stage 1 audit (documentation review)
- Week 5-6: Stage 2 audit (implementation assessment)
- Week 7: Certificate issuance
Total: About 6-8 weeks from kickoff to certification, assuming no major delays or gaps.
Compare that to the traditional 6-12 months, and the time savings are enormous. For companies racing to close deals or meet contractual deadlines, this speed can be business-critical.
ISO 27001 Requirements: What Controls Do You Need?
ISO 27001 is built around a set of requirements and controls. Let's break down what you actually need to do.
Core ISO 27001 Requirements (Clauses 4-10)
These are the mandatory organizational requirements that apply to everyone:
Clause 4 - Context of the Organization: Understand your organization, interested parties, and the scope of your ISMS.
Clause 5 - Leadership: Top management must demonstrate commitment and define an information security policy.
Clause 6 - Planning: Perform risk assessments and establish risk treatment plans and security objectives.
Clause 7 - Support: Provide necessary resources, competence, awareness, communication, and documented information.
Clause 8 - Operation: Implement and operate the processes needed to meet information security requirements.
Clause 9 - Performance Evaluation: Monitor, measure, analyze, evaluate, and audit your ISMS.
Clause 10 - Improvement: Continually improve the effectiveness of your ISMS, addressing non-conformities and taking corrective action.
These clauses are about establishing and maintaining your management system. They're process-oriented rather than technical.
Understanding ISO 27001 Annex A Controls
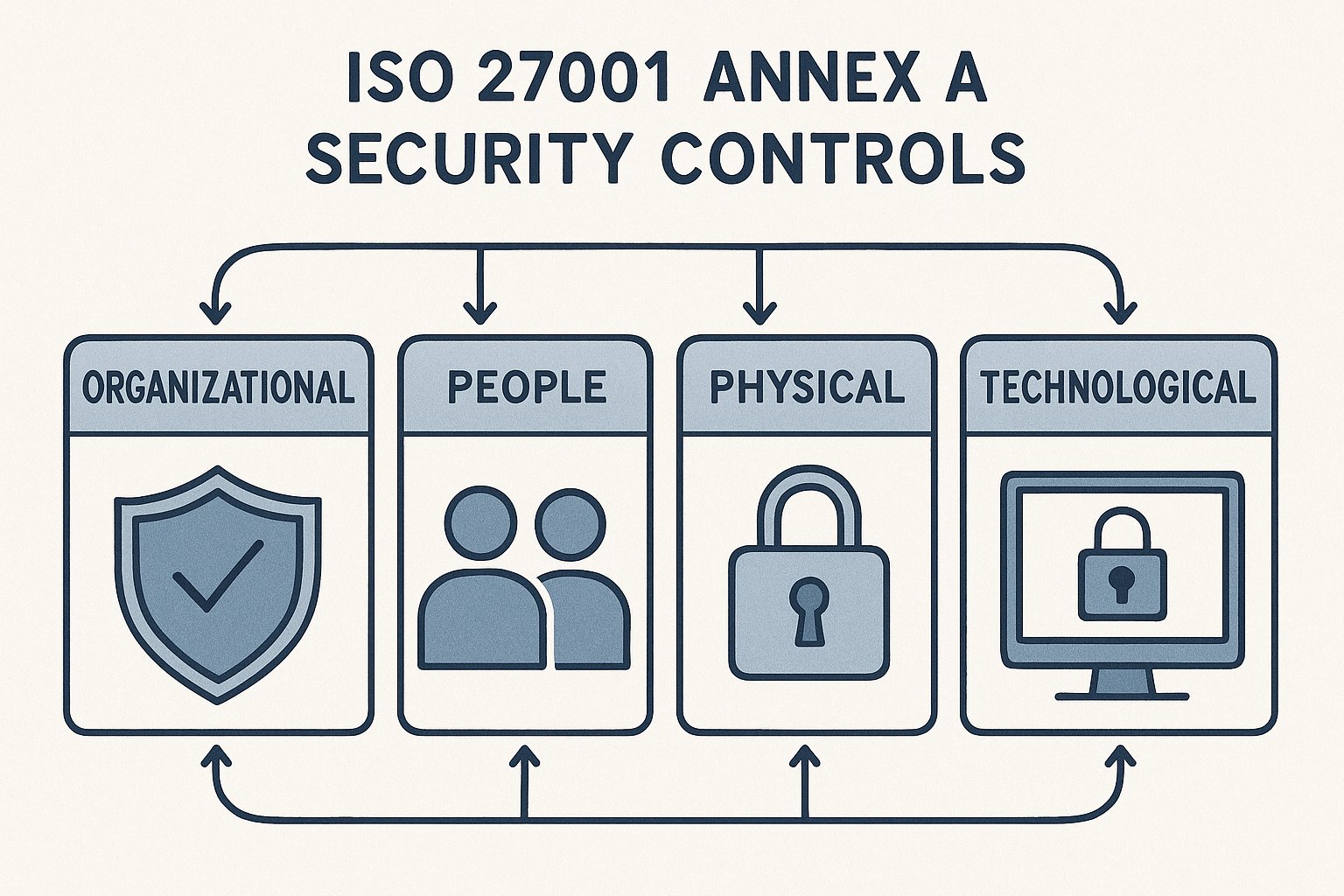
Annex A contains 93 specific security controls organized into four categories (as of the 2022 update):
Organizational Controls (37 controls): Things like information security policies, roles and responsibilities, asset management, access control, and supplier relationships.
People Controls (8 controls): Screening, terms and conditions of employment, security awareness training, and disciplinary processes.
Physical Controls (14 controls): Securing physical areas, protecting equipment, secure disposal, and clear desk/clear screen policies.
Technological Controls (34 controls): User access management, cryptography, network security, malware protection, logging and monitoring, backup, and incident management.
You document which controls you're implementing in your Statement of Applicability (SoA). For each control, you state whether it's applicable and justify your decision. If you're not implementing a control, you must explain why (usually because the risk doesn't apply to your organization).
Most tech companies implement the majority of technological controls (since they're software-heavy) and selectively implement physical controls (depending on whether they have offices or are fully remote).
Comp AI helps by:
- Recommending which controls make sense for your organization based on your tech stack and risk profile
- Providing ready-to-customize policy templates for each control
- Automatically collecting evidence that controls are functioning (for example, pulling MFA enforcement logs from Okta, encryption settings from AWS, or access review records from your identity provider)
This removes the guesswork and manual evidence gathering that traditionally consumes so much time.
ISO 27001 vs SOC 2 vs GDPR vs HIPAA: Which Do You Need?
Companies often ask: "We already have SOC 2 (or GDPR, or HIPAA). Do we really need ISO 27001 too?"
The answer depends on your business goals, but here's how ISO 27001 compares:
ISO 27001 vs SOC 2: Key Differences
Both standards address information security but differ in approach and recognition:
| Aspect | SOC 2 | ISO 27001 |
|---|---|---|
| Type | Attestation report | International certification |
| Geographic Focus | Primarily US | Global (especially Europe/Asia) |
| Scope | Service delivery controls | Comprehensive organizational ISMS |
| Output | Confidential report (Type I or II) | Public certificate |
| Framework | Customizable to specific services | Standardized requirements |
| Trust Service Criteria | 5 criteria (Security + 4 optional) | 93 Annex A controls (risk-based selection) |
| Best For | US SaaS companies, enterprise procurement | International markets, global enterprises |
Many companies get both. Comp AI makes this efficient by letting you manage multiple frameworks in one platform. Controls often overlap, so evidence collected for ISO 27001 can support your as well. Learn more about the differences in our .
ISO 27001 vs GDPR: How They Work Together
GDPR (General Data Protection Regulation) is a European privacy law governing how personal data of EU residents is processed. It's not optional if you handle EU personal data. It's a legal requirement.
ISO 27001 is a voluntary certification focused on information security. While it's not required by law, it helps demonstrate compliance with GDPR's security requirements.
How they relate:
- ISO 27001's controls align well with GDPR's security obligations (like encryption, access control, incident response)
- Having ISO 27001 can support your GDPR compliance efforts and provide evidence of "appropriate technical and organizational measures"
- But ISO 27001 alone doesn't make you GDPR compliant (GDPR also includes privacy-specific requirements like data subject rights, lawful basis, DPIAs, etc.)
Think of ISO 27001 as addressing the security side of GDPR. Many companies pursue both.
ISO 27001 vs HIPAA: Healthcare Compliance Comparison
HIPAA (Health Insurance Portability and Accountability Act) is a US regulation for protecting healthcare data. If you're a covered entity or business associate handling protected health information (PHI), HIPAA compliance isn't optional.
ISO 27001 is a voluntary international standard. However, many healthcare organizations appreciate it because ISO 27001's controls align well with HIPAA's Security Rule.
If you're in healthcare and handle PHI, you need HIPAA compliance. ISO 27001 can complement it and may satisfy some enterprise healthcare customers who prefer internationally recognized standards.
Comp AI supports both frameworks, letting you manage HIPAA and ISO 27001 requirements together efficiently.
Can You Pursue Multiple Compliance Frameworks at Once?
Absolutely. In fact, it's often more efficient because many controls overlap.
For example:
- Multi-factor authentication satisfies requirements in SOC 2, ISO 27001, HIPAA, and GDPR
- Encryption requirements are similar across frameworks
- Incident response processes can support all of them
- Access control policies largely carry over
With traditional approaches, managing multiple frameworks meant juggling different consultants, documents, and audit processes. With Comp AI, you implement controls once, and the platform maps them to multiple frameworks. Evidence collected for one audit supports others.
Companies pursuing both SOC 2 and ISO 27001 often complete them within weeks of each other, leveraging overlapping work.
5 Common ISO 27001 Challenges (And How to Overcome Them)
ISO 27001 certification comes with challenges. Here are the most common ones Comp AI sees, and how to address them:

Challenge 1: Understanding ISO 27001 Requirements
ISO 27001 documentation is dense and written in formal ISO language. First-timers often struggle to translate requirements into practical actions.
Solution: Use resources specifically designed for practitioners, not academics. Comp AI provides plain-English guidance for each requirement and control, with examples tailored to tech companies. Our platform asks questions like "Do you use multi-factor authentication?" and then automatically generates the corresponding policy language and documentation.
Use tools that interpret the standard for you (don't try to memorize it).
Challenge 2: Limited Time and Resources
Many companies underestimate the time and effort required. A single person trying to do ISO 27001 while juggling their regular job will struggle, especially using traditional methods.
Solution: Automation is your friend. AI-powered platforms can handle documentation, evidence collection, and control monitoring. Tasks that would otherwise require a dedicated team.
Comp AI AI agents work continuously, collecting evidence across your systems, flagging issues, and keeping your ISMS current. This turns ISO 27001 from a full-time project into a manageable process that runs largely on autopilot.
One customer told Comp AI: "Our CTO spent maybe 20 hours total on ISO 27001 over three weeks. Everything else was automated. That's unheard of."
Challenge 3: Complex Tech Stack Implementation
If you have a complex tech stack, legacy systems, or distributed teams, implementing controls consistently can be difficult.
Solution: Prioritize and integrate. Focus first on high-impact controls that address your most significant risks. Then use your existing tools.
Comp AI integrates with 100+ platforms (AWS, GCP, Azure, GitHub, Okta, Google Workspace, Slack, etc.). This lets you implement and monitor controls where your data and systems already live, without building parallel processes.
For legacy systems, you may need compensating controls or additional procedures. Document these clearly and involve them in your risk assessment.
Challenge 4: Keeping Documentation Current
ISO 27001 requires keeping documentation current. Policies, procedures, risk assessments: all must be reviewed and updated regularly.
Manually maintaining this documentation is tedious and error-prone. People forget, documents drift, and you end up with a paper ISMS that doesn't reflect reality.
Solution: Use platforms that version, track, and prompt updates automatically. Comp AI maintains a living ISMS where policies are version-controlled, review dates are tracked, and you're alerted when something needs attention.
When you make changes to your systems (add a new SaaS tool, onboard employees, change access policies), the platform prompts you to update relevant documentation. This keeps your ISMS aligned with actual operations.
Challenge 5: Passing Your First Audit
Audit anxiety is real. Even if you've done everything right, the thought of an auditor scrutinizing your work is stressful.
Solution: Prepare thoroughly and choose the right auditor. Do internal readiness reviews before the real audit. Comp AI includes pre-audit checks that simulate what auditors will review, flagging gaps so you can fix them beforehand.
Also, work with auditors who understand your industry and tech stack. Comp AI connects you with pre-vetted certification bodies familiar with fast-growing tech companies and automated compliance platforms. This avoids auditors who are confused by cloud-native architectures or expect everything to be documented in Word documents.
Our customers have a 100% first-time pass rate on audits. Proper preparation, good tools, and the right auditor make all the difference.
How Compliance Automation Makes ISO 27001 Faster
You can still do ISO 27001 the old way: hiring consultants, writing policies in Word, collecting screenshots manually. But why would you?
Modern compliance automation has transformed ISO 27001 from a months-long slog into a streamlined, efficient process. Here's what automation actually means in practice:
AI-Powered Policy Generation
Instead of writing security policies from scratch, AI generates customized drafts based on your organization's specific setup. You review and refine, but you're not staring at a blank page.
Comp AI analyzes your tech stack (what cloud provider, identity management, communication tools you use) and generates policies that reference your actual environment. The Access Control Policy mentions your SSO provider by name. The Data Protection Policy reflects your encryption methods.
This is intelligent customization. Policies that used to take weeks now take hours.
Automated Evidence Collection for Audits
Auditors need proof that your controls are working. Traditionally, this meant manually gathering screenshots, export reports, and emails. Hundreds of pieces of evidence for dozens of controls.
Automation changes this completely. AI agents connect to your systems and continuously collect evidence:
- MFA enforcement logs from Okta or Google Workspace
- Encryption settings from AWS, Azure, or GCP
- Access review records from your identity provider
- Code scanning results from GitHub
- Security training completion from your LMS
- Incident response records from your ticketing system
This evidence is timestamped, organized by control, and ready for auditors. No more scrambling the week before your audit trying to find proof that MFA was enabled six months ago.
Comp AI has collected over 2.6 million pieces of compliance evidence automatically for clients. That's work that would have taken thousands of hours manually.
Continuous Compliance Monitoring
ISO 27001 isn't just about passing an audit. It's about maintaining security over time. Automation enables continuous monitoring so you always know your compliance status.
If someone disables MFA on a critical account, Comp AI alerts you immediately. If a required security training isn't completed, you get notified. If a control drift happens (configuration change that breaks a control), the platform flags it.
This prevents compliance drift: the gap between what your documentation says and what's actually happening. With continuous monitoring, your ISMS stays current automatically.
AI-Driven Risk Assessment
Risk assessments can be overwhelming. You're supposed to identify all threats, vulnerabilities, assets, and then evaluate risks across combinations of these factors.
Automated platforms help by:
- Scanning your infrastructure to identify assets automatically
- Suggesting common threats and vulnerabilities relevant to your tech stack
- Providing risk scoring frameworks to prioritize
- Recommending controls based on identified risks
- Tracking risk treatment implementation
Comp AI turns risk assessment from a multi-week workshop into a guided, data-driven process that takes days. The AI asks questions, you provide answers, and it builds a comprehensive risk register.
Integration with Your Existing Tech Stack
One reason automation works so well is integration. Instead of building a parallel compliance world, modern platforms connect to your existing systems.
Comp AI integrates with 100+ tools across:
- Cloud infrastructure: AWS, Azure, GCP
- Identity and access: Okta, Auth0, Google Workspace, Azure AD
- Development: GitHub, GitLab, Bitbucket
- Communication: Slack, Microsoft Teams
- HR and training: BambooHR, Gusto, and LMS platforms
- Security: Cloudflare, Datadog, PagerDuty
These integrations let you implement controls where you work, not in a separate compliance silo. They also enable automated evidence collection directly from source systems, ensuring accuracy.
Expert Support When You Need It
Despite all this automation, there's still a human element. Comp AI combines AI with expert guidance: compliance specialists available via Slack to answer questions, review your setup, and guide you through decisions.
Automation handles the repetitive, time-consuming tasks. Humans handle judgment calls, strategic decisions, and anything requiring expertise.
This hybrid approach is why Comp AI customers achieve certification so quickly while maintaining quality. You get the speed of automation with the assurance of human expertise.
How to Get ISO 27001 Certified with Comp AI (Step-by-Step)
Let's walk through the practical steps using Comp AI AI-powered platform:
Step 1: Initial Setup and Scoping
You start with a brief onboarding call where Comp AI specialists help you define your ISMS scope. What systems, data, teams, and locations will be covered?
This typically takes 15-30 minutes. You'll discuss:
- Your business and main product/service
- What customer data you handle
- Your current security posture (MFA deployed? Encryption in use?)
- Target timeline for certification
Based on this conversation, the platform generates your initial scope statement and ISMS framework.
Step 2: Connect Your Systems
Next, you connect Comp AI to your tech stack via secure integrations. This usually takes 30-60 minutes depending on how many tools you use.
You'll typically connect:
- Cloud provider (AWS, GCP, Azure)
- Identity management (Okta, Google Workspace)
- Code repositories (GitHub, GitLab)
- Communication tools (Slack)
- HR systems (BambooHR, Rippling)
These integrations enable automated evidence collection and control monitoring. Comp AI only requests read access to security-relevant configurations. We don't modify your systems or access sensitive data.
Step 3: AI-Powered Risk Assessment
The platform guides you through a streamlined risk assessment process. Instead of blank spreadsheets, you answer targeted questions:
- What are your critical information assets?
- Who has access to sensitive data?
- What security threats concern you most?
- Where are your current vulnerabilities?
Based on your answers, the AI builds a risk register, scores risks, and recommends appropriate controls from Annex A. This takes 2-4 hours compared to weeks of traditional risk workshops.
You review and refine the risk assessment, adding any organization-specific risks the AI might have missed.
Step 4: Policy and Documentation Generation
Here's where automation shines. Based on your risk assessment and chosen controls, Comp AI AI generates your required documentation:
- Information Security Policy
- Risk Assessment Methodology
- Risk Treatment Plan
- Statement of Applicability
- Control-specific policies (Access Control, Cryptography, Incident Management, etc.)
- Procedures (Access Reviews, Change Management, Incident Response, etc.)
The AI customizes these documents to your organization (mentioning your actual tools, processes, and structure). They're not generic templates.
You review each document, make adjustments to fit your operations, and approve. This process takes 4-8 hours of actual work instead of weeks of writing.

Step 5: Control Implementation and Evidence Collection
With policies defined, you implement the controls (if not already in place) and Comp AI begins collecting evidence automatically.
For controls already implemented (like MFA or encryption), evidence collection starts immediately. The platform pulls logs, configurations, and reports from your connected systems.
For new controls, Comp AI provides implementation guidance. Need to set up quarterly access reviews? The platform walks you through it and then monitors to ensure it happens.
Throughout this phase, the Comp AI dashboard shows your readiness score: how many controls are fully implemented and evidenced, and which need attention.
Step 6: Readiness Review
Before engaging an auditor, Comp AI conducts an internal readiness review. This simulates what an auditor will check:
- Are all required documents complete and approved?
- Is evidence available for each control?
- Are there any gaps or inconsistencies?
The platform flags any issues so you can address them before the audit. Comp AI compliance specialists also review your ISMS and provide feedback.
This readiness review typically happens within 2-3 weeks of starting, confirming you're audit-ready.
Step 7: Certification Audit
Comp AI connects you with pre-vetted, accredited certification bodies and fast-tracks the audit scheduling. Instead of waiting months for an auditor, you typically schedule within 1-2 weeks.
Stage 1 Audit: The auditor reviews your documentation. Since everything is organized in Comp AI, you simply grant the auditor access to the platform. They review policies, risk assessment, SoA, and evidence. This usually takes 1-2 days remotely.
Stage 2 Audit: The auditor validates implementation. They interview staff (often via video call), test controls, and verify evidence accuracy. Comp AI provides auditors with organized evidence packages, making their job easier and faster.
The audit is collaborative. If the auditor has questions, you can address them in real time using evidence already in the platform.
Step 8: Certification and Ongoing Maintenance
Once the auditor is satisfied, they recommend certification. You receive your ISO 27001 certificate (usually within 1-2 weeks after Stage 2).
But the work doesn't stop there. Comp AI continues to:
- Monitor your controls automatically
- Collect evidence for future surveillance audits
- Alert you to any gaps or changes needed
- Track action items and deadlines
- Prepare you for annual surveillance and eventual recertification
Maintaining compliance becomes routine. Most Comp AI customers spend less than 5 hours per month on ISO 27001 maintenance: a fraction of what it would take manually.
Real Success Story: ISO 27001 in 6 Weeks
Let me share a story that illustrates what's possible with modern approaches.
A fast-growing SaaS company came to Comp AI in a bind. They had a major European enterprise prospect ready to sign a $300K annual contract, but the deal was contingent on ISO 27001 certification within 60 days.
The CEO had spent a week researching traditional approaches: hiring consultants (quoted 6-9 months and $50K+) or trying to DIY with templates (estimated 4-6 months of their CTO's time). Neither option worked with a 60-day deadline.
They discovered Comp AI through a fellow YC founder. Here's what happened:
Week 1: Onboarding call, system integrations, and scoping completed. The platform immediately began scanning their AWS and GCP environments, pulling security configurations.
Week 2: Risk assessment guided by AI (4 hours of CTO time), and policy generation (2 hours of review/approval). The AI drafted 15 policies customized to their tech stack.
Week 3: Control implementation (some were already in place, a few required configuration changes that took about 6 hours total), and evidence collection running automatically. The dashboard showed 85% readiness.
Week 4: Final documentation review, internal readiness check completed. Gaps addressed (mainly completing security training for two new hires). 100% ready.
Week 5: Stage 1 audit conducted remotely over 1.5 days. Auditor commented on how well-organized the documentation was.
Week 6: Stage 2 audit over 2 days. No major findings. Certification recommended.
Week 7: ISO 27001 certificate issued. Total time from start to certification: 44 days.
The deal closed the following week. The company's CEO later said: "ISO 27001 in six weeks seemed impossible. Comp AI made it shockingly straightforward. The automation handled everything the company dreaded (documentation, evidence collection, compliance tracking). The company just answered questions and made a few configuration changes."
Total cost: A fraction of what consultants quoted, and they now have an automated system maintaining their compliance continuously.
This is what modern ISO 27001 looks like: fast, efficient, and far less painful than the traditional approach.
ISO 27001 Certification Costs: What to Expect
Let's talk money. ISO 27001 certification involves several cost categories:
Auditor Fees
Certification body fees typically range from $5,000 to $15,000 depending on your organization size and scope. Larger organizations with complex operations pay more. A typical tech startup with 20-50 employees might expect around $8,000-$10,000 for the initial certification audit.
These fees usually cover:
- Stage 1 audit (documentation review)
- Stage 2 audit (implementation assessment)
- Certificate issuance
Annual surveillance audits cost less (often 30-50% of the initial audit fee).
Platform or Tool Costs
If you're using automation, there's a platform fee. Comp AI pricing starts at around $3,000 and varies based on company size and frameworks needed.
This typically includes:
- Unlimited users
- All necessary integrations
- AI-generated documentation
- Automated evidence collection
- Continuous monitoring
- Expert support via Slack
- Pre-vetted auditor connections
Many companies find the platform more than pays for itself through time savings alone. If your CTO's time is worth $200/hour, saving 200 hours is $40,000 in avoided opportunity cost (not to mention faster time to revenue from deals you can now close).
Internal Labor Costs
Even with automation, someone in your organization needs to spend time on ISO 27001. However, the time required is dramatically reduced.
Traditional approach: Expect 300-500 hours of internal time spread across multiple people (often a project manager, CTO, operations lead, etc.). At typical tech company salary rates, that's $60,000-$100,000 in opportunity cost.
Automated approach with Comp AI: 20-40 hours of CTO/security lead time for decision-making and review, plus maybe 10-20 hours from other team members for interviews and implementation tasks. Total: 30-60 hours, or $6,000-$12,000 in opportunity cost.
The difference is massive.
Consultant Costs (If You Go That Route)
If you hire consultants instead of using a platform, expect $20,000-$50,000+ for ISO 27001 project assistance. Senior consultants can charge $200-$400/hour.
Consultants provide expertise but don't scale efficiently. They'll help you build your ISMS, but once they're gone, you're on your own for maintenance. And their timelines tend to be long (6-9 months is common).
Total Cost Comparison
| Cost Category | Traditional Consultant-Led | DIY Approach | Automated with Comp AI |
|---|---|---|---|
| Consultant/Platform Fees | $30,000-$50,000 | $0 | $3,000-$8,000 |
| Auditor Fees | $10,000-$15,000 | $10,000-$15,000 | $8,000-$12,000 |
| Internal Time Cost | $60,000-$100,000 | $80,000-$120,000 | $6,000-$12,000 |
| Total Cost | $100,000-$165,000 | $90,000-$135,000 | $17,000-$32,000 |
| Timeline | 6-12 months | 6-12 months | 4-8 weeks |
| Risk Level | Medium (consultant dependent) | High (no expert guidance) | Low (expert + automation) |
| Ongoing Maintenance | High cost | High cost | Low cost (automated) |
The automated approach is not only faster but also more cost-effective by a factor of 3-5x.
Complete ISO 27001 Certification Checklist
Here's a comprehensive ISO 27001 compliance checklist you can use to track your certification journey:

Planning Phase
- Obtain leadership commitment and approval
- Define ISMS scope (systems, data, teams, locations)
- Assemble project team or choose compliance platform
- Set target timeline for certification
- Budget for auditor fees and tools
Risk Assessment and Treatment
- Identify information assets within scope
- Identify threats and vulnerabilities
- Assess and score risks
- Determine risk treatment approach for each risk
- Select applicable Annex A controls
- Document risk treatment plan
Documentation
- Draft Information Security Policy
- Create Statement of Applicability (SoA)
- Document risk assessment methodology
- Write control-specific policies (access control, cryptography, etc.)
- Create required procedures (incident response, change management, access reviews, etc.)
- Obtain management approval for all policies
Control Implementation
- Implement selected Annex A controls
- Deploy technical controls (MFA, encryption, logging, etc.)
- Establish operational procedures (access reviews, backups, etc.)
- Set up physical controls if applicable (office security, device management)
- Conduct security awareness training for staff
- Implement incident management process
Evidence Collection
- Begin collecting evidence for each control
- Organize evidence by control and requirement
- Ensure evidence covers the required time period
- Document any exceptions or findings
Internal Readiness
- Conduct internal ISMS review
- Perform internal audit or readiness assessment
- Address any gaps identified
- Ensure all required documents are complete and current
Certification Audit
- Select and engage accredited certification body
- Schedule Stage 1 audit
- Provide auditor with access to documentation
- Complete Stage 1 audit (documentation review)
- Address any Stage 1 findings
- Schedule Stage 2 audit
- Complete Stage 2 audit (implementation assessment)
- Address any Stage 2 findings or non-conformities
- Receive ISO 27001 certificate
Ongoing Maintenance
- Establish continuous monitoring processes
- Schedule regular management reviews (at least annually)
- Conduct internal audits
- Maintain evidence collection
- Update documentation as systems or processes change
- Prepare for annual surveillance audits
- Plan for 3-year recertification
If you're using Comp AI, most of these items are guided and tracked automatically within the platform. You'll see your progress in real time and get alerts for anything requiring attention.
How to Maintain ISO 27001 Compliance Year-Round
Getting certified is just the beginning. The real value of ISO 27001 comes from maintaining it: ensuring your security posture stays strong and you're ready for surveillance audits without scrambling.
Continuous Evidence Collection
Evidence doesn't stop after the initial audit. Surveillance auditors will want to see that controls remained operational throughout the year.
Comp AI handles this automatically. Every week, month, and quarter, evidence is collected from your integrated systems:
- Access logs showing MFA usage
- Encryption status checks
- Employee security training completion
- Access reviews and approvals
- Incident response logs
- System availability and backup verification
This ongoing evidence stream means you're always audit-ready. When the surveillance audit comes, you don't need to prepare (the evidence is already there).
Monitoring for Control Drift
Systems change. Employees join and leave. Configurations get modified. Over time, it's easy for your actual security posture to drift from what your documentation says.
Continuous monitoring detects this drift:
- If someone disables a critical security setting, you get alerted
- If an employee hasn't completed required training, you're notified
- If a quarterly access review is overdue, reminders are sent
- If new risks emerge (a vendor breach, a new vulnerability), you're informed
This proactive monitoring keeps your ISMS alive and effective, not just a set of documents gathering dust.
Scheduled Reviews and Updates
ISO 27001 requires periodic reviews:
- Management reviews (at least annually): Leadership reviews ISMS performance, approves changes
- Internal audits: Your organization audits itself to identify gaps before external audits
- Policy reviews: Ensuring policies remain current and relevant
- Risk reassessments: Periodically reviewing if risks have changed
Comp AI schedules these automatically, sends reminders, and provides templates to make them efficient. What might take days of coordination happens smoothly in hours.
Handling Changes
When your organization changes (new systems, new services, new locations, new team members), your ISMS must adapt.
Comp AI makes this manageable:
- New employee onboarding: Automatically includes security training and policy acknowledgment
- New system integration: Connect it to the platform, assess risks, implement controls
- Policy updates: Version-controlled with approval workflows
- Risk reassessment triggers: When significant changes happen, the platform prompts you to review and update your risk assessment
This keeps your ISMS aligned with reality, which is exactly what auditors want to see.
Surveillance Audit Preparation
Annual surveillance audits are lighter than the initial certification audit, but you still need to prepare.
With Comp AI, preparation is minimal:
- Review the dashboard to confirm all controls show green (evidence current, no gaps)
- Address any flagged issues
- Grant auditor access to the platform
- Schedule the audit
Since evidence has been collecting continuously, there's no mad rush to gather screenshots or run reports. The surveillance audit becomes routine: maybe half a day of your time for preparation, and 1-2 days for the audit itself.
Comp AI customers consistently report that surveillance audits are "almost too easy" (because the system has been maintaining compliance automatically all year).
Scaling Your ISMS
As your company grows, your ISMS needs to scale:
- More employees to train
- More systems to secure
- More data to protect
- Maybe expanding to new geographies or frameworks
Comp AI scales with you. Adding users, integrating new tools, and expanding scope are straightforward. The automation that worked for 20 employees works just as well for 200.
Some companies even expand their ISMS scope or add frameworks (like adding SOC 2 or GDPR to their existing ISO 27001 certification). With overlapping controls and shared evidence, this expansion is far less work than doing each framework separately.
Frequently Asked Questions About ISO 27001 Certification
How long is an ISO 27001 certificate valid?
ISO 27001 certificates are valid for three years from the date of issuance. However, you must undergo surveillance audits annually (typically at 12 and 24 months after certification) to maintain the certificate. At the end of three years, you undergo a recertification audit to renew.
Can small companies get ISO 27001 certified?
Absolutely. ISO 27001 scales to organizations of any size. Small companies often have simpler systems and fewer assets, which can make certification faster and more straightforward. Comp AI has helped companies with as few as 5 employees achieve ISO 27001 certification.
The key is scoping appropriately and focusing on relevant controls. You don't need enterprise-scale processes (just effective ones proportional to your risks).
Do I need a consultant to get ISO 27001 certified?
No. While consultants can help, they're not required. Many companies successfully achieve ISO 27001 using automated platforms like Comp AI without hiring expensive consultants.
Platforms provide the expertise through built-in guidance, templates, and access to compliance specialists. This gives you consultant-level support at a fraction of the cost.
What happens if I fail the ISO 27001 audit?
If the auditor identifies major non-conformities (significant gaps in your ISMS), they won't recommend certification until you address them. You'll need to fix the issues and have the auditor verify the corrections (which might be done remotely or as a follow-up visit).
Minor non-conformities can often be addressed through a corrective action plan without delaying certification significantly.
The good news: with proper preparation (like the readiness reviews Comp AI conducts), failures are rare. Our customers have a 100% first-time pass rate because gaps are identified and fixed before the audit even starts.
Can ISO 27001 be done remotely?
Yes. Especially post-COVID, remote audits have become standard. Most of the process can be done remotely:
- Documentation review (Stage 1) is almost always remote
- Interviews can be conducted via video call
- Evidence review happens through shared platforms
Stage 2 may include some on-site components if you have physical offices with sensitive data, but even this is often handled remotely by reviewing video tours, screenshots, and procedures.
Comp AI facilitates remote audits by providing auditors with organized, cloud-based access to all documentation and evidence. Geographic location isn't a barrier.
How often do I need to update my ISO 27001 documentation?
You should review and update documentation whenever significant changes occur:
- Major system changes or new technology
- Organizational restructuring
- New risks identified
- Changes in legal or regulatory requirements
- After incidents or near-misses
ISO 27001 requires at least annual management reviews where you assess if policies and procedures need updates.
With Comp AI, version control is built in. You can update documents easily, and the platform tracks what changed and when. This makes compliance with ISO 27001's documentation requirements straightforward.
What's the difference between ISO 27001 and ISO 27002?
ISO 27001 is the certification standard. It specifies requirements for establishing, implementing, maintaining, and continually improving an ISMS. It's what you get audited against.
ISO 27002 is a supporting code of practice. It provides detailed guidance and best practices for implementing the security controls listed in ISO 27001's Annex A. It's not for certification (it's a reference guide).
Think of ISO 27001 as the "what" (what you must do) and ISO 27002 as the "how" (how to do it well).
Can I do ISO 27001 for just part of my organization?
Yes. This is called scoping, and it's common. You might certify just your SaaS platform and the teams that support it, while excluding other parts of your business.
For example, a company might scope ISO 27001 to cover:
- Their cloud-based software platform
- The engineering and DevOps teams
- Customer data processing activities
While excluding:
- Internal IT systems unrelated to the product
- Marketing operations
- Non-technical departments
The certificate will clearly state the scope, so customers know exactly what's covered. This approach lets you achieve certification faster and keeps the effort manageable.
Do I need ISO 27001 if I already have SOC 2?
It depends on your business needs. SOC 2 is excellent for US customers but less recognized internationally. If you're targeting European or Asian markets, or if enterprise customers specifically ask for ISO 27001, then yes (you should pursue it).
Many companies have both certifications. The good news: lots of controls overlap, so achieving both isn't double the work. With Comp AI, you manage them together, implementing controls once and mapping them to both frameworks.
How much does it cost to maintain ISO 27001 annually?
Annual maintenance costs include:
- Surveillance audit fees: $3,000-$5,000 per year (less than the initial audit)
- Platform or tool fees (if using automation): Ongoing subscription, typically $3,000-$8,000/year depending on company size
- Internal time: With automation, maybe 5-10 hours per month reviewing dashboards, addressing alerts, and conducting periodic reviews
Total annual cost with Comp AI: roughly $6,000-$13,000, compared to $15,000-$30,000+ if maintaining manually or with consultants.
Maintenance is significantly cheaper than initial certification, especially with automated continuous monitoring.
Why Choose Comp AI for ISO 27001 Certification
If you've made it this far, you've seen references to Comp AI throughout this guide. Let's be direct about why Comp AI is the fastest, most efficient way to achieve ISO 27001 certification:
Unmatched Speed
Comp AI has a proven track record of getting companies audit-ready in 14 days (sometimes faster). This isn't marketing hype. Comp AI has done it repeatedly for clients who had urgent deadlines.
The speed comes from:
- AI-generated documentation in minutes, not weeks
- Automated evidence collection from 100+ integrated tools
- Pre-built templates customized to your tech stack
- Guided workflows that eliminate guesswork
- Expert support via Slack for quick answers
You're not slower because you're lazy. You're slower because traditional approaches waste time on manual tasks that should be automated.
True Automation
Many platforms claim automation but still leave you doing most of the work. Comp AI actually delivers on the automation promise:
- 90% of compliance tasks automated: Comp AI's AI agents handle evidence collection, risk analysis, policy generation, and continuous monitoring
- 100% first-time audit pass rate: Because Comp AI doesn't let you go to audit with gaps
- Continuous compliance: Not just for the initial audit, but ongoing (set it and forget it)
One customer said: "We thought we'd spend hours every week on compliance. With Comp AI, I check the dashboard once a month, and everything just works."
Built for Tech Companies
Comp AI was built by engineers for engineers. Comp AI understands cloud-native architectures, modern dev practices, and the tools startups actually use.
Comp AI integrates natively with AWS, GCP, Azure, GitHub, Okta, Slack (the tools you already rely on). You don't need to change how you work or adopt clunky compliance-specific tools.
Comp AI's policies and controls are written for tech companies, not generic enterprises. They make sense for your environment.
Transparent Pricing
No hidden fees, no surprises. You know upfront what it costs. Starting at just $3,000 for smaller companies, with clear pricing tiers as you grow. And Comp AI offers a money-back guarantee if you're not satisfied.
Compare that to consultants who bill by the hour with no predictable endpoint, or platforms that nickel-and-dime for every feature.
Expert Support
Comp AI isn't just software (you get real humans who are compliance experts). Reach Comp AI via Slack and get answers typically within minutes (during business hours). No ticketing systems, no waiting days for a response.
Comp AI's team has helped hundreds of companies through ISO 27001, SOC 2, HIPAA, and other frameworks. Comp AI knows where first-timers get stuck and how to unstick you quickly.
Proven Results
Comp AI is trusted by 4,000+ companies. Comp AI has facilitated hundreds of successful ISO 27001 certifications with zero failures.
Comp AI's customers include YC-backed startups, fast-growing SaaS companies, healthcare innovators, and international teams. They chose Comp AI because Comp AI is simply the fastest, most reliable way to get compliant.
Get Started with ISO 27001 Certification Today
ISO 27001 doesn't have to be a months-long ordeal that distracts from growing your business. With the right approach, you can achieve certification in weeks while building a security posture that actually protects your organization and impresses customers.
Here's how to get started:
1. Book a demo with Comp AI: Comp AI will show you exactly how the platform works, walk through your specific situation, and map out a timeline to certification.
2. Connect your systems: In about an hour, you'll integrate Comp AI with your tech stack. Comp AI's team guides you through this step-by-step.
3. Let AI do the heavy lifting: While you focus on your product and customers, Comp AI's AI agents generate documentation, collect evidence, and prepare you for audit.
4. Get certified: In as little as 4-6 weeks from start to finish, you'll have your ISO 27001 certificate and can start closing those enterprise deals.
Thousands of companies have trusted Comp AI to handle their compliance. Comp AI's 100% audit success rate and industry-leading speed speak for themselves.
Don't let compliance slow you down. Book a demo with Comp AI today and see how fast you can get ISO 27001 certified.
Looking for more compliance resources?
- How to Get SOC 2 Certification - Learn about SOC 2 timelines and how to accelerate them
- SOC 2 Compliance Checklist - Essential checklist for SOC 2 readiness
- Best Compliance Management Software - See how different platforms stack up
- Benefits of ISO 27001 Certification - Understand what makes ISO 27001 valuable
Frequently Asked Questions
How quickly can I realistically get ISO 27001 certified?
With Comp AI, companies typically achieve audit readiness in 2-3 weeks and receive their certificate within 6-8 weeks total. The timeline depends on your current security posture and how quickly you can implement any required controls. Traditional approaches take 6-12 months.
Do I need technical expertise to use Comp AI?
No. While having a technical background helps, Comp AI is designed to guide non-experts through the entire process. Comp AI's AI asks questions in plain language, generates documentation for you, and Comp AI's support team is always available to help. Many of Comp AI's customers are founders or operations leads without deep security backgrounds.
What if I don't have many security controls in place yet?
That's fine. Comp AI helps you implement controls as part of the certification process. The platform recommends specific controls based on your risks, provides implementation guidance, and verifies they're working properly. You'll end up more secure than before (which is the whole point).
Can I get multiple certifications at once (SOC 2 + ISO 27001)?
Absolutely. Because many controls overlap between frameworks, pursuing multiple certifications together is often more efficient than doing them separately. Comp AI manages multiple frameworks in one platform, so evidence collected for ISO 27001 can support your SOC 2 audit and vice versa. Companies often complete both within 8-10 weeks.
What happens after I get certified?
Comp AI continues monitoring your compliance year-round. You'll undergo annual surveillance audits (lighter than the initial audit) and recertification every three years. The platform handles evidence collection continuously and alerts you to any gaps, making ongoing compliance nearly effortless.
How much will ISO 27001 certification cost?
Total costs including auditor fees, platform subscription, and internal time typically range from $17,000-$32,000 with Comp AI (compared to $100,000-$165,000 for traditional consultant-led approaches). Comp AI offers transparent pricing with no hidden fees.
Is Comp AI suitable for my industry?
Comp AI supports companies across industries (SaaS, fintech, healthtech, AI/ML, e-commerce, and more). Comp AI handles industry-specific requirements and can customize controls to your needs. If you handle any type of sensitive data, Comp AI can help you protect it and prove it to customers.
What if I have questions during the process?
You'll have direct Slack access to Comp AI compliance specialists throughout your certification journey. Average response time is under 5 minutes during business hours. No ticketing systems or waiting days for answers (just fast, expert help when you need it).
Want to get ISO 27001 certified in weeks instead of months? Schedule a demo with Comp AI to see the platform in action and get a customized timeline for your organization.
Share this article
Help others discover this content