When enterprise customers ask to see your SOC 2 report, they're really asking one question: "Can we trust you with our data?" Penetration testing sits at the heart of that answer.
Here's what most guides won't tell you: SOC 2 doesn't technically mandate penetration testing. But if you're serious about security (and about closing deals), you'll want to understand exactly how pen testing fits into your compliance strategy.
Does SOC 2 Require Penetration Testing?
Let's cut straight to it: No, SOC 2 doesn't explicitly require penetration testing. The AICPA's Trust Services Criteria don't spell out "thou shalt conduct pen tests."
But here's where it gets interesting. SOC 2 does require you to demonstrate that you've identified and addressed risks to your systems. And penetration testing is a reliable and cost-effective way to satisfy multiple SOC 2 requirements, especially those related to risk assessment, vulnerability management, and ongoing monitoring.
Think of it this way: You could technically pass a SOC 2 audit without pen testing. But your auditor will want to see how you're validating your security controls. Pen testing gives you concrete evidence that your defenses actually work.
How Does Penetration Testing Support SOC 2 Compliance?
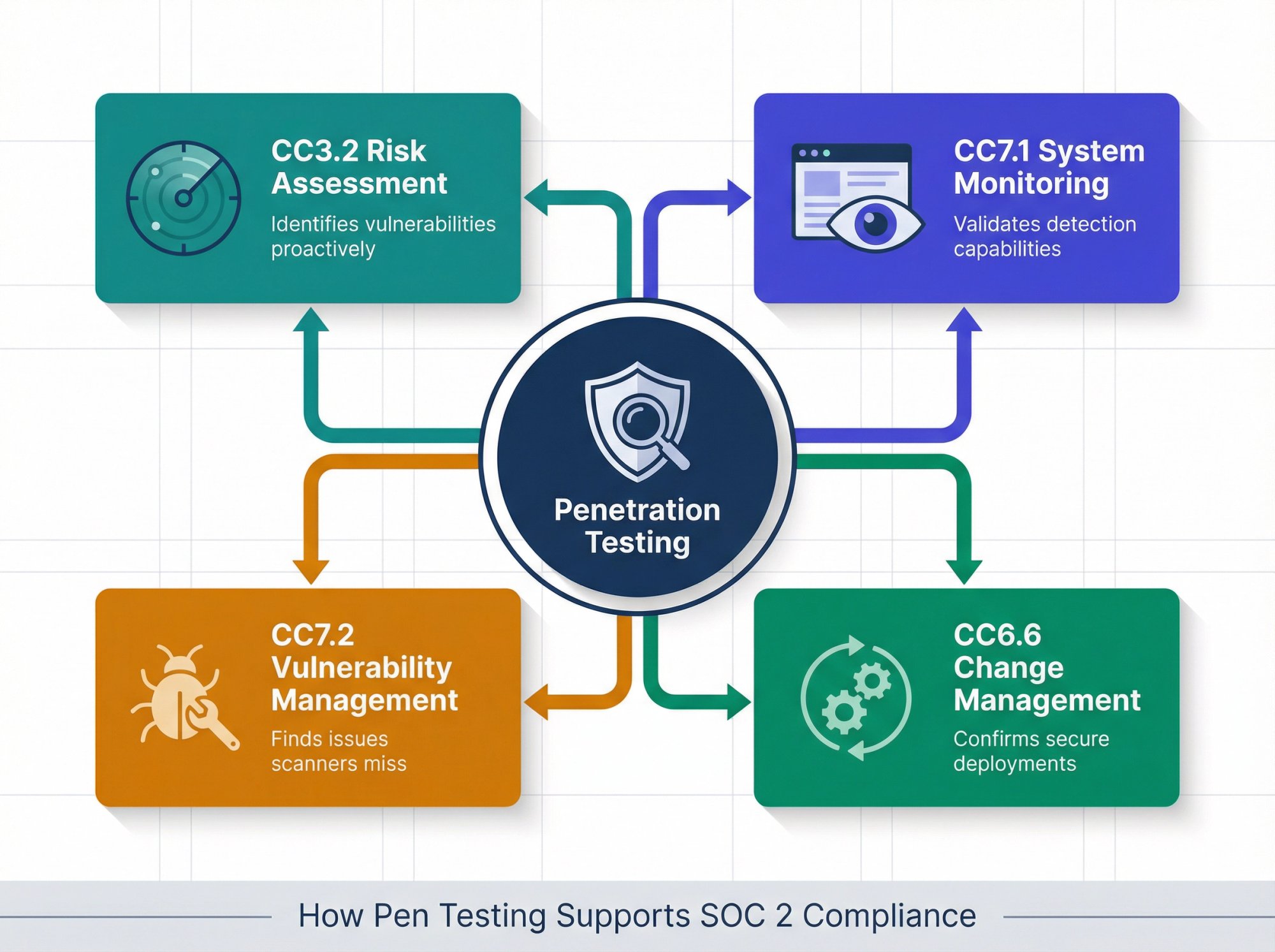
Penetration testing directly supports several Trust Services Criteria. Here's how it maps:
| Trust Service Criteria | How Pen Testing Helps | What Auditors Look For |
|---|---|---|
| Risk Assessment (CC3.2) | Simulates real attacks to identify vulnerabilities | Evidence of proactive security testing |
| System Monitoring (CC7.1) | Validates that monitoring tools catch threats | Periodic validation of detection capabilities |
| Vulnerability Management (CC7.2) | Finds issues automated scanners miss | Remediation timelines and thoroughness |
| Change Management (CC6.6) | Confirms changes didn't introduce weaknesses | Post-change security validation |
How Pen Testing Satisfies Risk Assessment (CC3.2)
SOC 2 requires you to identify and analyze risks that could affect your ability to achieve your security objectives. A penetration test does exactly that. It simulates real-world attacks to find vulnerabilities before bad actors do.
Your auditor wants to see that you've done more than just check boxes. They want evidence that you've actively looked for weaknesses. Pen test reports provide that evidence.
How Pen Testing Validates System Monitoring (CC7.1)
Continuous monitoring is a core SOC 2 requirement. While pen testing isn't continuous, it serves as a periodic validation that your monitoring tools are catching what they should.
If your pen tester finds a vulnerability that your best vulnerability management tools missed, that's valuable information. It tells you where to improve your ongoing monitoring.
How Pen Testing Addresses Vulnerability Management (CC7.2)
This criterion requires you to identify, evaluate, and remediate vulnerabilities on a timely basis. Penetration testing is one of the most effective ways to identify vulnerabilities that automated scanners miss.
Scanners are great for known vulnerabilities. But pen testers think like attackers. They chain together multiple small weaknesses into significant exploits. That's the kind of insight you won't get from automated tools alone.
How Pen Testing Supports Change Management (CC6.6)
When you make changes to your systems, how do you know those changes didn't introduce new vulnerabilities? Penetration testing after significant changes gives you that assurance.
Your auditor will want to see that you have a process for validating security after changes. Pen testing is a key part of that validation.
What Type of Penetration Test Do You Need for SOC 2?
Not all pen tests are created equal. The type you need depends on your infrastructure, your risk profile, and what you're trying to prove.
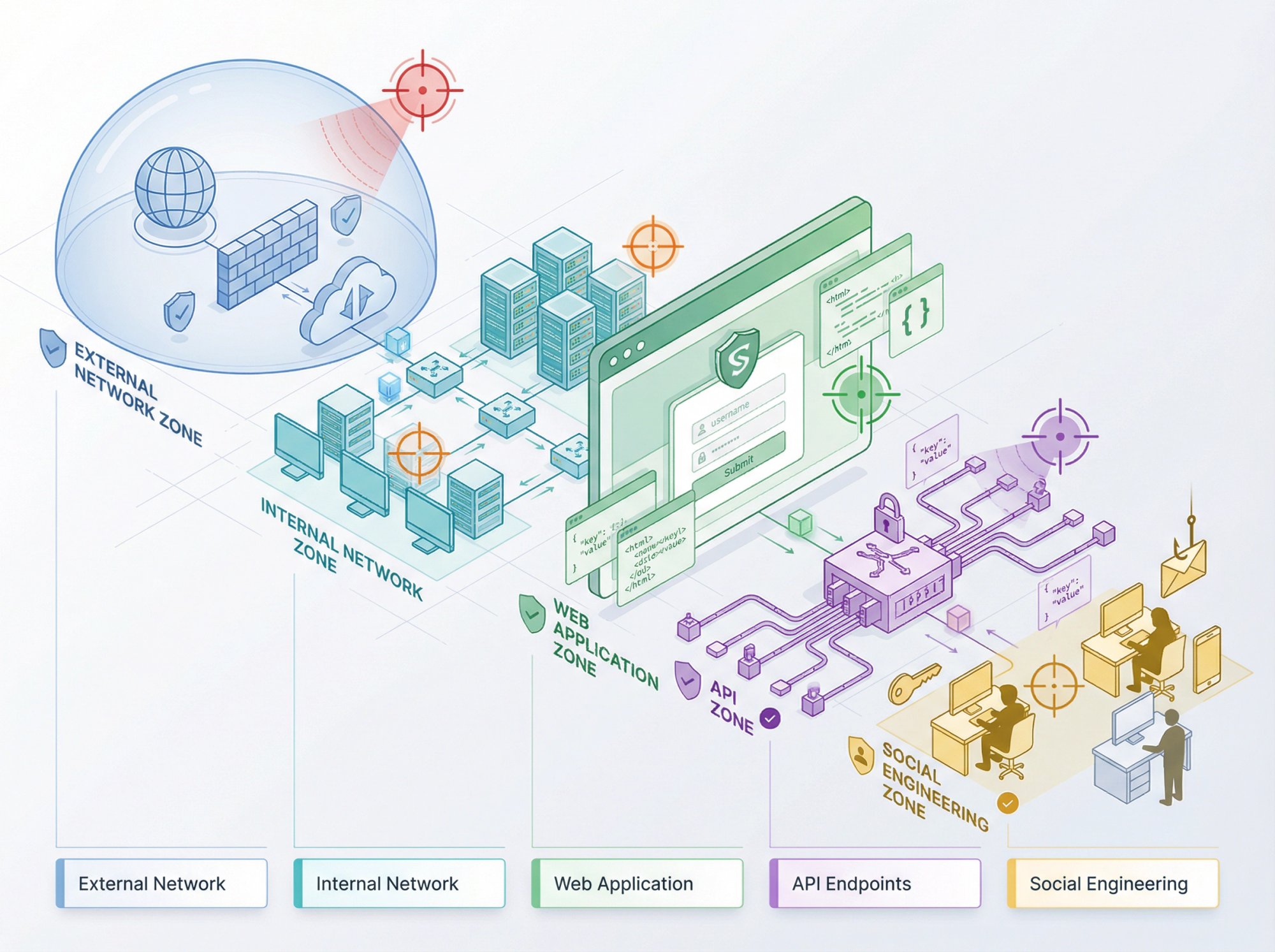
What Is External Network Penetration Testing?
This tests your internet-facing systems. If you have web applications, APIs, or any services exposed to the internet, external testing is essential.
Most startups should start here. Your external attack surface is where most real-world attacks begin.
What Is Internal Network Penetration Testing?
This simulates an attacker who's already inside your network. Maybe through a phishing attack, maybe through a compromised employee account.
Internal testing is particularly important if you handle sensitive customer data. It shows how much damage an insider (or a compromised insider) could do.
What Is Web Application Penetration Testing?
If your product is a web application (and for most SaaS companies, it is), this is non-negotiable. Web apps have their own unique vulnerabilities like injection attacks, broken authentication, and security misconfigurations.
You'll want testers who follow OWASP guidelines and can check your app against the OWASP Top 10.
What Is API Penetration Testing?
APIs are increasingly the target of choice for attackers. If your product exposes APIs, they need dedicated testing.
API security testing examines authentication, authorization, rate limiting, and data exposure. These are often overlooked in traditional web app testing.
Should You Include Social Engineering in Your Pen Test?
Phishing simulations and other social engineering tests evaluate your human defenses. SOC 2 requires security awareness training. Testing validates that training is working.
This isn't required for SOC 2, but many organizations include it for a complete picture of their security posture.
How Often Should You Conduct Penetration Tests for SOC 2?
For SOC 2 purposes, annual penetration testing is the standard expectation. But that's the minimum.
Here's a more practical approach:
Annual comprehensive testing: A full penetration test covering your entire scope at least once per year.
After major changes: Whenever you deploy significant new features, change infrastructure, or integrate new third-party services.
Quarterly or continuous for high-risk organizations: If you're handling particularly sensitive data or operating in a high-risk industry, more frequent testing makes sense.
Your auditor will want to see that your testing frequency matches your risk profile. A company handling healthcare data should test more often than a company handling public marketing content.
How to Choose a Penetration Testing Firm for SOC 2
Your SOC 2 auditor will scrutinize your pen testing methodology. Choosing the right firm matters.
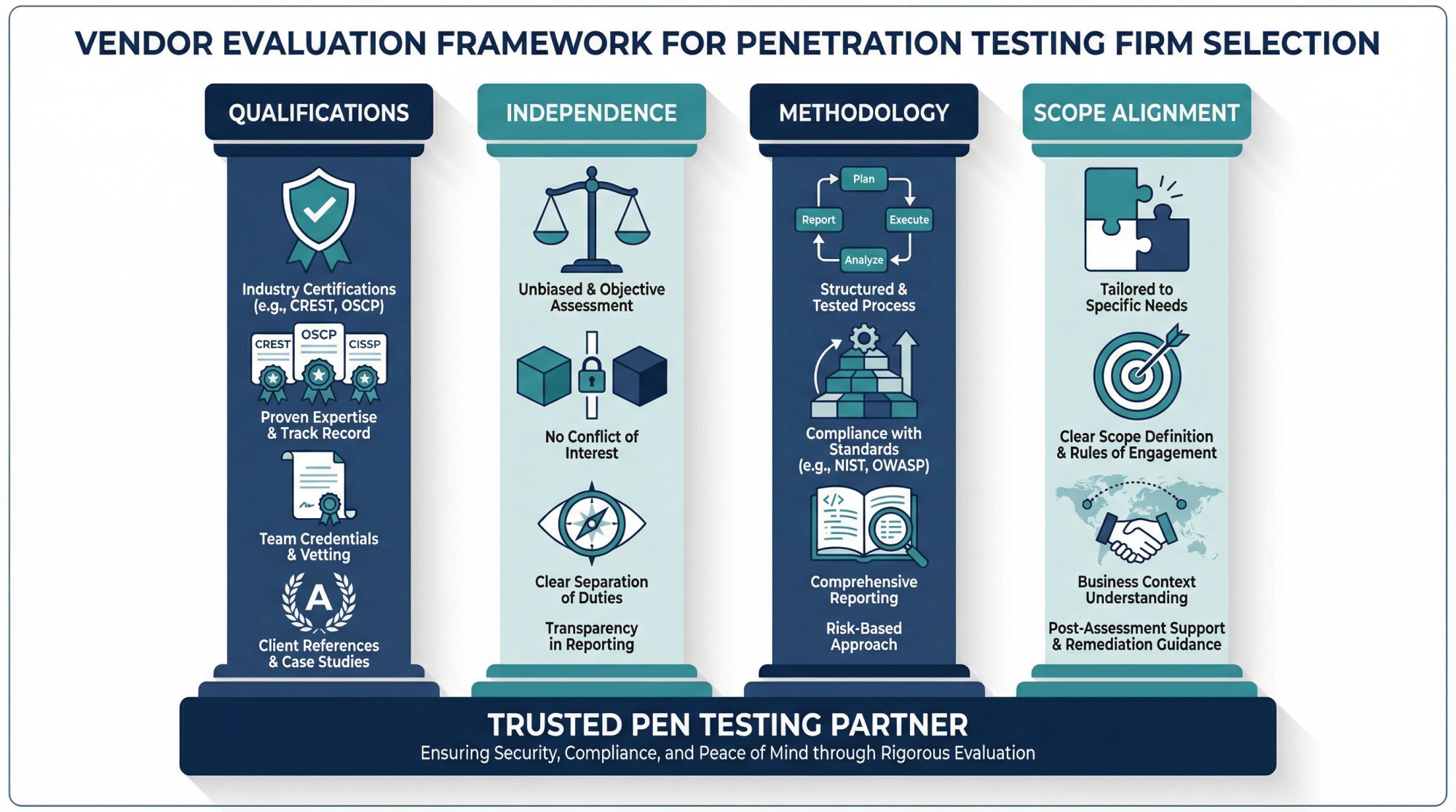
What Pen Tester Qualifications Should You Look For?
Look for testers with recognized certifications:
- OSCP (Offensive Security Certified Professional)
- GPEN (GIAC Penetration Tester)
- CEH (Certified Ethical Hacker)
- CREST certification
Certifications aren't everything, but they demonstrate baseline competency.
Why Does Pen Testing Independence Matter for SOC 2?
Your pen testing firm should be independent from your SOC 2 auditor. This isn't just best practice. It prevents conflicts of interest and ensures objectivity.
Some auditors will question findings from internal security teams. Third-party pen tests carry more weight in the audit.
What Pen Testing Methodology Should Your Firm Use?
Your pen testing firm should explain their methodology clearly. Common frameworks include:
→ PTES (Penetration Testing Execution Standard)
→ OWASP Testing Guide
→ NIST SP 800-115
Ask how they'll document findings and what deliverables you'll receive.
How to Define Pen Test Scope for SOC 2
Before testing begins, get clear agreement on scope. What systems are in bounds? What's off limits? When will testing occur?
For SOC 2, your pen test scope should align with your audit scope. If your SOC 2 covers your production environment, your pen test should too.
How to Use Pen Test Results in Your SOC 2 Audit
Your pen test report becomes evidence in your SOC 2 audit. Here's how to maximize its value.
What Documentation Do Auditors Need from Pen Tests?
Your auditor will want to see:
- The pen test report with findings and severity ratings
- Evidence that you've remediated critical and high-severity findings
- Your risk acceptance documentation for any findings you chose not to fix
- Timelines showing when testing occurred and when remediation was completed
Why Remediation Matters More Than Finding Vulnerabilities
Finding vulnerabilities is only half the equation. You must also fix them (or accept the risk with documented justification).
For SOC 2 Type II audits, auditors look at your remediation process over time. They want to see that you're not just finding issues but actually resolving them.
How to Communicate Pen Test Results with Your Auditor
Share your pen test results with your SOC 2 auditor. They may have questions about methodology, scope, or remediation.
Early communication prevents surprises. If your auditor sees critical unfixed findings during the audit, that's a problem. If they see that you found issues and remediated them promptly, that's evidence of mature security practices.
Best Penetration Testing Tools for SOC 2 Preparation
While professional pen testers bring expertise you can't replicate, there are tools you can use for internal security testing.
What Commercial Pen Testing Tools Are Available?
For vulnerability scanning and initial assessments, check out our guide to the best penetration testing tools. These tools can help you identify obvious issues before your formal pen test.
What Open Source Pen Testing Tools Can You Use?
Many pen testing teams use open source tools like:
- Nmap for network discovery
- Burp Suite Community for web app testing
- Metasploit for exploitation testing
- OWASP ZAP for automated security testing
These are great for internal teams but shouldn't replace professional pen testing for SOC 2 purposes.
5 Common Penetration Testing Mistakes to Avoid for SOC 2

We've seen companies make the same mistakes repeatedly. Here's what to watch out for.
Scheduling Your Pen Test Too Close to the Audit
Don't schedule your pen test two weeks before your SOC 2 audit. You need time to remediate findings.
Plan for at least 4 to 6 weeks between pen test completion and your audit. More if you anticipate significant findings.
Misaligning Pen Test Scope with SOC 2 Scope
If your SOC 2 scope includes your production environment and your pen test only covers your staging environment, that's a problem. Ensure alignment.
Skipping Remediation After Receiving Results
Some companies treat pen tests as checkbox exercises. They get the report, file it, and move on.
Your auditor will ask about remediation. Have clear documentation showing what you fixed and when.
Testing Only Once Instead of Annually
One pen test from three years ago won't satisfy your SOC 2 auditor. Annual testing is the expectation.
Choosing a Pen Testing Firm Based on Price Alone
The cheapest pen test often provides the least value. You want thorough testing from qualified professionals.
A cheap pen test that misses critical vulnerabilities costs you far more in the long run.
How to Integrate Pen Testing into Your SOC 2 Compliance Program
Penetration testing shouldn't exist in isolation. It's one piece of your security program.
For a complete view of what SOC 2 requires, check out our comprehensive guide to SOC 2 compliance requirements. And if you're just getting started, our SOC 2 compliance checklist walks you through every step.
How Much Does Penetration Testing Cost for SOC 2?
Penetration testing isn't free. Costs typically range from $5,000 to $50,000 or more depending on scope and complexity.
For a realistic view of total SOC 2 costs including pen testing, see our SOC 2 cost breakdown.
How to Track Pen Test Improvement Over Time
Use pen test findings to improve your security posture over time. Track metrics like:
- Number of critical findings year over year
- Time to remediation
- Findings by category
This data helps you demonstrate security maturity to auditors and customers.
How Comp AI Helps with SOC 2 Penetration Testing Requirements
Getting pen testing right for SOC 2 involves more than just hiring a firm and collecting a report. You need to document findings, track remediation, and present everything clearly to your auditor.
Comp AI streamlines this entire process. Our platform helps you:
- Track penetration testing schedules and results
- Document remediation efforts with audit-ready evidence
- Map pen test findings to relevant SOC 2 controls
- Maintain continuous compliance between audits
We've helped startups get audit-ready in hours, not months. Our AI agents handle the evidence collection and documentation so you can focus on actually fixing vulnerabilities.
Frequently Asked Questions
Is penetration testing required for SOC 2 compliance?
No, SOC 2 doesn't explicitly require penetration testing. However, it's strongly recommended and most auditors expect to see evidence of security testing. Pen testing helps satisfy the Trust Services Criteria related to risk assessment (CC3.2), vulnerability management (CC7.2), and ongoing monitoring (CC7.1).
How often should I conduct penetration tests for SOC 2?
Annual penetration testing is the standard expectation for SOC 2 compliance. You should also consider additional testing after major infrastructure changes, significant new feature deployments, or third-party integrations that affect your security posture.
What's the difference between penetration testing and vulnerability scanning?
Vulnerability scanning uses automated tools to identify known security weaknesses. Penetration testing goes deeper by using human testers who think like attackers to find and exploit vulnerabilities that scanners might miss. For SOC 2, both are valuable, but pen testing provides more comprehensive validation of your security controls.
How much does a penetration test cost for SOC 2?
Penetration testing costs typically range from $5,000 to $50,000 depending on scope and complexity. Basic external network tests for small startups start around $5,000, while comprehensive testing of complex applications and infrastructure can reach $30,000 or more.
When should I schedule my penetration test before a SOC 2 audit?
Plan for at least 4 to 6 weeks between pen test completion and your SOC 2 audit. This gives you time to remediate any findings and document your remediation efforts, which auditors will want to see.
Do I need a third-party firm for penetration testing?
While not strictly required, third-party penetration testing carries more weight with SOC 2 auditors than internal testing. Independent testers provide objective assessment and their reports serve as stronger evidence of security validation.
What should be included in the scope of a SOC 2 penetration test?
Your pen test scope should align with your SOC 2 audit scope. This typically includes external network testing, web application testing, API testing, and potentially internal network testing if you handle sensitive customer data. Cloud infrastructure should also be included if relevant.
How do I present penetration test results to my SOC 2 auditor?
Provide your auditor with the complete pen test report, evidence of remediation for critical and high-severity findings, risk acceptance documentation for any unresolved issues, and timelines showing when testing and remediation occurred. Early communication prevents surprises during the audit.
Penetration testing is essential for meaningful SOC 2 compliance. While it's not technically required, it's the best way to validate your security controls and demonstrate due diligence to auditors and customers.
If you're preparing for SOC 2 and want to ensure your penetration testing approach will satisfy your auditor, book a demo with our team. We'll show you how to integrate pen testing into a streamlined compliance program that gets you audit-ready fast.
Share this article
Help others discover this content