At its core, getting ISO 27001 certified is all about building, running, and constantly fine-tuning an Information Security Management System (ISMS). It's a structured way for companies to get a handle on security risks that could mess with the confidentiality, integrity, and availability of their data—and their customers' data.
What Are the Core ISO 27001 Requirements
Before we get into the nitty-gritty of clauses and controls, let's get the philosophy right. Think of ISO 27001 less like a rigid checklist and more like a blueprint for building a fortress around your company's most valuable asset: its information.
The heart of it all is the Information Security Management System (ISMS). This isn't just some software you install. It's the command center for your entire security operation—a living framework of policies, procedures, and controls that dictates how you protect sensitive data.
The Purpose Behind the Process
Nailing the ISO 27001 requirements is about so much more than just passing an audit. It’s about weaving a culture of security into the very DNA of your organization. Taking this proactive stance on data protection gives you a serious edge in the market.
- Building Customer Trust: Certification is a clear signal to clients and partners that you don't mess around when it comes to their data.
- Ensuring Business Continuity: A solid ISMS means your company can take a punch from a security incident and get back on its feet quickly.
- Navigating Digital Threats: It gives you a structured game plan for spotting, assessing, and shutting down the constantly evolving world of cyber threats.
The real goal of ISO 27001 is to shift security from a reactive, "firefighting" mode to a proactive, risk-managed discipline. You're building a system that learns and adapts to new threats and business goals.
A Global Standard for Security
The standard's effectiveness isn't just talk; its global adoption proves it. As of 2023, more than 70,000 organizations across 150+ countries have achieved ISO 27001 certification. That explosive growth shows just how valuable it is for businesses trying to manage sensitive data and avoid the massive costs of a breach.
This table provides a high-level overview of the fundamental components of the ISO 27001 standard, helping you quickly grasp its structure and key focus areas.
The Pillars of ISO 27001 at a Glance
| Component | Purpose | Key Focus Area |
|---|---|---|
| Mandatory Clauses | To establish the framework for the ISMS. | Defines how to scope, implement, operate, and improve the system. |
| Annex A Controls | To provide a checklist of security controls. | Offers specific measures to mitigate identified information security risks. |
| Risk Assessment | To identify and evaluate security threats. | Forms the basis for selecting appropriate Annex A controls. |
| Continual Improvement | To ensure the ISMS evolves and remains effective. | Requires regular monitoring, reviews, and updates to the security posture. |
Ultimately, achieving this certification is a powerful statement. It tells the world that your organization has a comprehensive, internationally respected system for protecting information. This journey starts with understanding each requirement, which is why a detailed is an indispensable tool for mapping out your path to success. It ensures every angle is covered, from physical security to employee training, creating a truly resilient business.
Breaking Down the Mandatory Clauses: Clauses 4 Through 10

While everyone talks about the Annex A controls, it's Clauses 4 through 10 that form the strategic heart of your Information Security Management System (ISMS). Think of them less as bureaucratic hurdles and more as the chapters in your security operations playbook. They're the logical, step-by-step instructions for building a security framework that actually works.
Each clause builds on the one before it, creating a tightly interconnected system. This isn't just a checklist; it's a philosophy. ISO 27001 is designed to treat security as an ongoing process, not a one-and-done project.
So, let's walk through what these mandatory clauses actually mean in practice.
Clause 4: Context of the Organization
Before you can defend your kingdom, you have to survey the land. That’s Clause 4 in a nutshell. It forces you to look both outward and inward to get a clear picture of the environment your ISMS will live in.
This means identifying all your interested parties—everyone from customers and regulators to your own employees and shareholders—and figuring out what they expect from you on security. It also means recognizing the internal and external forces at play, like shifting market competition, your own company culture, or new data privacy laws that could throw a wrench in your plans.
Get this part right, and everything else falls into place. Skip it, and your ISMS will operate in a vacuum, protecting against the wrong threats or completely missing the mark on what your stakeholders actually need.
Clause 5: Leadership
Okay, you've mapped out the territory. Now you need to appoint your generals. Clause 5 is all about top-down commitment. This isn't a task you can just toss over the fence to the IT department; the standard is crystal clear that senior leadership must be actively involved.
Leadership’s job is to:
- Establish the Information Security Policy: This is the high-level mission statement, the declaration of your organization's security goals and direction.
- Assign Roles and Responsibilities: No ambiguity. Everyone needs to know exactly who is responsible for what within the ISMS.
- Provide Resources: Real commitment is shown through budget, people, and the right tools.
An ISMS without genuine leadership buy-in is just a paper-pusher's dream—and an auditor's nightmare. When auditors see executives actually championing the security policy, they know the commitment is real.
Clause 6: Planning
You’ve got your mission and your leaders. Now it’s time to draw up a battle plan. Clause 6 is where you get systematic about tackling risks and opportunities. It’s the bridge between the high-level context you figured out in Clause 4 and the specific security controls you'll eventually pick from Annex A.
The core of this clause is the risk assessment and risk treatment process. You have to identify what could possibly go wrong with your information, analyze how likely it is to happen and how bad it would be, and then decide how you're going to handle it. The goal isn't to eliminate all risk—that's impossible. It's about making smart, informed decisions to knock it down to an acceptable level.
This is also where you set clear, measurable security objectives. For example, a goal might be something like, "Reduce successful phishing incidents by 25% within the next fiscal year."
Clause 7: Support
An army can't fight without supplies, training, and a way to communicate. Clause 7 is all about making sure your ISMS has the support structure it needs to actually function.
This covers a few critical areas:
- Resources: Having the right people, tech, and funding to keep the ISMS running.
- Competence: Making sure your team has the skills and training for their security roles.
- Awareness: Ensuring every single employee understands the security policy and their personal role in upholding it.
- Communication: Setting up clear channels for talking about security issues, both inside the company and with external parties.
- Documented Information: Creating and maintaining all the required policies, procedures, and records. It's the paper trail that proves you're doing what you say you're doing.
Clause 8: Operation
This is where the rubber meets the road. Clause 8 is about taking all those plans from Clause 6 and putting them into action. It’s the "doing" part of the cycle.
This involves actually conducting your risk assessments and implementing the treatment plan you came up with. If your plan called for a new access control policy or a formal vendor security review process, this is the clause where you make it happen. You're officially operationalizing your security strategy.
Clause 9: Performance Evaluation
You've built your fortress and deployed your troops. But how do you know if your defenses are actually holding up? Clause 9 is about measuring and evaluating your ISMS to see if it’s effective.
This requires three key activities:
- Monitoring and Measurement: Tracking key security metrics to see if you’re hitting your objectives.
- Internal Audits: Conducting regular self-inspections to find weaknesses before an external auditor does. It’s better to find your own problems.
- Management Reviews: Regular meetings where leadership looks at the ISMS performance data and makes strategic decisions for the future.
Clause 10: Improvement
The final clause, Improvement, drives home the core idea that security is never "done." It’s a continuous loop. This clause requires you to constantly refine your ISMS.
When you find nonconformities—areas where you’re not meeting a requirement—from your audits or performance reviews, you have to take corrective action. This isn’t about blaming people; it's about digging in, finding the root cause of the problem, and fixing the underlying process so it doesn't happen again. This cycle of planning, doing, checking, and acting is what makes your security posture stronger over time.
By linking all these clauses together, you create a living, breathing management system. To get a better handle on how all these pieces form a cohesive whole, check out our guide on Information Security Management Systems and see how they act as the central nervous system for your entire security program.
Making Sense of the Annex A Controls
If the mandatory clauses are the strategic blueprint for your security fortress, then Annex A is your armory. It’s a detailed catalog of 93 security controls, and it often feels like the most intimidating part of the entire standard. But here’s the secret: you don’t have to implement every single one.
Think of it as a huge collection of defensive tools. You wouldn’t equip a desert outpost with naval cannons, right? Instead, you pick the specific weapons and armor—the controls—that are best suited to defend against the unique threats you found during your risk assessment (Clause 6).
This approach makes sure your security efforts are efficient, relevant, and targeted. You're not just checking boxes; you're building a practical, custom defense system. To make things manageable, the 93 controls are grouped into four distinct themes.
Organizational Controls
This is the biggest group, with 37 controls that create the foundational policies and procedures for your ISMS. Think of these as the rules of engagement and the command structure for your entire security operation. They aren't about a specific piece of software but about how the organization governs security as a whole.
These controls cover a lot of ground, including:
- Information security policies: The high-level documents that set the direction for your security program.
- Roles and responsibilities: Clearly defining who is accountable for protecting specific information assets.
- Asset management: Knowing what data you have, where it lives, and how valuable it is.
- Supplier relationships: Making sure your vendors and partners meet your security standards.
For instance, control A.5.1 (Policies for information security) requires a documented, board-approved policy. This isn't just paperwork; it’s a clear signal from leadership that security is a non-negotiable priority. This control ensures everyone is marching to the same beat.
People Controls
With 8 controls, this theme zeroes in on the human element of security. Your people can be your strongest defense or your weakest link. These controls are designed to ensure they are a well-trained, aware, and reliable part of your security posture.
Imagine these as the training drills for your sentries. It’s about managing security risks across the entire employee lifecycle—from the moment they are hired to the day they leave. Key areas include background screening, security awareness training, and having a disciplinary process for security slip-ups.
A common mistake is treating security training as a one-time event. Effective 'People Controls' mean creating an ongoing culture of security awareness, where employees are continuously reminded of their role in protecting company data.
Physical Controls
This group has 14 controls dedicated to securing the physical world where your data and systems live. We often focus on digital threats, but a stolen laptop or someone sneaking into a server room can be just as devastating as a hack.
These controls are the locks, fences, and security guards for your tangible assets. They cover everything from securing offices and data centers to protecting equipment from theft or environmental damage. A great example is A.7.2 (Physical entry), which requires measures to stop unauthorized people from just walking into sensitive areas.
This diagram shows how the 93 Annex A controls are split across the four main themes.
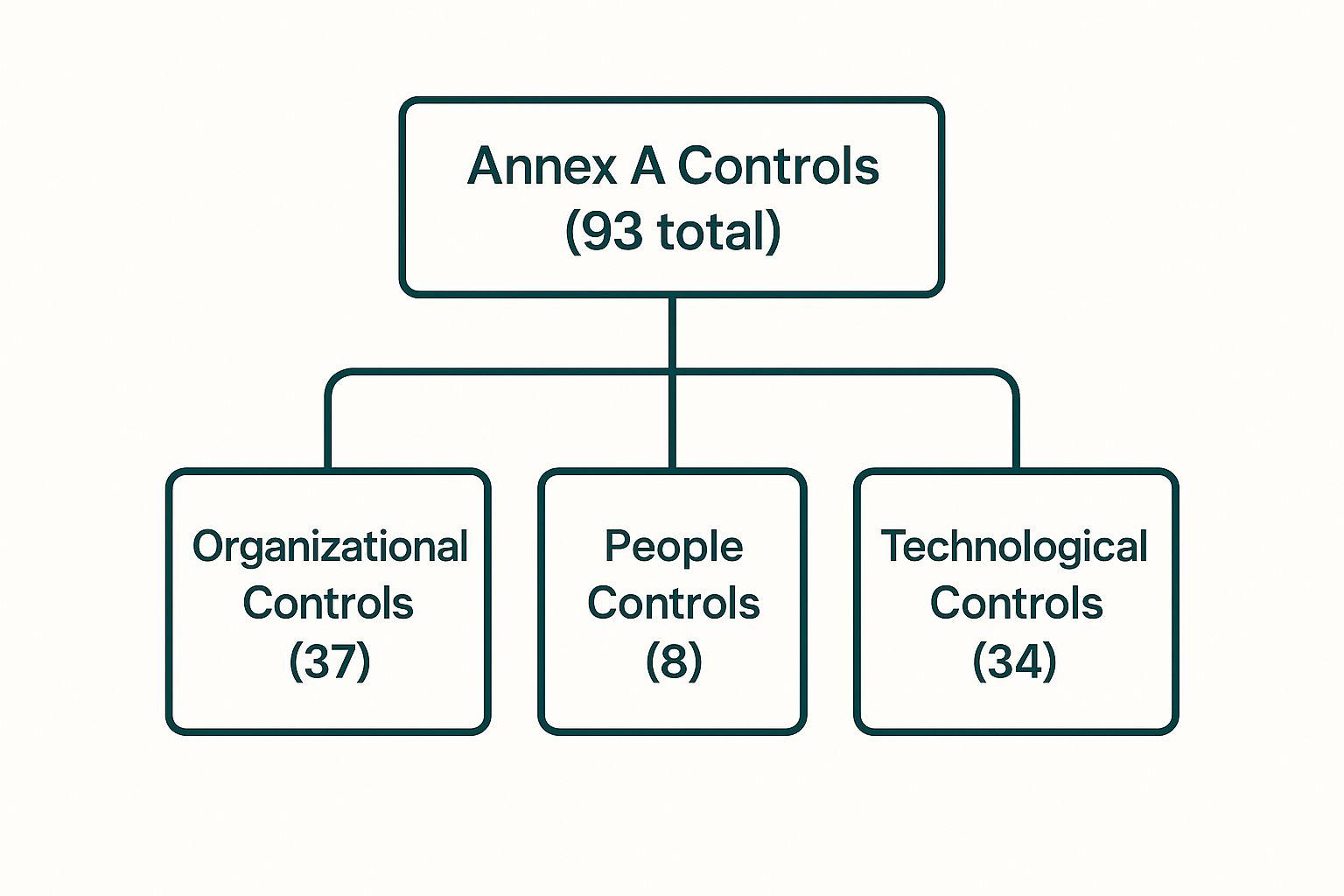
As you can see, Organizational and Technological controls make up the bulk of the Annex A options. This really highlights their central role in building a solid ISMS.
Technological Controls
Finally, the 34 Technological Controls are the digital locks and keys for your information systems. This is what most people think of when they hear "cybersecurity": firewalls, encryption, antivirus software, and access rights.
These controls are all about using technology to enforce your security policies. They make sure that only the right people can access specific data and that information is protected both when it's sitting on a server and when it's being sent across the internet.
One of the most critical controls here is A.5.15 (Access control). This single control is the bedrock of preventing unauthorized data access. It requires you to define and implement rules governing who can see, change, or use information assets. To get a better handle on this, you can learn more about crafting an effective access control policy that lines up with ISO 27001 standards.
The Statement of Applicability
After you've gone through all 93 controls, your decisions have to be recorded in one crucial report: the Statement of Applicability (SoA). This document is a non-negotiable requirement for ISO 27001 certification.
For each of the 93 controls, your SoA has to state:
- Whether you've decided to implement the control.
- Why you made that decision (linking it directly to your risk assessment).
- A quick description of how the control has been implemented.
The SoA becomes a central reference point for your auditors. It proves that you've done a thorough risk assessment and made deliberate, justified decisions about your security. It’s the ultimate proof that your ISMS is truly built for your organization’s needs, turning Annex A from a scary checklist into a powerful tool for smart risk management.
Navigating The Certification Audit Process

The certification audit can feel like the final exam, but it’s really more of a collaborative review to confirm all your hard work has paid off. Think of it like bringing in a master architect to inspect your newly built security fortress. They aren't there to find fault, but to confirm the structure is sound and built according to the blueprint.
This process is a formal verification by an accredited, third-party certification body. It’s the step that officially confirms your Information Security Management System (ISMS) meets all ISO 27001 certification requirements. The journey is broken into two main stages, followed by ongoing checks to make sure you stay on track.
The Stage 1 Audit: A Documentation Review
The first phase, the Stage 1 audit, is basically a readiness check. The auditor pores over your ISMS documentation to confirm you have all the necessary policies, procedures, and foundational elements in place. It's like they're reviewing the architectural plans before touring the completed building.
During this stage, the auditor will focus on:
- The scope of your ISMS.
- Your risk assessment methodology and results.
- The all-important Statement of Applicability (SoA).
- Evidence of leadership commitment and policy documentation.
The outcome of Stage 1 is a report that flags any areas of concern or potential nonconformities. This gives you a clear punch list of items to fix before the much more detailed Stage 2 audit kicks off.
The Stage 1 audit is your chance to get valuable feedback directly from the auditor. Treat it as a dress rehearsal to ensure a smooth and successful Stage 2 experience.
The Stage 2 Audit: An Implementation Review
Once you’ve addressed any findings from Stage 1, it’s time for the Stage 2 audit. This is the main event. Auditors will come on-site (or connect remotely) to see your ISMS in action. They'll interview your team, observe processes, and check records to verify that you’re actually doing what your documentation says you do.
This hands-on review checks if your controls are effective and if your team is following the procedures you’ve laid out. Auditors want to see that your ISMS is a living, breathing part of your organization—not just a binder of documents collecting dust on a shelf. If you're prepping for this, a good IT security audit checklist can be a lifesaver.
Addressing Nonconformities and Achieving Certification
It’s not uncommon for an auditor to find a nonconformity, which is simply an area where you aren't fully meeting a requirement. Don't panic; this is a totally normal part of the process.
There are two main types of findings:
- Major Nonconformity: A significant failure in the ISMS that could put information security at risk. This has to be fixed before you can get certified.
- Minor Nonconformity: A smaller lapse or a one-off incident. You'll need to submit a plan to correct it, but it usually doesn't hold up your certification.
Once you've successfully addressed any issues and the auditor is satisfied, they will recommend your organization for certification. Your certificate is typically valid for three years, marking a huge milestone in your security journey.
Surveillance Audits: Maintaining Your Certification
Getting certified isn't a one-and-done deal. To keep your certificate valid, you have to go through annual surveillance audits. These are smaller, scaled-down versions of the Stage 2 audit that check if you're maintaining and continually improving your ISMS.
These regular check-ins ensure that security stays top-of-mind and that your ISMS grows with your business. The whole audit cycle reinforces the core principle of ISO 27001: continuous improvement. For a deeper dive into the end-to-end process, our guide on how to get ISO 27001 certified provides a detailed roadmap.
Sorting Out the Usual ISO 27001 Implementation Headaches
Diving into ISO 27001 certification is a major move, and let's be real—even the most buttoned-up organizations hit a few speed bumps. Knowing what these are ahead of time is half the battle, and it's what keeps your project from going off the rails.
<iframe width="100%" style="aspect-ratio: 16 / 9;" src="https://www.youtube.com/embed/ssHR24Nv6d0" frameborder="0" allow="autoplay; encrypted-media" allowfullscreen></iframe>
The journey is more than just tech; it's a mix of people, processes, and a bit of company politics. From getting the green light from the C-suite to figuring out a practical scope for your Information Security Management System (ISMS), every stage has its own unique puzzles. Let's walk through the most common snags and the tried-and-true ways to get past them.
Getting Leadership on Board
One of the first, and biggest, hurdles is convincing leadership to actually invest the time and money. Executives can sometimes see compliance as just another cost center—an IT problem that just eats up the budget without bringing anything back. That kind of thinking can stop an ISO 27001 project dead in its tracks.
The trick is to change the conversation. Ditch the technical jargon and translate the ISO 27001 certification requirements into real-world business wins.
- Crack Open New Markets: Point out that certification is often a non-starter for big enterprise clients and government contracts. It’s the key that unlocks new revenue.
- Get a Leg Up on the Competition: Frame ISO 27001 as a massive trust signal. It shows customers you’re serious about security and makes you stand out from the crowd.
- Dodge Financial Bullets: Talk about how a solid ISMS prevents expensive data breaches—the kind that lead to hefty fines, lawsuits, and a PR nightmare.
When you pitch ISO 27001 as a strategic move that drives growth and protects the bottom line, the whole dynamic shifts. You’re no longer talking about costs; you’re talking about opportunity. That’s how you get the enthusiastic backing you need from the top.
Nailing Down a Realistic ISMS Scope
Another classic mistake is messing up the scope of the ISMS. Teams tend to go one of two ways: they either make it too narrow, leaving huge chunks of the business exposed, or they go way too broad, creating a monster project that’s impossible to manage and quickly loses steam.
The goal is to find that sweet spot. Start by mapping out your most vital information assets and the business processes that rely on them. Your initial scope should zero in on the "crown jewels"—the data and systems that are absolutely critical to your operations and would cause the most damage if compromised.
This focused approach lets you get your core services certified without boiling the ocean. You can always widen the scope later, pulling in other departments or products as your security program gets more mature. It makes the first step manageable and gets you a win on the board much faster.
Doing a Risk Assessment That Actually Matters
Finally, a lot of companies stumble through the risk assessment. They either treat it like a checkbox exercise to get it over with or fall into "analysis paralysis," trying to account for every wild possibility. A half-baked risk assessment means you end up with the wrong controls, wasted money, and the real threats still lurking.
For a risk assessment to be worth anything, you have to tie threats directly to your business. Don't just list generic stuff like "malware." Get specific: "Risk of ransomware hitting our customer database, causing 48 hours of downtime and a potential data leak."
This approach forces you to think about the real-world impact on your business—on operations, finances, and your reputation. By prioritizing risks based on how likely they are and how much they'd hurt, you make sure your resources go toward stopping the threats that actually matter. That’s how you build an ISMS that's both effective and smart.
It's clear that the path to ISO 27001 has its share of tricky spots. The table below breaks down some of the most common hurdles you might face, along with some proactive ways to clear them before they turn into major roadblocks.
Common ISO 27001 Hurdles and How to Clear Them
| Challenge | Potential Impact | Proactive Solution |
|---|---|---|
| Lack of Employee Engagement | Controls fail because people aren't following procedures, creating security gaps despite technical measures. | Run regular, engaging security awareness training. Use real-world examples and celebrate security "champions" in different departments. |
| Poor Documentation | Auditors can't verify compliance, leading to non-conformities and a failed audit. It also makes onboarding new team members a nightmare. | Start documenting from day one. Use templates and a centralized system (like a wiki or compliance platform) to keep everything organized and accessible. |
| "Set It and Forget It" Mentality | The ISMS becomes outdated as new threats emerge and the business changes, leaving you vulnerable despite being "certified." | Schedule regular internal audits and management reviews (quarterly or semi-annually) to ensure the ISMS evolves with your business. |
| Vendor Risk Overload | A third-party vendor has a breach, which then impacts your data and your customers, making your own compliance efforts moot. | Implement a robust vendor management program. Assess the security posture of all critical vendors before signing contracts and review them annually. |
Thinking through these potential issues from the get-go doesn't just make the audit process smoother; it helps you build a security culture that lasts. By turning these challenges into opportunities for improvement, you end up with a much stronger and more resilient organization.
Answering Your Top ISO 27001 Questions
Let's cut through the noise and tackle the practical questions that pop up when you're staring down the barrel of an ISO 27001 certification. This is about giving you clear, straightforward answers to help you budget, plan, and set the right expectations for your journey through the ISO 27001 certification requirements.
How Long Does It Take To Get ISO 27001 Certified?
Honestly, it depends. The timeline for getting certified can swing pretty wildly based on your company's size, how complex your operations are, and how much security work you've already done.
A smaller company that’s already got some solid security habits might get it done in as little as six months. But for a larger enterprise with lots of moving parts and older systems, you could easily be looking at a 12 to 18-month project.
Want to speed things up? The two biggest factors are a dedicated project team and real, unwavering support from your leadership. When the top brass is committed, resources magically appear and roadblocks get cleared out of the way fast.
What Is The Difference Between ISO 27001 and SOC 2?
Great question. While both are all about security, they answer fundamentally different questions for your customers. Think of it this way: ISO 27001 is the blueprint for building a fortress, while SOC 2 is the guard's report on how well they patrolled the walls last night.
- ISO 27001: This is a certification. It proves you've designed and built a comprehensive Information Security Management System (ISMS). It’s all about having the right system in place to manage security risks over the long haul.
- SOC 2: This is an attestation report, not a certification. An auditor verifies that your security controls actually worked as intended over a specific period of time, usually 3 to 12 months.
So, ISO 27001 confirms you have the management system, and SOC 2 reports on how that system is performing day-to-day. It’s pretty common for companies to get both to satisfy different customer demands.
A key takeaway is that ISO 27001 focuses on the establishment of a risk management framework, while SOC 2 is focused on reporting on the effectiveness of controls related to specific service commitments.
Is Every Control In Annex A Mandatory To Implement?
Nope, and this is probably the biggest myth about the standard. Thinking you have to implement all 93 controls in Annex A is a surefire way to feel completely overwhelmed. It’s simply not true.
The best way to think of Annex A is as a big catalog of security controls you could implement. The standard just requires you to go through the list and check it against your own risk assessment. You only have to implement the controls that make sense for the specific risks your business faces.
The key is that you have to justify your decisions. You’ll document why you’re including or excluding each control in a crucial document called the Statement of Applicability (SoA). This tells an auditor you’ve been thoughtful and deliberate about building your security program.
How Much Does ISO 27001 Certification Cost?
The cost of certification really breaks down into three buckets. Getting your head around these will help you build a budget that doesn't have any nasty surprises.
- Implementation Costs: This is the internal stuff—your team's time, any consultants you hire, and new tools or software you might need to buy.
- Certification Audit Fees: This is what you pay the accredited third-party auditor to actually perform your Stage 1 and Stage 2 audits.
- Maintenance Costs: Certification isn't a one-and-done deal. You'll have yearly surveillance audits and ongoing costs to keep your ISMS running and improving.
For a small to mid-sized business, you can expect the total first-year cost to land anywhere from $20,000 to over $80,000. The final number really hinges on how much you can do internally versus hiring outside help and the overall complexity of your business.
Navigating the ISO 27001 certification requirements can be a complex and time-consuming process. Comp AI transforms this journey, using AI to get you audit-ready in days, not months. Our platform automates evidence collection, centralizes your compliance efforts, and provides expert guidance to ensure a 100% success rate. Cut the busywork and scale securely with Comp AI.
Share this article
Help others discover this content