If you're reading this, you probably got hit with one of these requests:
- A prospect sent you a security questionnaire asking if you're "NIST compliant"
- Your customer's procurement team wants proof you align with NIST CSF 2.0
- You're bidding on a government contract that requires NIST SP 800-171
- An enterprise buyer won't sign until you show NIST alignment
Here's the problem: "NIST compliance" isn't one thing. It's at least three different frameworks with different purposes, different control baselines, and different levels of rigor. This guide breaks down exactly which NIST publication applies to your situation, what you actually need to implement, and how to build evidence that'll satisfy technical reviewers.
You'll get:
→ A decision tree to figure out which NIST framework you need
→ Implementation roadmaps for CSF 2.0, 800-171, and 800-53
→ Ready-to-use evidence packs and documentation templates
→ Common pitfalls that cause failed assessments
If you're in a hurry and just need someone to handle this for you, Comp AI automates evidence collection and generates NIST documentation from your actual environment. We've helped hundreds of companies go from "no idea where to start" to "assessment-ready" in weeks instead of months. But if you want to understand what's actually involved, keep reading.

Which NIST Framework Do You Need? CSF vs 800-171 vs 800-53
Start here. Don't guess. The wrong framework wastes months of work.
```
┌─ Are you handling CUI (Controlled Unclassified Information)
│ or working with DoD/federal contracts?
│
├─ YES → Do you need FedRAMP authorization or are you
│ hosting systems for a federal agency?
│ │
│ ├─ YES → You need NIST SP 800-53
│ │ (Full federal control baseline, typically
│ │ 300+ controls depending on impact level)
│ │
│ └─ NO → You need NIST SP 800-171
│ (110 controls for protecting CUI in
│ contractor systems)
│
└─ NO → Are you responding to an enterprise security
review or RFP that mentions "NIST"?
│
├─ YES → You probably need NIST CSF 2.0
│ (Voluntary framework for demonstrating
│ security maturity and risk management)
│
└─ NO → Double-check the actual requirement.
Sometimes "NIST" is shorthand for
"structured security program" and CSF
is the safe default.
```
Still not sure? Look at the actual contract language or questionnaire. It should reference a specific publication number.
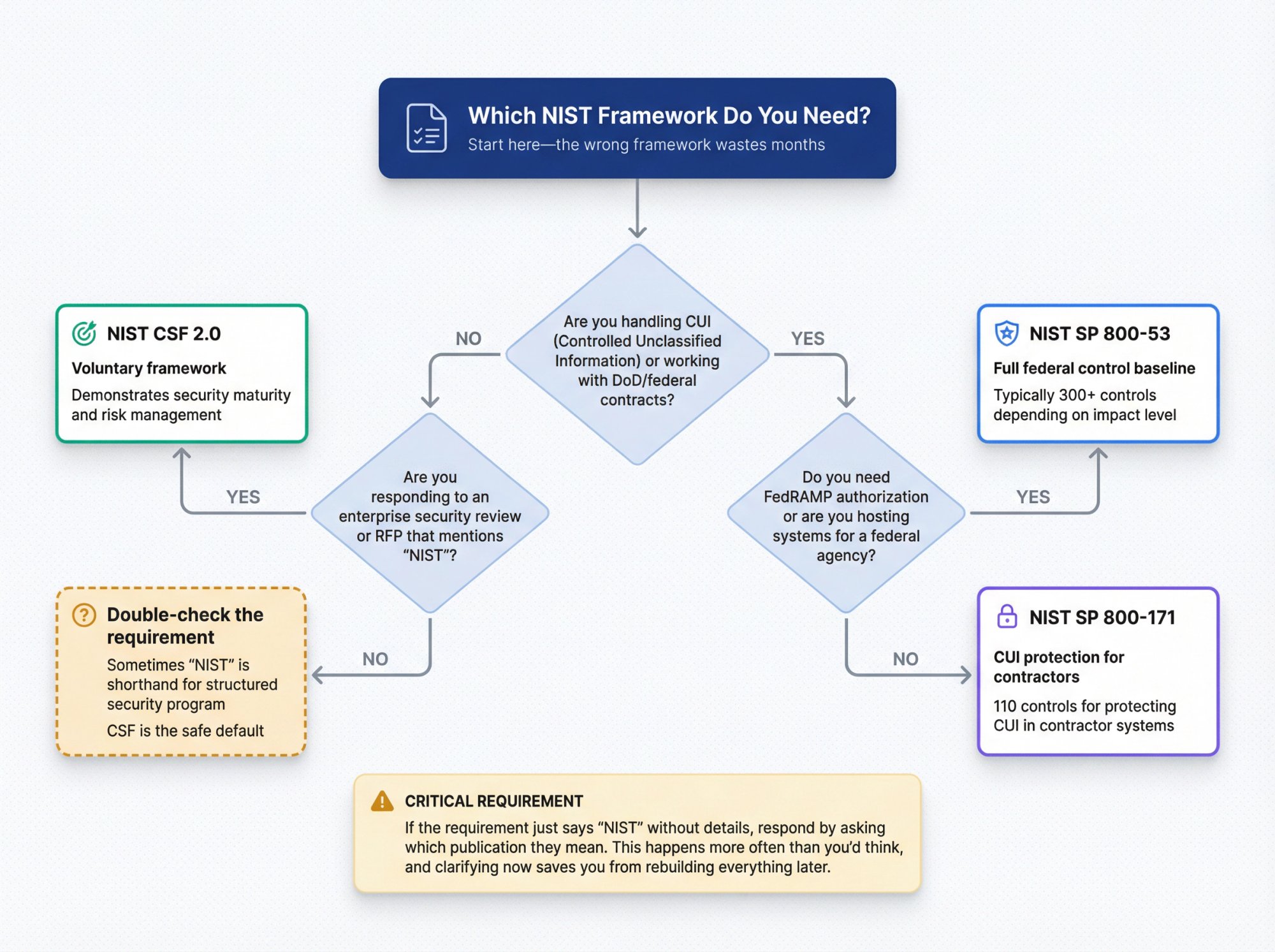
*CRITICAL REQUIREMENT:* If it just says "NIST" without details, respond by asking which publication they mean. This happens more often than you'd think, and clarifying now saves you from rebuilding everything later.
What Changed in NIST Compliance in 2024-2025?
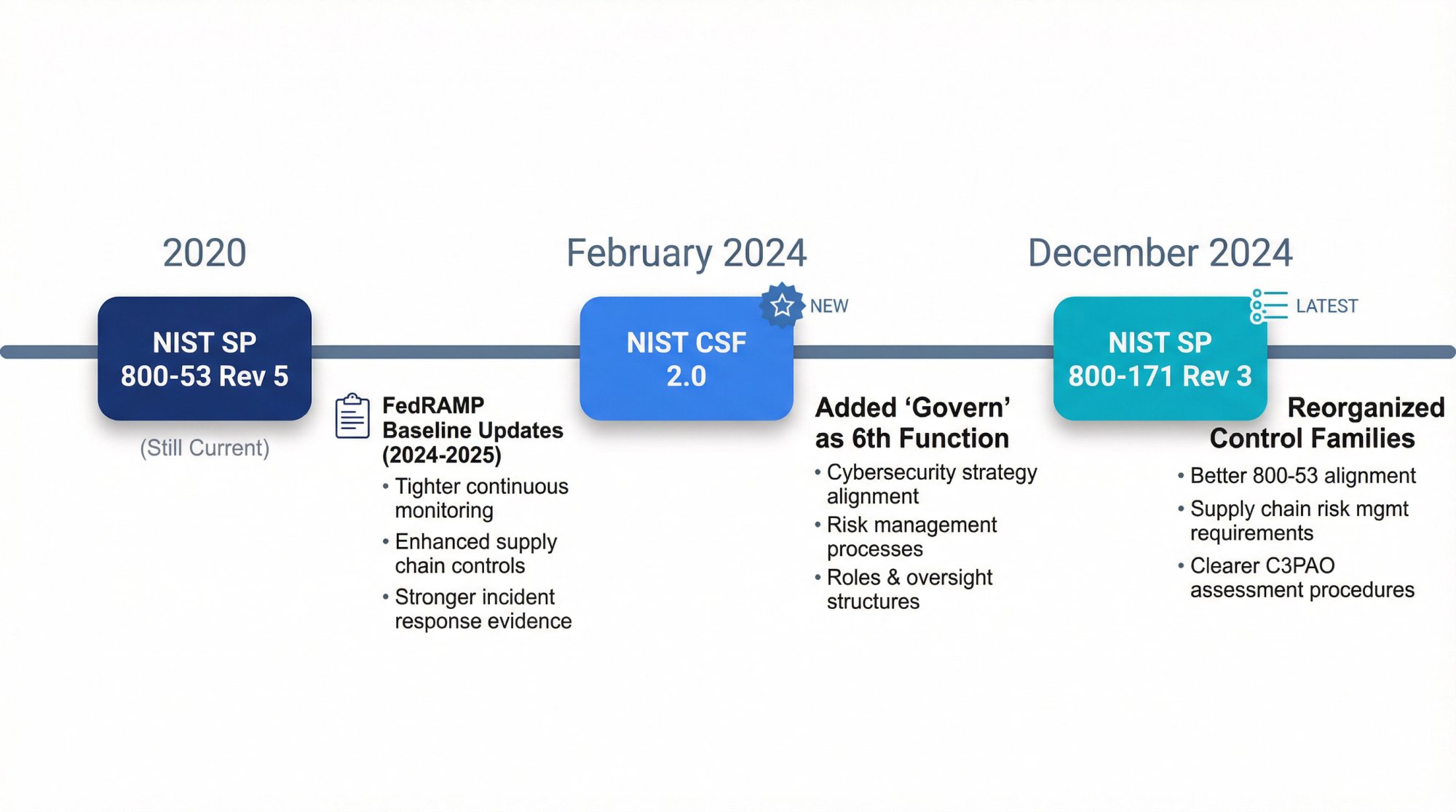
CSF 2.0 (February 2024)
The big shift: NIST added "Govern" as a sixth function. This isn't just bureaucratic overhead. It reflects what enterprise buyers already expect: someone needs to be accountable for cybersecurity strategy, not just execution.
The new Govern function covers:
- Cybersecurity strategy aligned with business objectives
- Risk management processes
- Roles and responsibilities
- Oversight structures
If you're using CSF for sales conversations, you need to show governance isn't an afterthought. Buyers want to know someone owns the security roadmap. Read the official CSF 2.0 release for full details.
800-171 Rev 3 (December 2024)
Revision 3 is here, and it changes how you'll structure your System Security Plan (SSP).
Key updates:
- Reorganized control families for better alignment with 800-53
- New requirements around supply chain risk management
- Clearer assessment procedures for C3PAOs
If you're currently working with Rev 2 documentation, check your contract. Some are already requiring Rev 3 alignment. The official 800-171 Rev 3 publication has the complete control baseline.
800-53 Rev 5 (2020, still current)
No major changes in 2024-2025, but FedRAMP updated its baseline to incorporate lessons learned from recent assessments.
If you're pursuing FedRAMP, the baseline is now tighter on:
- Continuous monitoring requirements
- Supply chain controls
- Incident response evidence
What is NIST CSF 2.0 and How Does It Work?
What is NIST CSF?
The Cybersecurity Framework is a voluntary framework designed to help organizations manage and communicate cybersecurity risk. It's organized around six functions: Govern, Identify, Protect, Detect, Respond, Recover. It's not a checklist of specific controls. It's a structure for showing how your security program works as a system.
Who needs NIST CSF?
You'll see CSF requirements in:
- Enterprise RFPs that want proof of security maturity
- Customer security reviews where they ask "how do you manage risk?"
- Sales conversations where you need to communicate your security posture clearly
- Internal planning when you want a structured approach to risk management
CSF is especially common when selling to large enterprises or critical infrastructure sectors (finance, healthcare, energy, telecom).
How to Implement NIST CSF 2.0 in 6 Weeks
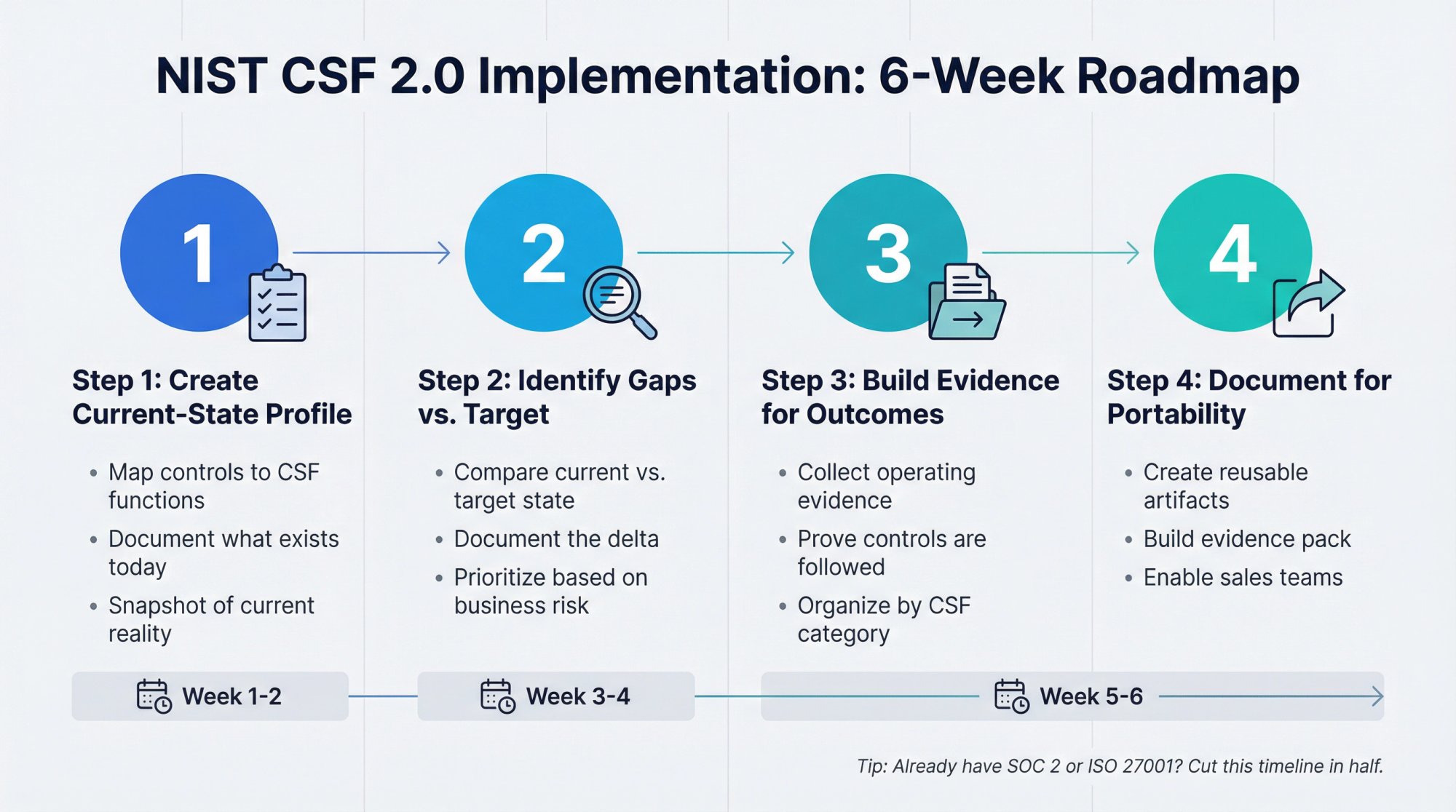
Step 1: Create a current-state profile
A CSF profile maps your actual controls to the framework's functions and categories. You're documenting what you do today: access controls, logging, incident response, vendor management, patching, encryption. This isn't aspirational. It's a snapshot of reality.
Tools you can use:
→ Spreadsheet mapping your controls to CSF categories
→ Comp AI's automated CSF profile generator (pulls from your actual environment)
→ Manual documentation (time-consuming but free)
Step 2: Identify gaps against your target profile
Your target profile represents where you need to be based on your risk appetite and business requirements. Compare current state vs. target state. Document the delta. This becomes your roadmap.
Start with the controls that protect your most critical assets. Don't try to close every gap at once. Prioritize based on actual business risk, not theoretical completeness.
Step 3: Build evidence for major outcomes
For each CSF category where you claim maturity, you need operating evidence:
- Govern: Risk register, governance meeting minutes, policy ownership documentation
- Identify: Asset inventory, data classification, risk assessment reports
- Protect: Access review logs, training completion records, MFA enforcement screenshots
- Detect: SIEM alerts, vulnerability scan reports, monitoring dashboards
- Respond: Incident response runbooks, tabletop exercise documentation, communication templates
- Recover: Backup verification logs, disaster recovery test results
The mistake teams make is writing policies without proving they're being followed. Buyers care about operating evidence.
Step 4: Document your implementation in a way that travels
You need artifacts you can attach to RFP responses:
- CSF profile (spreadsheet or PDF)
- Evidence pack (organized by category)
- Narrative explaining your approach to risk management
This becomes your reusable sales enablement collateral for security reviews. At Comp AI, we generate this documentation automatically from your connected systems, so you're not maintaining it manually every time a prospect asks.
CSF 2.0 Implementation Timeline
From scratch with basic security practices already in place (SSO, logging, policies):
- Week 1-2: Build current-state profile, identify gaps
- Week 3-4: Collect evidence, document controls
- Week 5-6: Create target-state profile, finalize documentation
If you already have SOC 2 or ISO 27001, you can reuse most of your evidence and cut this timeline in half.
Key resources for CSF
NIST 800-171: CUI Protection Requirements for Contractors
What is NIST 800-171?
NIST SP 800-171 defines 110 security requirements for protecting Controlled Unclassified Information (CUI) when it resides in non-federal systems. Translation: If you're a contractor working with federal agencies and you're handling CUI, you need to implement these controls.
CUI is sensitive but unclassified information like:
- Technical data covered by export control regulations
- Personally identifiable information (PII) from federal sources
- Procurement-sensitive information
- Law enforcement information
If you're not sure if your data qualifies as CUI, check the CUI Registry.
Who Needs NIST 800-171 Compliance?
You need 800-171 if:
- You're a DoD contractor handling CUI
- Your contract includes the DFARS 252.204-7012 clause
- You're pursuing CMMC Level 2 or 3 certification
- You're a subcontractor in a supply chain that handles CUI
This is contractually required. You can't skip it.
The 110 NIST 800-171 Requirements: What You're Implementing
The 110 requirements are organized into 14 families. Here are the major control areas with realistic implementation notes:
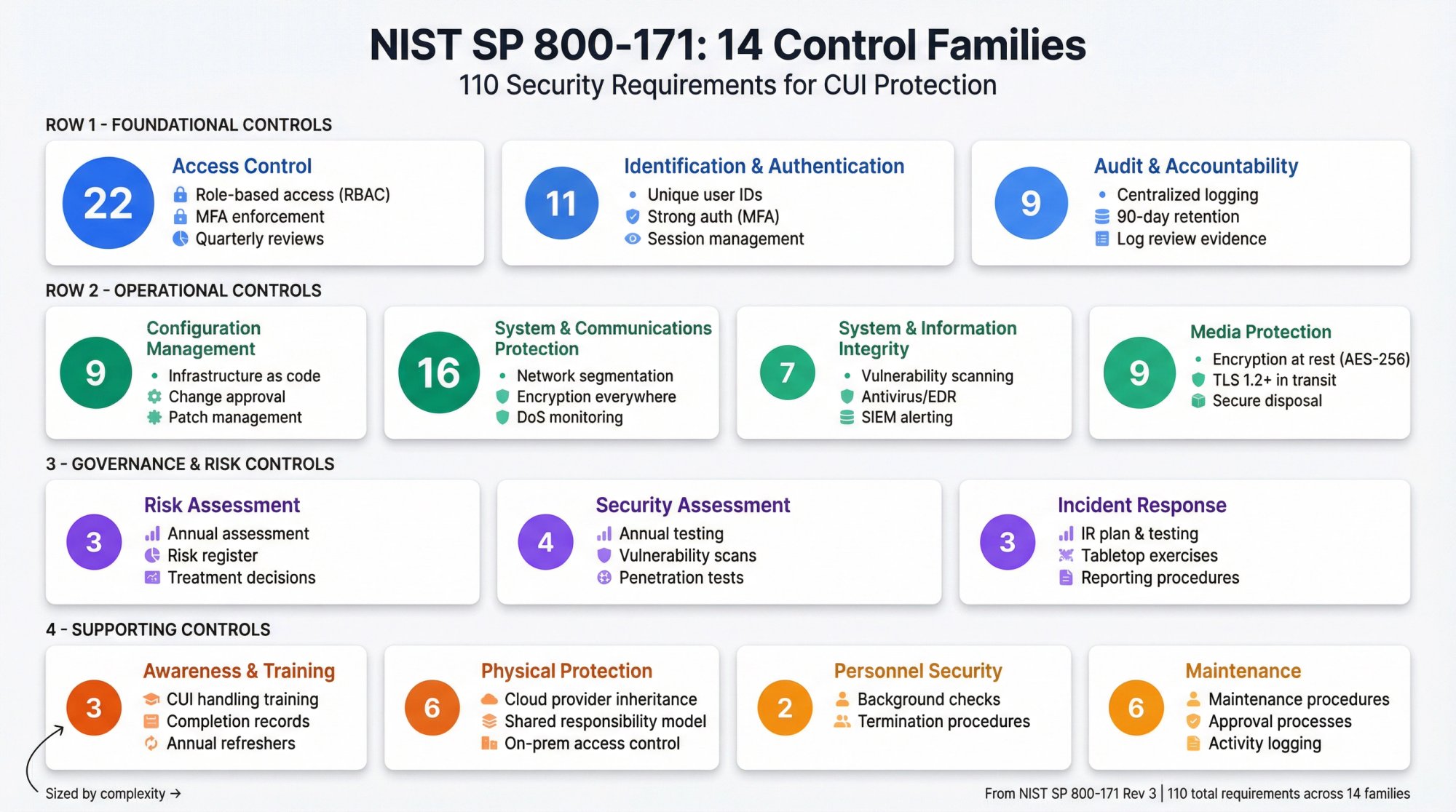
Access Control (22 requirements)
You need to prove that only authorized users can access CUI systems. This means role-based access control (RBAC) configured in your identity provider, MFA enforced for all CUI system access, quarterly access reviews with evidence of changes made, and separation of duties for critical functions. Most teams already have SSO and MFA. The hard part is documenting access decisions and maintaining review evidence over time.
Awareness and Training (3 requirements)
Users need security training that's specific to handling CUI. This isn't generic phishing training. You need to show training content covers CUI handling procedures, completion records for all users with CUI access, and annual refresher training.
Audit and Accountability (9 requirements)
You need to log activity on CUI systems and review those logs.
Implementation typically looks like:
→ Centralized logging (e.g., CloudWatch, Splunk, Datadog)
→ Log retention policy (NIST requires 90 days minimum, but most contracts want 1 year)
→ Evidence of log review (SIEM alerts, weekly review reports)
Configuration Management (9 requirements)
Baseline configurations for systems, change control, vulnerability remediation. This usually means infrastructure-as-code (Terraform, CloudFormation), change approval process with documented approvals, and patch management with evidence of critical patches applied within 30 days.
Identification and Authentication (11 requirements)
Proving who's accessing your systems.
Key requirements:
- Unique user IDs for all users (no shared accounts)
- Strong authentication mechanisms (MFA)
- Session management (timeouts, re-authentication for sensitive operations)
Incident Response (3 requirements)
You need a documented process for detecting and responding to security incidents involving CUI.
This means:
- Incident response plan that covers CUI scenarios
- Evidence that the plan is tested (tabletop exercises)
- Reporting procedures aligned with contract requirements
Maintenance (6 requirements)
Controlling who can perform maintenance on CUI systems. This usually involves documented maintenance procedures, approval processes for maintenance access, and logging of maintenance activities.
Media Protection (9 requirements)
Protecting CUI at rest and during transport.
Key controls:
- Encryption for CUI at rest (AES-256 typically)
- Encryption for CUI in transit (TLS 1.2+)
- Secure media disposal procedures
Personnel Security (2 requirements)
Screening people with CUI access. Typically background checks for CUI-privileged users and termination procedures that revoke access immediately.
Physical Protection (6 requirements)
Controlling physical access to CUI systems.
For cloud-based systems, this usually means:
→ Inheriting controls from your cloud provider (AWS, GCP, Azure)
→ Documenting your shared responsibility model
→ Controlling physical access to any on-prem systems handling CUI
Risk Assessment (3 requirements)
Regular risk assessments that identify threats to CUI. This means annual risk assessment, risk register documenting threats, likelihood, impact, and risk treatment decisions with approvals.
Security Assessment (4 requirements)
Regular testing of security controls. Typically annual security assessment (can be internal or third-party), vulnerability scanning (weekly or monthly depending on contract), and penetration testing (annual minimum).
System and Communications Protection (16 requirements)
Boundary protection, encryption, denial-of-service protection.
Key implementations:
- Network segmentation (VPCs, security groups)
- Encryption everywhere CUI moves or sits
- Monitoring for denial-of-service conditions
System and Information Integrity (7 requirements)
Vulnerability remediation, malware protection, monitoring. This means antivirus/EDR deployed on endpoints, vulnerability scanning with evidence of remediation, and information system monitoring (SIEM, alerting).
How to Implement NIST 800-171 in 12 Weeks
Step 1: Define your system boundary (scope)
*BIGGEST MISTAKE*Teams accidentally scope too broadly. You only need to implement 800-171 for systems that process, store, or transmit CUI.
If you can isolate CUI to a specific environment (e.g., a dedicated AWS account or GCP project), you dramatically reduce implementation scope. Create a one-page scope statement that defines exactly what's in and out of scope. Get it reviewed by someone who understands the requirement before you start implementing controls.
Step 2: Map your current state to the 110 controls
For each of the 110 requirements, document:
- What you have implemented today
- What evidence exists
- What gaps remain
If you already have SOC 2, ISO 27001, or HIPAA, you'll find significant overlap. Don't start from scratch. At Comp AI, we do this mapping automatically, so you can see exactly which controls you already satisfy and which ones need work.
Step 3: Implement missing controls
For each gap, you need to:
- Implement the technical control (MFA, logging, encryption, etc.)
- Document the implementation (policies, procedures, architecture diagrams)
- Collect evidence (screenshots, config exports, logs)
Focus on the controls that protect CUI directly: access control, encryption, monitoring, incident response.
Step 4: Create your System Security Plan (SSP)
The SSP is your master documentation artifact. It describes your system architecture, the boundary of your CUI environment, how each of the 110 controls is implemented, and where evidence is maintained. This document travels with assessments and contract reviews.
Template: NIST SP 800-171 SSP Template
At Comp AI, we generate SSPs from your actual environment rather than making you fill out blank templates. The platform knows what controls you've implemented because it's connected to your systems.
Step 5: Develop your Plan of Action & Milestones (POA&M)
If you have gaps that can't be closed immediately, you document them in a POA&M with:
- Description of the gap
- Risk level
- Remediation plan
- Target completion date
- Status updates
⚠️ CRITICAL COMPLIANCE REQUIREMENT: POA&Ms are normal. Assessors expect them. The key is showing you have a plan and you're making progress. Never let a POA&M go stale without updates.
Step 6: Prepare for assessment (if required)
Some contracts require third-party assessment (e.g., CMMC Level 2 requires a C3PAO assessment). Others accept self-attestation. Check your contract language to understand assessment requirements. If you need a third-party assessment, budget 2-4 weeks for the assessment process itself, plus prep time.
800-171 Implementation Timeline
From scratch with no existing compliance program:
- Weeks 1-2: Define scope, map current state
- Weeks 3-8: Implement missing controls
- Weeks 9-10: Create SSP and POA&M
- Weeks 11-12: Internal validation and prep for assessment
If you already have SOC 2 or ISO 27001, you can cut this timeline in half by reusing evidence. With Comp AI, companies typically reduce this to 3-4 weeks because evidence collection and SSP generation are automated.
Key resources for 800-171
- Official NIST SP 800-171 Rev 3 Publication
- DoD Assessment Methodology
- CUI Registry
- Comp AI's 800-171 SSP Generator
NIST 800-53: FedRAMP and Federal Control Requirements
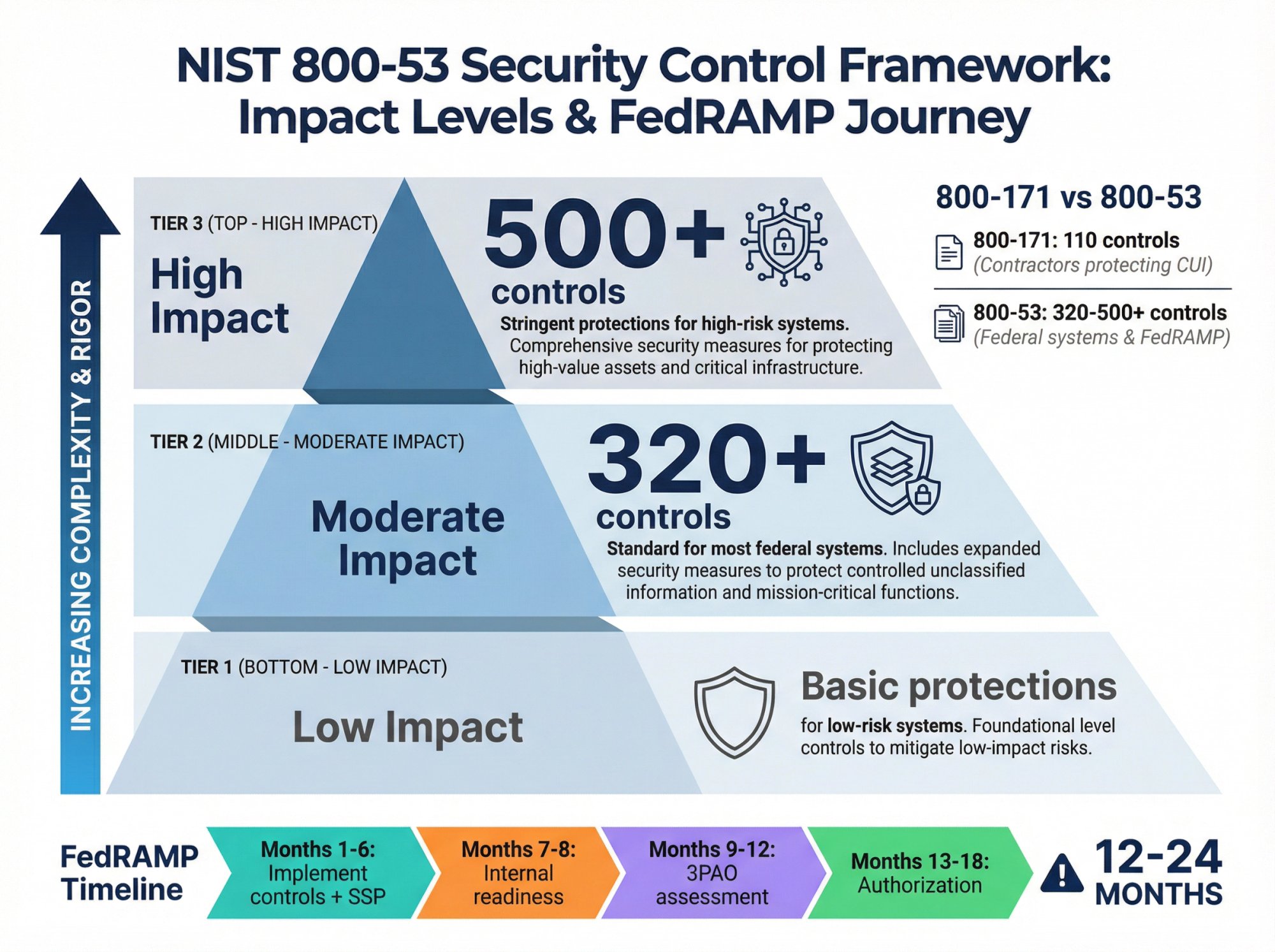
What is NIST 800-53?
NIST SP 800-53 is the comprehensive security and privacy control catalog used by federal agencies.

It defines controls across three impact levels:
- Low: Basic protections for low-risk systems
- Moderate: Standard controls for most federal systems (typically 320+ controls)
- High: Stringent controls for high-risk systems (500+ controls)
If you're pursuing FedRAMP authorization or hosting systems for a federal agency, you're working with 800-53.
Who Needs NIST 800-53 Compliance?
You need 800-53 if:
- You're pursuing FedRAMP authorization
- You're a cloud service provider working with federal agencies
- Your contract explicitly requires 800-53 compliance
- You're hosting systems that federal agencies will use
This is a major undertaking. Budget 12-24 months for full FedRAMP authorization.
NIST 800-53 vs 800-171: Key Differences Explained
800-171 is designed for contractors protecting CUI in non-federal systems (110 controls).
800-53 is designed for federal systems themselves or cloud services that federal agencies will use (300-500+ controls depending on impact level).
If you're a contractor handling CUI but not hosting federal systems, you need 800-171, not 800-53. If you're building a cloud platform that federal agencies will use, you need 800-53 through FedRAMP.
How to Implement NIST 800-53 for FedRAMP
The process is similar to 800-171, but the scope and rigor are much higher.
Step 1: Determine your impact level
Work with your federal sponsor or agency to determine the appropriate impact level (Low, Moderate, High). Most SaaS platforms pursuing FedRAMP start at Moderate.
Step 2: Implement the control baseline
For FedRAMP Moderate, you'll implement 320+ controls across families like:
- Access Control
- Audit and Accountability
- Security Assessment and Authorization
- Configuration Management
- Contingency Planning
- Identification and Authentication
- Incident Response
- Maintenance
- Media Protection
- Physical and Environmental Protection
- Planning
- Personnel Security
- Risk Assessment
- System and Services Acquisition
- System and Communications Protection
- System and Information Integrity
Each control has specific implementation requirements and assessment procedures.
Step 3: Create your System Security Plan (SSP)
The FedRAMP SSP is comprehensive. It documents your entire security implementation.
Template: FedRAMP SSP Template
At Comp AI, we generate FedRAMP SSPs from your environment automatically, but this is still a heavy lift. FedRAMP SSPs are typically 200-400 pages.
Step 4: Continuous monitoring
800-53 requires continuous monitoring of your security posture.
This means:
- Monthly vulnerability scanning
- Annual penetration testing
- Continuous configuration monitoring
- Regular security control assessments
Comp AI handles continuous monitoring automatically, alerting you to drift before it becomes an assessment finding.
Step 5: Third-party assessment
FedRAMP requires assessment by an accredited Third-Party Assessment Organization (3PAO). The 3PAO validates your control implementation and produces a Security Assessment Report (SAR). This process typically takes 2-4 months.
Step 6: Authorization
After assessment, you need either:
- Agency Authorization: The federal agency you're working with authorizes your system
- JAB Provisional Authorization: The Joint Authorization Board grants provisional authorization that multiple agencies can leverage
800-53 Implementation Timeline
Realistic timeline for FedRAMP Moderate authorization:
- Months 1-6: Implement control baseline, create SSP
- Months 7-8: Internal readiness assessment
- Months 9-12: 3PAO assessment
- Months 13-18: Remediation and authorization process
This is not something you can rush. FedRAMP is a long-term commitment.
Key resources for 800-53
- Official NIST SP 800-53 Rev 5 Publication
- FedRAMP Official Resources
- FedRAMP Marketplace
- Comp AI's FedRAMP Acceleration Platform
NIST Compliance Evidence: What You Need to Prove It
Regardless of which NIST framework you're implementing, you need evidence. Here's what that actually looks like in practice.
The control tracker (your single source of truth)
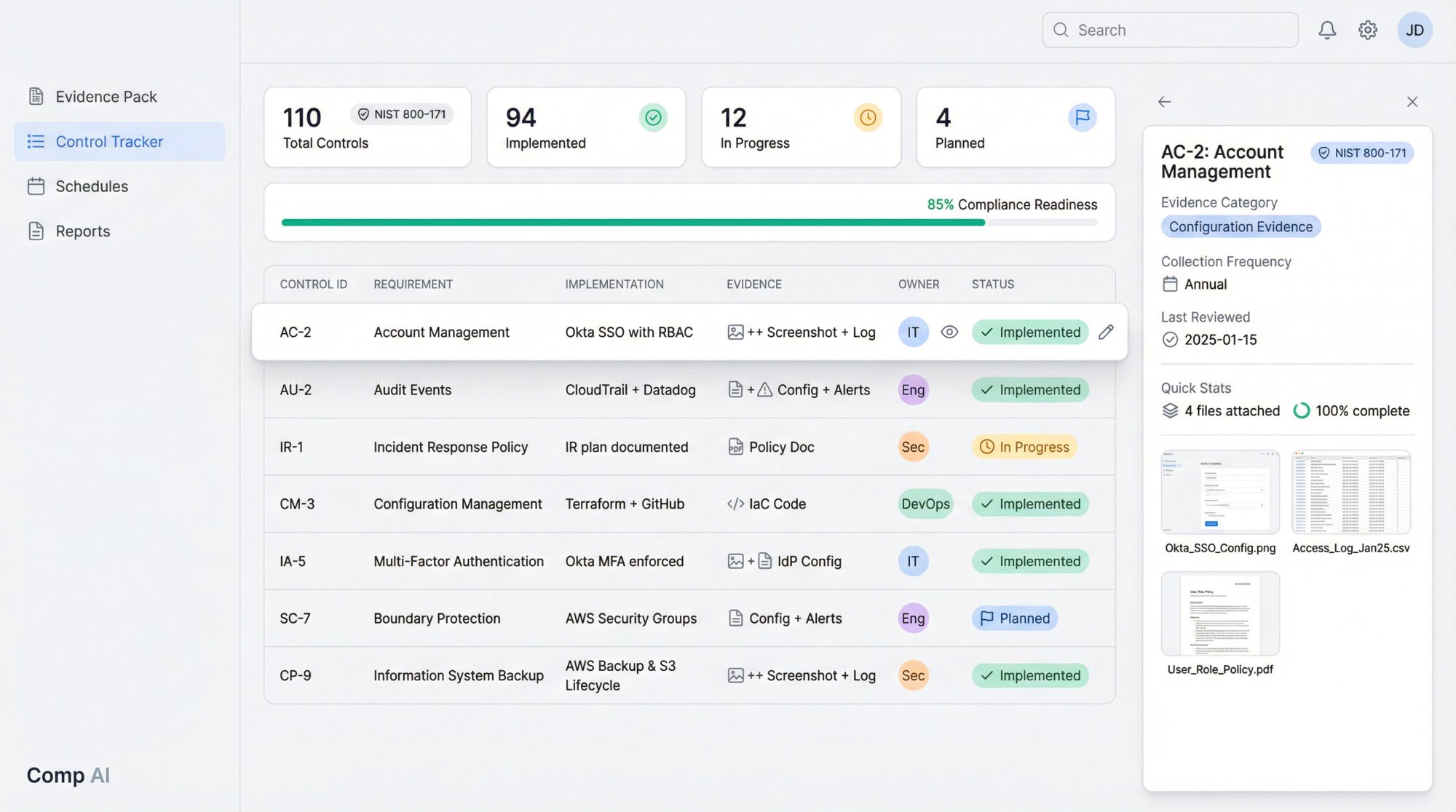
Create one spreadsheet (or use a compliance platform like Comp AI) that maps:
| Control ID | Requirement | Implementation | Evidence | Owner | Status |
|---|---|---|---|---|---|
| AC-2 | Account Management | Okta SSO with RBAC | Okta config screenshot + access review log | IT Director | Implemented |
| AU-2 | Audit Events | CloudTrail + Datadog | Logging config + sample alerts | Engineering Lead | Implemented |
| IR-1 | Incident Response Policy | IR plan documented | Policy doc + tabletop minutes | Security Lead | Implemented |
This becomes your assessment checklist. For CSF, you'll map to functions and categories instead of specific control IDs, but the structure is the same.
Evidence categories you'll need
Configuration evidence
Screenshots or config exports showing controls are actually enabled:
- MFA enforcement in your identity provider
- Encryption settings on databases and storage
- Network security group rules
- SIEM configuration
Operating evidence
Logs and records showing controls are being followed:
- Access review logs (who reviewed, what changed)
- Vulnerability scan reports with remediation evidence
- Training completion records
- Incident response tickets
Documentation evidence
Policies and procedures that define how things work:
- Information security policy
- Incident response plan
- Change management procedures
- Acceptable use policy
Governance evidence
Meeting minutes and decisions showing someone's accountable:
- Risk review meetings
- Security roadmap reviews
- Exception approvals
- Vendor risk assessments
How to organize your evidence
Create a folder structure like this:
```
NIST Evidence Pack/
├── Governance/
│ ├── Risk register
│ ├── Governance meeting minutes
│ └── Policy ownership documentation
├── Access Control/
│ ├── MFA config screenshots
│ ├── Access review logs
│ └── RBAC documentation
├── Monitoring/
│ ├── SIEM configuration
│ ├── Alert samples
│ └── Log retention policy
├── Incident Response/
│ ├── IR plan
│ ├── Tabletop exercise docs
│ └── Past incident tickets
└── Assessment/
├── Vulnerability scans
├── Penetration test reports
└── Security assessment results
```
At Comp AI, we collect and organize this evidence automatically by connecting to your systems (AWS, GCP, Azure, Okta, GitHub, and 100+ other integrations).
Evidence collection schedule
Don't wait until assessment time to gather evidence. You'll scramble and miss things. Instead, create a collection schedule:
| Evidence Type | Collection Frequency | Owner | Due Date |
|---|---|---|---|
| Access review logs | Quarterly | IT Director | 1st of Jan/Apr/Jul/Oct |
| Vulnerability scans | Monthly | Security Lead | 1st of each month |
| Training completion records | Quarterly | HR / Security | 1st of Jan/Apr/Jul/Oct |
| SIEM alert samples | Monthly | Engineering Lead | 1st of each month |
| Risk register updates | Quarterly | Security Lead | 15th of Mar/Jun/Sep/Dec |
This schedule ensures you're always audit-ready.
The copy-paste evidence template
Here's a template you can adapt for any control. Copy this into your control tracker:
Control ID: \[e.g., AC-2, CSF PR.AC-1\]
Requirement: \[What the control requires in plain English\]
Implementation: \[What you actually did to satisfy this requirement\]
Evidence location: \[Where the proof is stored\]
Evidence type: \[Configuration / Operating / Documentation / Governance\]
Collection frequency: \[How often this evidence needs to be refreshed\]
Owner: \[Who's responsible for maintaining this control\]
Status: \[Implemented / In Progress / Planned\]
Last reviewed: \[Date\]
Notes: \[Any context that'll help during assessment\]
Example for MFA:
Control ID: AC-2 (Account Management) / CSF PR.AC-1
Requirement: Enforce multi-factor authentication for all users accessing CUI systems
Implementation: MFA enforced in Okta for all applications. Users cannot disable MFA. New user onboarding requires MFA setup before first login.
Evidence location: /evidence/access-control/mfa-config-screenshot.png + /evidence/access-control/okta-mfa-policy.pdf
Evidence type: Configuration
Collection frequency: Annual (or when policy changes)
Owner: IT Director
Status: Implemented
Last reviewed: 2025-01-15
Notes: MFA policy applies to all users. Exceptions require written approval from CISO (none granted to date).
This is the single most valuable file you'll create. Use it for CSF alignment, 800-171, and 800-53 work.
| Control / outcome | Requirement intent | Implementation | Evidence link | Owner | Status |
|---|---|---|---|---|---|
| MFA enforced | Prevent account takeover | Enforced in IdP + critical systems | Screenshot + policy | IT | Implemented |
| Central logging | Detect suspicious activity | Cloud + app logs centralized | Logging config + alert samples | Eng | Implemented |
| IR plan practiced | Respond effectively | Annual tabletop exercise | Tabletop minutes | Security | Planned |
5 Compliance Pitfalls That Cause NIST Assessment Failures
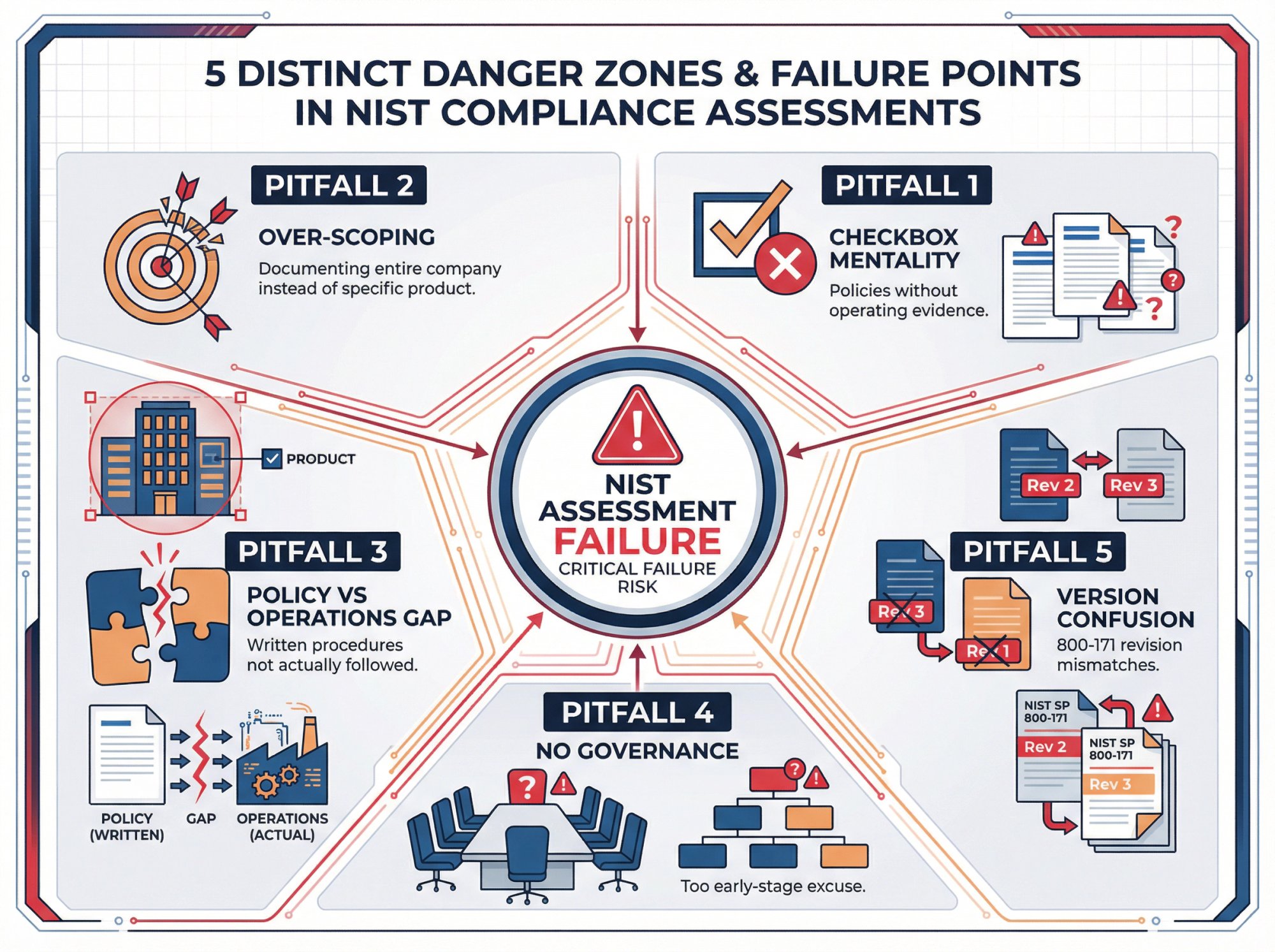
Pitfall 1: Treating "NIST compliance" as a checkbox
Customers care about outcomes: access control, monitoring, response capability, governance. If you can't show evidence that these things actually work, the checkbox doesn't help you win deals.
COMPLIANCE REALITY: Policies are necessary. They aren't sufficient. Having a 50-page Information Security Policy doesn't prove you're doing anything. You need operating evidence: tickets, logs, review records, approvals.
Fix: Build the evidence pack as you implement controls, not after.
Pitfall 2: Over-scoping
Teams accidentally scope "the whole company" when the actual request is about a specific product or environment. You end up documenting desktop IT infrastructure that has nothing to do with your SaaS product.
Fix: Write a one-page scope statement first. Get it reviewed by someone who understands the requirement.
Pitfall 3: Confusing policies with operations
Policies are necessary. They aren't sufficient. Having a 50-page Information Security Policy doesn't prove you're doing anything. You need operating evidence: tickets, logs, review records, approvals.
Fix: Pair every policy with operating evidence that shows it's actually being followed.
Pitfall 4: Ignoring governance because you're "too early-stage"
CSF 2.0 explicitly added "Govern" for a reason: customers want to know someone is accountable. If you tell a prospect "we don't really have formal governance yet" in a security review, you just made their risk team nervous.
Fix: Make governance lightweight but real. You don't need a board committee. You need an owner, a cadence, a risk register, and a process for exceptions.
Pitfall 5: Version confusion (especially around 800-171)
Revision changes and evolving DoD guidance mean you must track which revision applies to your specific contract or customer requirement. Using Rev 2 documentation when your contract references Rev 3 will cause problems during assessment.
Fix: Treat versioning as a contractual requirement. Document it clearly in your scope statement and SSP.
How Comp AI Automates NIST Compliance and Evidence Collection
If you're a startup or lean SaaS team, speed in compliance comes from three things:
- Reuse - Use SOC 2 or ISO 27001 work instead of starting from scratch
- Automation - Evidence collection and monitoring shouldn't be a full-time job
- Tight scope - One product boundary first, then expand
This is exactly why companies adopt compliance automation platforms. The hard part isn't knowing the controls. The hard part is collecting and maintaining proof continuously without burning out your team.
How we approach NIST at Comp AI
At Comp AI, we've built our platform around a simple philosophy: do the heavy lifting for you.
Here's what that means in practice for NIST compliance:
We handle evidence collection automatically
Our AI agents connect to your systems (AWS, GCP, Azure, GitHub, Okta, and 100+ other integrations) and automatically collect evidence for controls. Instead of manually logging into each system to take screenshots and export configs, our agents do it for you. They run continuously, so your evidence stays current for quarterly reviews or surprise assessments.
We generate documentation from your actual environment
When you need an SSP for 800-171 or a CSF profile for a questionnaire, Comp AI generates it from your actual environment rather than making you fill out blank templates. The platform knows what you've implemented (because it's connected to your stack), so it can produce documentation that matches reality. That means no more "the SSP says we do X but we actually do Y" disconnects that cause assessment failures.
We map across frameworks automatically
If you already have SOC 2, we don't make you start from zero for NIST. Comp AI maps controls across frameworks automatically. Your SOC 2 access review evidence? That satisfies NIST CSF "Protect" outcomes and 800-171 access control requirements. Your vulnerability scans? Those map to multiple controls across CSF, 800-171, and 800-53. You do the work once, and we make it count everywhere.
We keep you audit-ready continuously
NIST compliance isn't one-and-done. You need to maintain evidence over time, especially for 800-171 POA&Ms and continuous monitoring. Comp AI monitors your environment continuously and alerts you to gaps before they become assessment failures. If MFA gets disabled somewhere or a critical patch is overdue, you know immediately.
Real results from companies using Comp AI for NIST
Companies using Comp AI for NIST compliance typically see:
- 75-90% reduction in time spent on evidence collection and documentation
- Weeks instead of months to produce a complete SSP or CSF profile
- Zero failed assessments due to missing or inconsistent evidence
According to internal case studies, we've helped companies go from "we have no idea where to start with 800-171" to "we're assessment-ready" in under 30 days.
How to get started with Comp AI for NIST
If you're facing a NIST requirement and need to move fast:
- Book a demo - We'll show you exactly how we'd handle your specific NIST requirement
- Connect your stack - We integrate with your existing tools (typically takes 15-30 minutes)
- Let our AI agents collect evidence - We automatically gather and organize evidence while you focus on your product
We also offer hands-on support from our compliance team. If you get stuck on a specific control or need help responding to a customer's technical questions, we're available via Slack in real-time.
NIST Compliance FAQ: Common Questions Answered
Is NIST CSF 2.0 required?
Usually no, unless a contract explicitly requires it. But CSF 2.0 is increasingly used as a common language in enterprise security reviews. Even if it's not contractually required, aligning to CSF gives you a structured way to communicate your security maturity. The "Govern" emphasis in CSF 2.0 also reflects what buyers already expect to see in mature organizations.
We have SOC 2. Does that mean we're NIST compliant?
Not automatically, but SOC 2 gives you a large chunk of the operational foundation. The faster path is typically mapping your SOC 2 controls to NIST requirements and filling gaps rather than starting from scratch, as research from compliance practitioners shows significant overlap between frameworks.
For example:
- Your SOC 2 access review evidence maps to NIST CSF "Protect" and 800-171 access control requirements
- Your SOC 2 incident response controls map to CSF "Respond" and 800-171 IR requirements
- Your SOC 2 change management evidence maps to CSF and 800-171 configuration management
At Comp AI, we do this mapping automatically so you're not rebuilding evidence you already have.
What's the difference between NIST 800-171 and CMMC?
CMMC (Cybersecurity Maturity Model Certification) is a program and requirement structure used in DoD supply chains. NIST 800-171 is a core control baseline that CMMC incorporates at Levels 2 and 3.
Think of it this way: CMMC defines the overall maturity levels and assessment requirements. 800-171 defines the specific controls you need to implement.
What if a questionnaire just says "NIST" without specifics?
Respond by asking which publication they mean: CSF, 800-171, or 800-53.
If they can't clarify (which happens more often than you'd think), the safe move is to align to NIST CSF and provide:
- A CSF profile showing your current state
- Evidence pack for major outcomes
- Clear documentation of scope
This demonstrates structured security thinking without overcommitting to a specific control baseline you may not need.
What's the single best first deliverable to reduce risk quickly?
Three things, in this order:
- Scope statement (one page defining what's in and out of scope)
- Control tracker (mapping requirements to implementation and evidence)
- Evidence calendar (scheduled collection so you're never scrambling)
These three prevent 80% of downstream chaos in NIST implementations. They force you to be clear about what you're actually doing, and they create a system for maintaining proof over time.
How long does NIST compliance take?
It depends entirely on which "NIST" and your starting point.
NIST CSF alignment:
If you have basic security practices in place (SSO, MFA, logging, basic policies), you can produce a credible CSF profile and evidence pack in 2-4 weeks, according to NIST implementation guidance.
NIST SP 800-171:
From scratch with no existing compliance program, budget 8-12 weeks for initial implementation and SSP production (according to DoD assessment guidance). If you already have SOC 2 or ISO 27001, you can cut that in half by mapping and filling gaps.
NIST SP 800-53 / FedRAMP:
Budget 12-24 months for full FedRAMP authorization, as confirmed by FedRAMP's official documentation. This isn't something you can rush.
With Comp AI, companies typically reduce these timelines by 60-75% because evidence collection and documentation generation are automated.
Do we need a third-party assessment for NIST compliance?
It depends on the requirement.
For NIST CSF: Typically no. CSF is a voluntary framework. You self-assess and communicate your alignment.
For NIST SP 800-171: It depends on your contract. Some government contracts require a third-party assessment (C3PAO for CMMC, for example). Others accept self-attestation with evidence.
For NIST SP 800-53 / FedRAMP: Yes. FedRAMP requires a formal third-party assessment by an accredited 3PAO.
Always check your specific contract language to understand assessment requirements.
Can we implement NIST requirements in the cloud (AWS, GCP, Azure)?
Absolutely. In fact, cloud environments often make it easier because:
- Many controls are built-in (encryption, logging, IAM)
- Evidence collection can be automated via APIs
- Configuration-as-code makes baseline management cleaner
The key is making sure you:
→ Understand your shared responsibility model
→ Document your implementation clearly
→ Maintain evidence of configuration and monitoring
Comp AI integrates directly with AWS, GCP, and Azure to collect evidence automatically, so you don't have to manually export configs every quarter.
What if we're already using another compliance tool?
You have a few options:
Keep your existing tool for SOC 2 or ISO, add Comp AI for NIST
Many companies use Comp AI alongside existing tools because we specialize in evidence automation and multi-framework mapping.
Consolidate onto Comp AI
We support 25+ frameworks including SOC 2, ISO 27001, HIPAA, GDPR, and NIST. Most companies find it easier to manage everything in one platform once they see how much faster evidence collection is with our AI agents.
Talk to us about what makes sense for your situation. We're not here to force a migration if your current setup works. We're here to help you move faster and reduce manual work.
What's the difference between NIST compliance and SOC 2?
SOC 2 is a formal audit framework from the AICPA. You implement controls based on Trust Services Criteria, undergo a third-party audit, and receive a report you can share with customers.
NIST compliance (typically referring to CSF or 800-171) is about implementing specific control baselines or aligning to a framework. There's typically no formal "NIST audit" that produces a shareable report (NIST documentation confirms this), except in specific contexts like FedRAMP.
In practice:
- Enterprises often accept SOC 2 Type 2 reports as proof of security maturity
- Government and defense contracts often require NIST 800-171 documentation
- Some customers want both: SOC 2 for commercial credibility and NIST for government readiness
At Comp AI, we help you handle both simultaneously by reusing evidence across frameworks.
How much does NIST compliance cost?
If you're doing it manually:
Budget for staff time (security engineer, compliance lead, potentially consultants) plus any tools or infrastructure upgrades. Total cost can range from $50,000 to $200,000+ depending on complexity and starting point.
If you're using Comp AI:
We handle evidence collection, documentation generation, and ongoing monitoring for a fraction of that cost. Most companies save 60-80% compared to manual implementation or traditional consulting approaches.
Book a demo to get specific pricing for your situation.
Can Comp AI help us respond to security questionnaires?
Yes. Our AI-powered trust center includes questionnaire automation.
When a prospect sends you a security questionnaire (those lengthy spreadsheets with hundreds of questions), our AI can auto-fill answers based on your implemented controls and evidence. For NIST-specific questions like "Do you align to NIST CSF?" or "Are you implementing 800-171?", the platform pulls from your actual documentation and provides accurate, evidence-backed responses.
This typically reduces questionnaire response time from days to minutes.
What if we fail a NIST assessment?
First, understand that most "failures" in NIST contexts aren't binary pass/fail. They're usually:
- Gaps identified in a POA&M (Plan of Action & Milestones) that you need to remediate
- Requests for additional evidence that you didn't provide initially
- Implementation questions where the assessor wants clarification
The key to avoiding this is having complete, consistent evidence from the start.
At Comp AI, we help you build audit-ready evidence continuously. Our platform flags gaps before an assessment happens, and we provide hands-on support from our compliance team if you need help responding to assessor questions. We've maintained a 100% success rate across hundreds of compliance assessments because we ensure evidence is complete and accurate before you ever talk to an assessor.
Is NIST compliance a one-time thing or ongoing?
Ongoing.
Even if you're not subject to continuous monitoring requirements (like in 800-171 or FedRAMP), maintaining NIST alignment means:
- Keeping evidence current (access reviews, vulnerability scans, training records)
- Updating your risk register as your environment changes
- Maintaining policies and procedures
- Responding to new questionnaires with up-to-date information
The companies that struggle with compliance are the ones that treat it as a one-time project. The companies that succeed build it into their regular operations. Comp AI makes ongoing compliance manageable by automating evidence collection and monitoring. Instead of scrambling every quarter to gather proof, you have it ready continuously.
Ready to get NIST compliant without the chaos?
If you're facing a NIST requirement and need to move fast, Comp AI can help.
We'll handle evidence collection, generate documentation from your actual environment, and keep you audit-ready continuously so you can focus on building your product instead of filling spreadsheets.
Book a demo to see exactly how we'd handle your specific NIST requirement.
Or if you have questions, our team is available via Slack in real-time. We're not here to sell you things you don't need. We're here to help you win deals and pass assessments without burning out your team.
Share this article
Help others discover this content